WannaCry Ransomware Analysis
BossFight: WannaCry Ransomware Analysis
Introduction
WannaCry is a ransomware worm that spread rapidly through across a number of computer networks in May of 2017. After infecting a Windows computer, it encrypts files on the PC’s hard drive, making them impossible for users to access, then demands a ransom payment in bitcoin in order to decrypt them.
SHA256 File Hash
WannaCry.exe -> 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
Basic Static Analysis
Strings
When running command as strings or floss you will get large number of strings so I’ll put the most important first :-
!This program cannot be run in DOS mode. (appeared more than one which means there are embedded EXEs)
SizeofResource
LockResource
LoadResource
FindResourceA
CreateProcessA
mssecsvc.exe
\\192.168.56.20\IPC$
C:\%s\qeriuwjhrf
tasksche.exe
WriteFile
CreateFileA
CreateProcessA
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
RegCloseKey
RegQueryValueExA
RegSetValueExA
RegCreateKeyW
CryptReleaseContext
CreateServiceA
CloseServiceHandle
StartServiceA
OpenServiceA
OpenSCManagerA
RegCloseKey
RegQueryValueExA
RegSetValueExA
RegCreateKeyW
CryptReleaseContext
CreateServiceA
CloseServiceHandle
StartServiceA
OpenServiceA
OpenSCManagerA
WanaCrypt0r
WANACRY!
msg/m_bulgarian.wnry
msg/m_chinese (simplified).wnry
msg/m_chinese (traditional).wnry
msg/m_croatian.wnry
msg/m_czech.wnry
msg/m_danish.wnry
msg/m_dutch.wnry
msg/m_english.wnry
....
For sure there are still more strings found but I’m satisfied with this for now. Looks like it is going to connect to the URL http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com but still we don’t know why for now. Also it is going to create some files and service and will add registry value. The Malware has embedded EXEs.
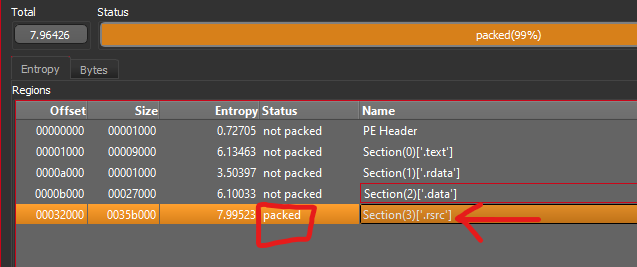
So thats enough with the basic static analysis lets start in the basic dynamic analysis
Basic Dynamic Analysis
Lets run the malware without connecting to InetSim :-
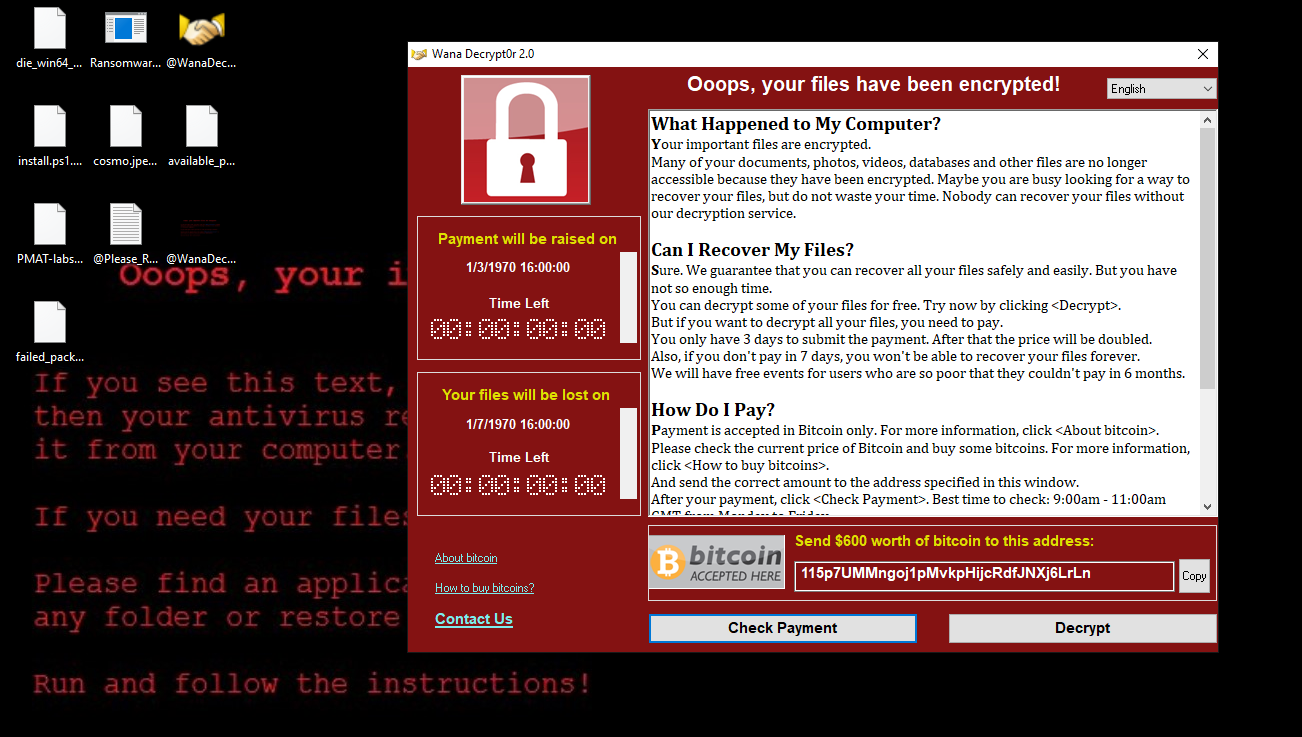
As you can see it changed the background dropped EXEs and encrypted all files and add .WNCRY extension. Also the malware dropped readme text
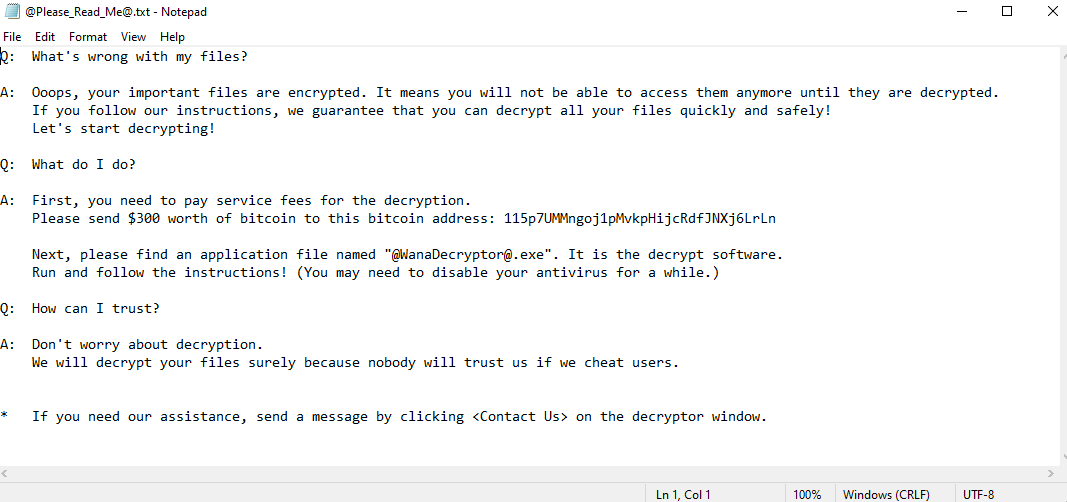
ReadMe Text
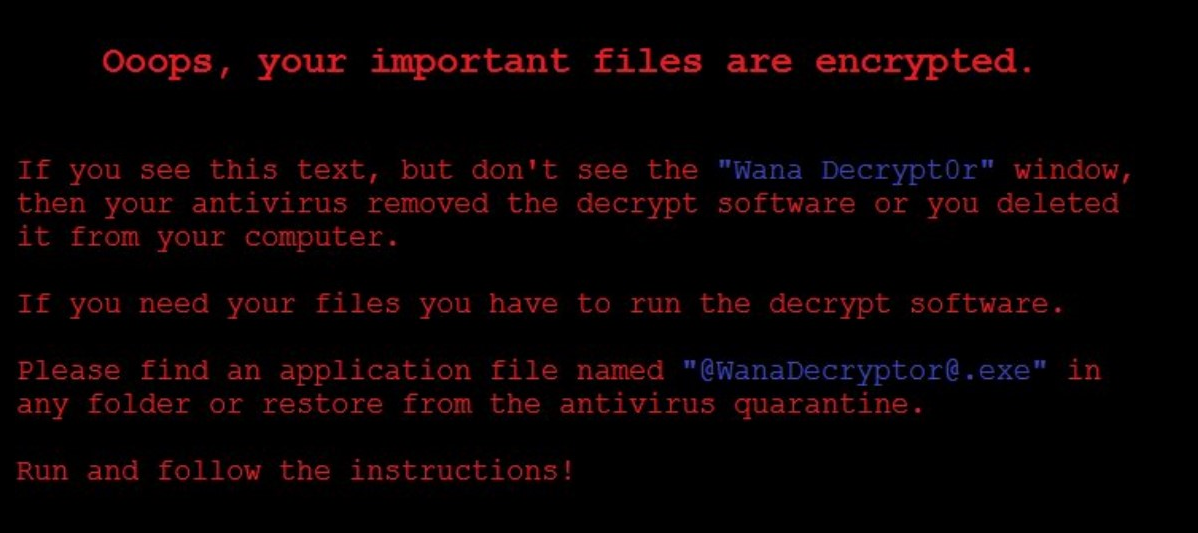
Now Lets open InetSim to simulate network and analyze traffic by wireshark :-
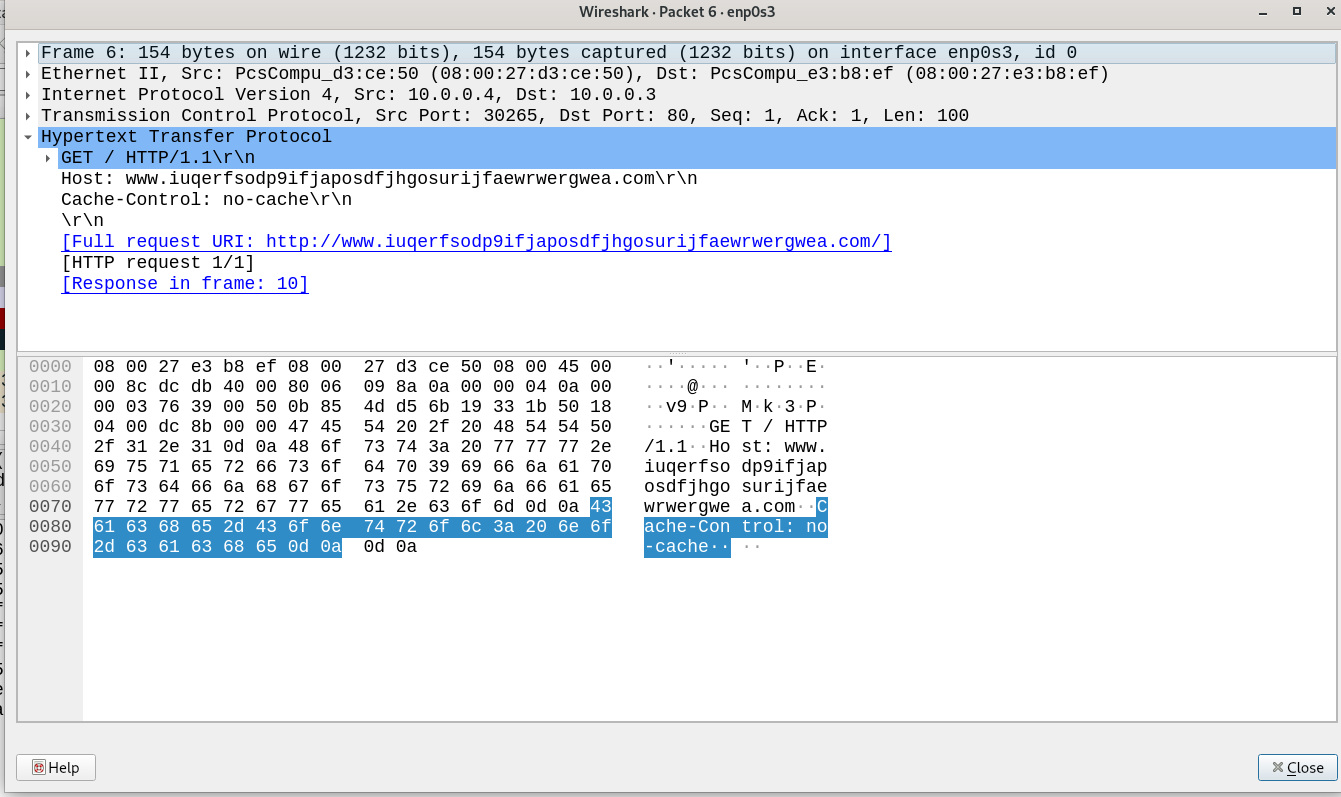
The malware sent request to http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com and it was successful. But the most weird thing that the ransomware terminated directly after that. Looks like it is checking if it is being monitored by a tool like InteSim.
After understanding how WannaCry works lets dive into more detailed analysis while running it. I will use ProcMon to trace WannaCry EXE :-
- so wannacry EXE will create a child process called tasksche.exe
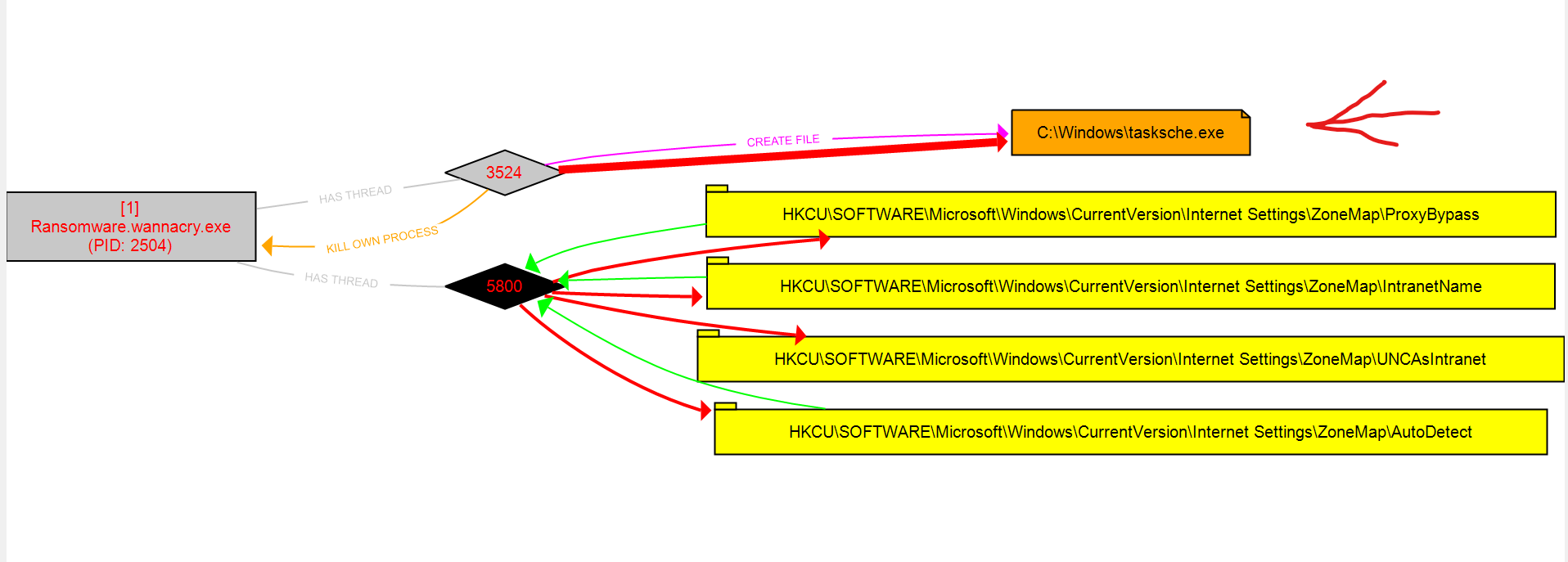
Lets trace the child process :-
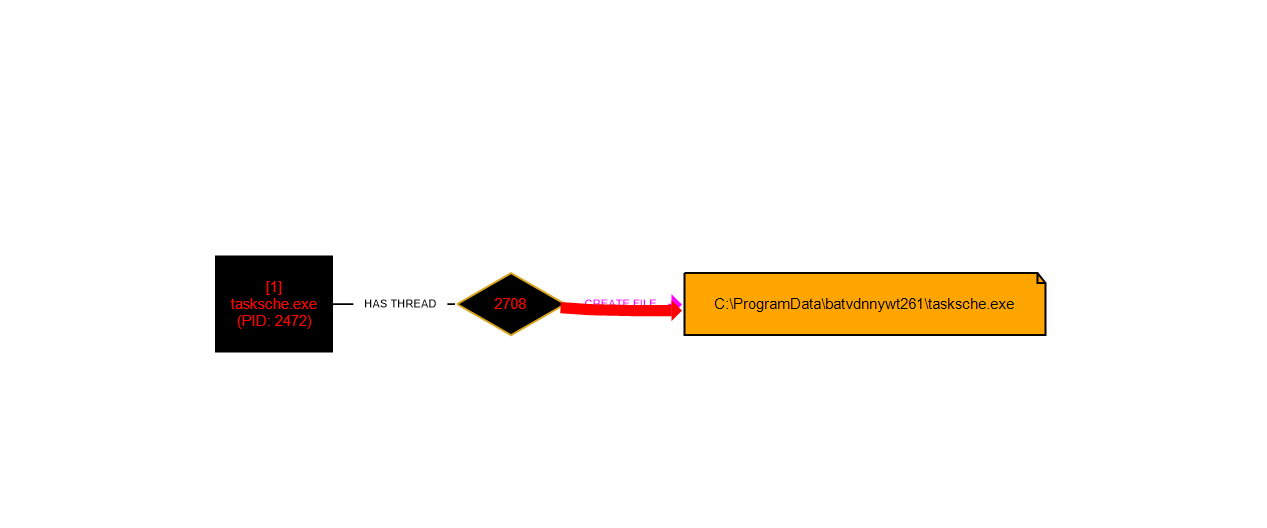
It created a directory with random name also it created a service with the same name which will be responsible for persistence.
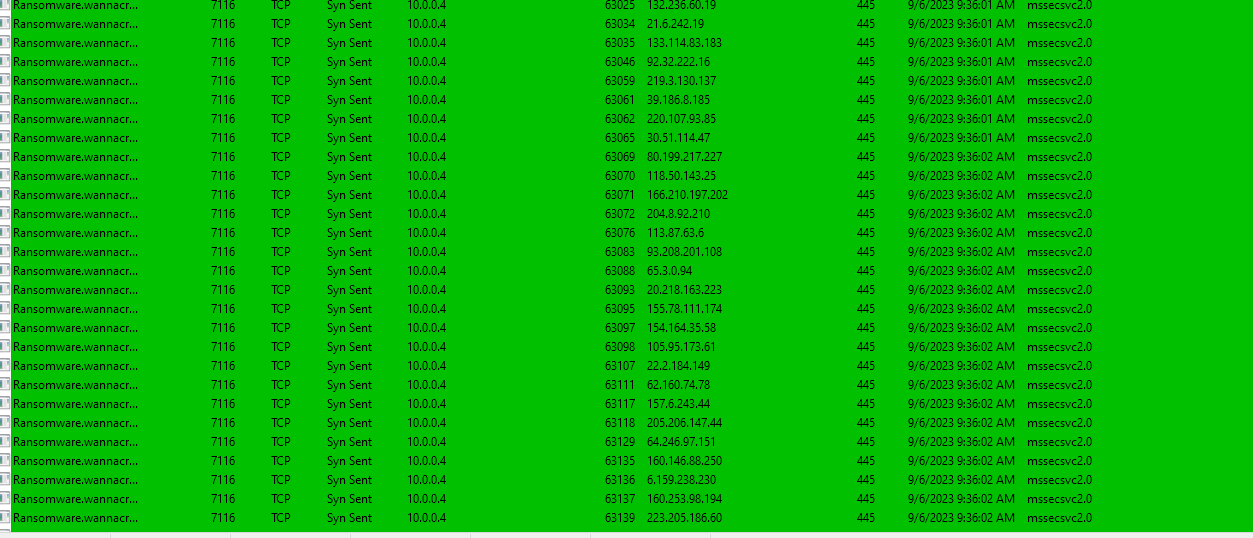
By using TCPView we could see that WannaCry is trying to exploit the vulnerability found in SMB protocol (port 445)
- What is SMB ?!
- Server Message Block (SMB) is a file sharing protocol that allows Windows systems connected to the same network or domain to share files. SMB also enables computers to share printers and serial ports from other computers within the same network.
- Vulnerability in SMB version 1.0
Advanced Analysis
So lets load the Malware into IDA. As we can see here it checks the if the connection to that weird URL is successful or not :-
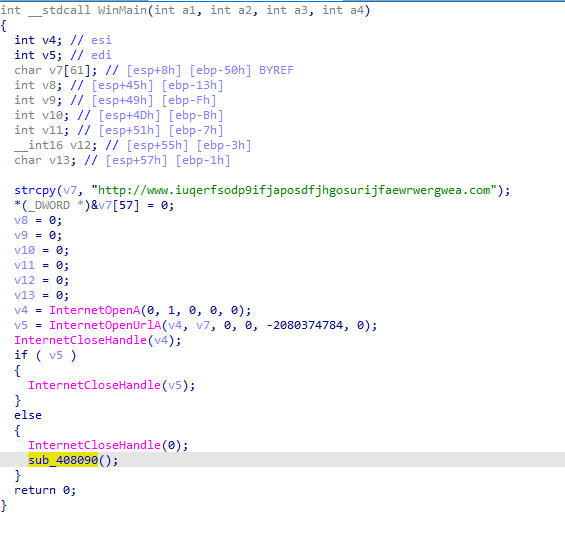
If the request is not Successful which means it is not being monitored or using InetSim it will call sub_408090 function :-
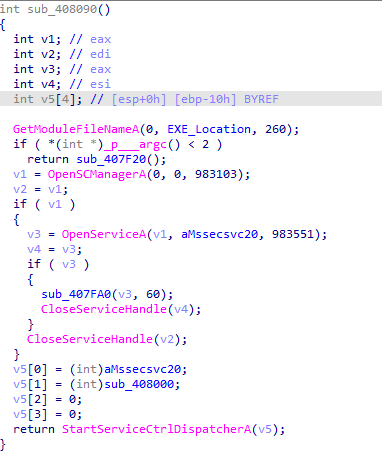
As we can see first of all it will get EXE location by using GetModuleFileNameA in my case it is Desktop so the return value will be “C:\Desktop\WanaCry.exe” for example then it will check that we run the EXE with no arguments by using p__argc() function if so it will call sub_407F20() which has two functions inside :-
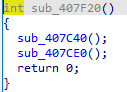
The first Function sub_407C40() creates a service for the binary “WannaCry.exe -m security” which will run same EXE but with some arguments
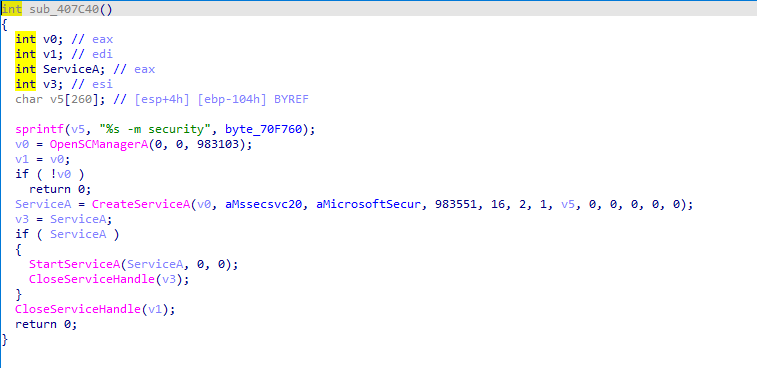
The seconde Function sub_407CE0() is responsible for dumping the embedded EXE in the resource section to file named tasksche.exe
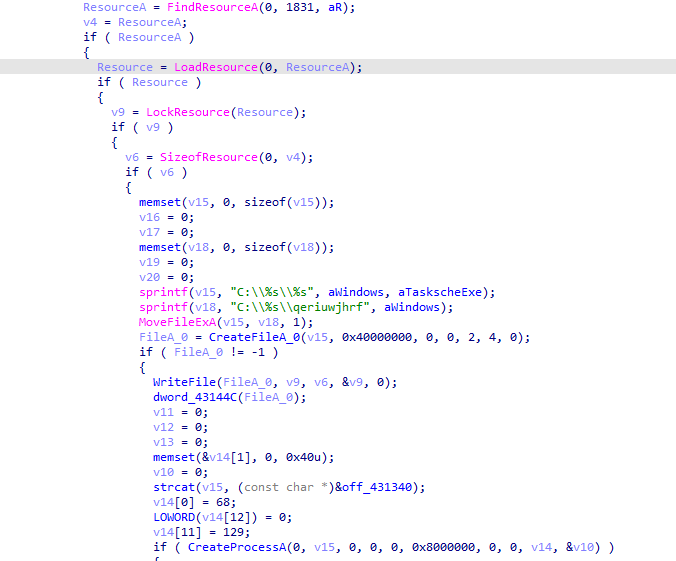
After creating the file at C:\Windows\tasksche.exe it will execute it by CreateProcessA.
I will stop here for now maybe in future “In Sha Allah” I will dive into more detailed analysis.
The end of WannaCry
WannaCry was the biggest ransomware attack in history it was diffrent than any other ransomeware as it could spread through the local network by its own by exploiting the SMB Vulnerability. But a kill switch was discovered by British security researcher Marcus Hutchins, who stopped the attack by registering the web domain found in the malware’s code. As we said above that WannaCry checks if the connection is successful this means it is being moniterd so it terminates.
Challenge Questions
- Record any observed symptoms of infection from initial detonation. What are the main symptoms of a WannaCry infection?
- First of all the malware will not work if it could reach http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- It starts by dropping all the embedded EXEs and files
- Start encrypting the files
- change the background
- then opens WannaCry decryptor
- Use FLOSS and extract the strings from the main WannaCry binary. Are there any strings of interest?
- http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- msg/m_bulgarian.wnry ….
- tasksche.exe
- WanaCrypt0r
- WANACRY!
- icacls . /grant Everyone:F /T /C /Q
- Inspect the import address table for the main WannaCry binary. Are there any notable API imports?
- There are lots of interesting APIs as :-
- CreateServiceA
- CryptReleaseContext and all crypto APIs
- InternetOpenA
- InternetOpenUrl
- There are lots of interesting APIs as :-
- What conditions are necessary to get this sample to detonate?
- If the connection to http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com succeed the malware will not work
- If it didn’t succeed the malware will work
- This mechanism is used to detect tools as inetsim
- Network Indicators: Identify the network indicators of this malware
- http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
- A lot of SMB connection requests
- Host-based Indicators: Identify the host-based indicators of this malware.
- tasksche.exe
- A directory is going to be created at C:\ProgramData with random name
- service is going to be created with the same of the directory
- Use Cutter to locate the killswitch mechanism in the decompiled code and explain how it functions.

- If the connection is successful it will exit else the malware will execute fine.
I wish you enjoyed the analysis. If you have any comment or any thing to add don’t hesitate to contact me.
Yara Rule
rule wannacry
{
meta:
author = "Mohammed Gabr"
description = "WannaCry Strings"
strings:
$str_1 = "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com" ascii
$str_2 = "WanaCrypt0r"
$str_3 = "WANACRY!"
$str_4 = "msg/m_english.wnry"
$str_5 = "tasksche.exe"
$str_8 = "msg/m_bulgarian.wnry"
$str_9 = "msg/m_chinese (simplified).wnry"
$str_10 = "msg/m_chinese (traditional).wnry"
$str_11 = "msg/m_croatian.wnry"
$str_12 = "msg/m_czech.wnry"
$str_13 = "msg/m_danish.wnry"
$str_14 = "msg/m_dutch.wnry"
$str_15 = "msg/m_english.wnry"
$str_16 = "@WanaDecryptor@.exe"
condition:
any of them
}
Hope you enjoyed reading. If you have any comment or any thing to add don’t hesitate contact me.
Reference
- https://portswigger.net/daily-swig/marcus-hutchins-on-halting-the-wannacry-ransomware-attack-still-to-this-day-it-feels-like-it-was-all-a-weird-dream
- https://cyware.com/news/what-is-smb-vulnerability-and-how-it-was-exploited-to-launch-the-wannacry-ransomware-attack-c5a97c48
