Chapter 3 : Basic Dynamic Analysis
Chapter 3 : Basic Dynamic Analysis
Note :-
I,m going to use Windows XP for dynamic analysis as most of the labs are designed for Windows XP
Tools
string/floss -> to get the strings of the binary. Floss gets the stack strings too.
file -> to get general info about EXE as architecture
PeID -> to find if it is packed or not
InetSim -> to simulate the internet connection
WireShark -> to analyze traffic
Lab 1
SHA256 File Hash
Lab03-1 -> EB84360CA4E33B8BB60DF47AB5CE962501EF3420BC7AAB90655FD507D2FFCEDD
ARCH -> 32 bit
Basic Static Analysis
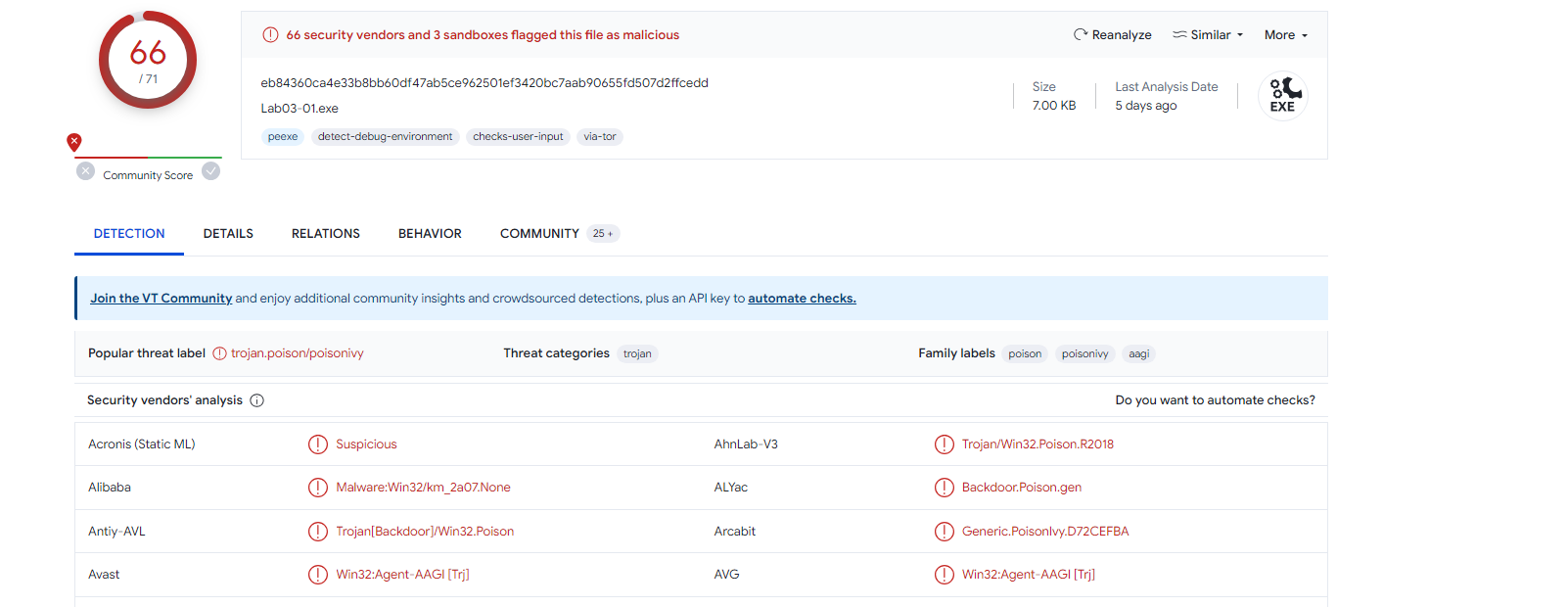
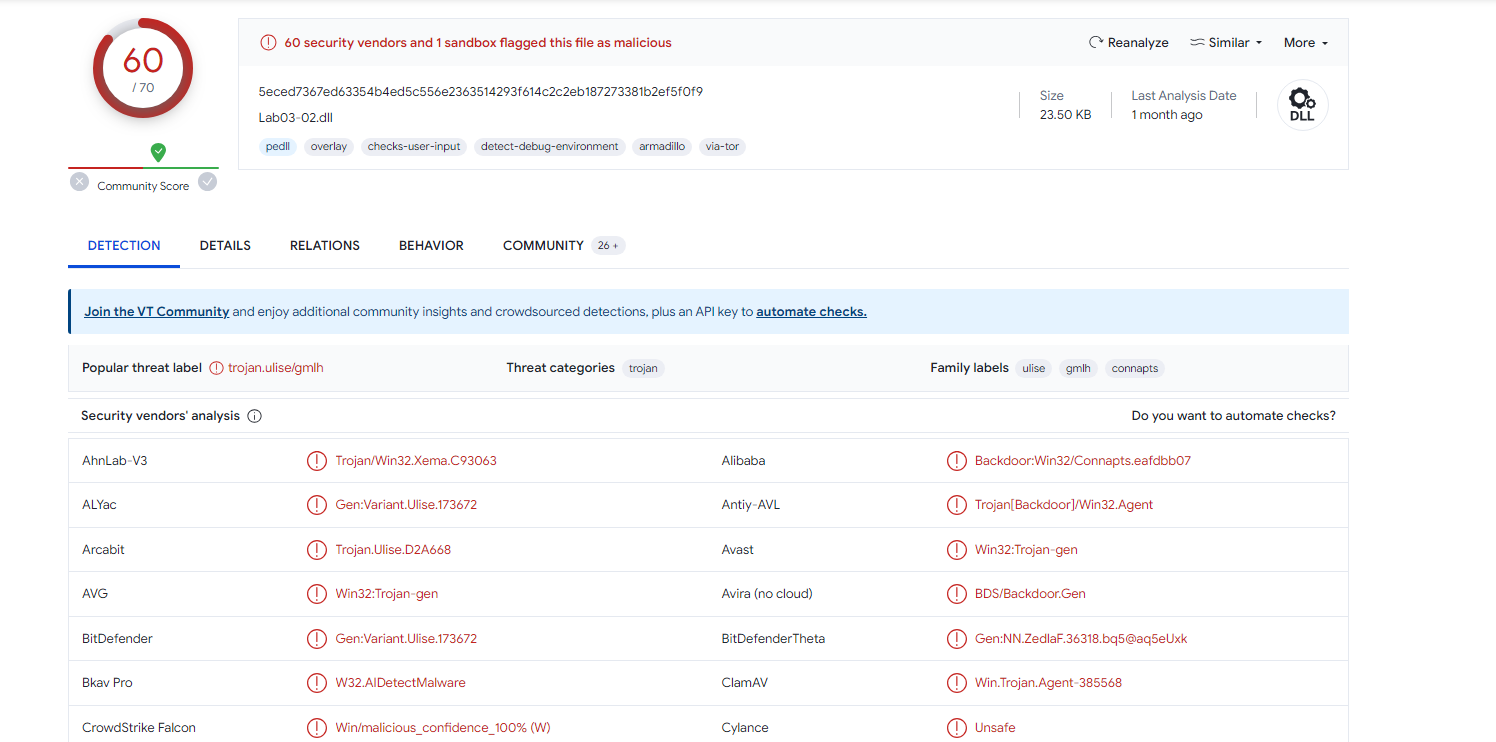
VirusTotal
Looks like it is Malicious as shown below :-
Strings
ExitProcess
kernel32.dll
ws2_32
CONNECT %s:%i HTTP/1.0
StubPath
SOFTWARE\Classes\http\shell\open\commandV
Software\Microsoft\Active Setup\Installed Components\
test
www.practicalmalwareanalysis.com
admin
VideoDriver
WinVMX32-
vmx32to64.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
AppData
So looks like it is going to connect to www.practicalmalwareanalysis.com url and download 2nd stage EXE which is vmx32to64.exe or maybe it is going to exfiltrate data (this is just a guess). Also looks like it is going to persist it self by using SOFTWARE\Microsoft\Windows\CurrentVersion\Run REG key. I think it is packed as there are few strings actually only one import from kernel32.dll which is ExitProcess. To understand whats is Software\Microsoft\Active Setup\Installed Components\ we need to know what is Active Setup :-
-
Active Setup is a mechanism for executing commands once per user early during logon. Active Setup is used by some operating system components like Internet Explorer to set up an initial configuration for new users logging on for the first time.
-
“StubPath” entry stores the command that needs to be executed by the Active setup process.
There is some interesting strings but still we don’t know what is the malware going to uses this REG keys for.
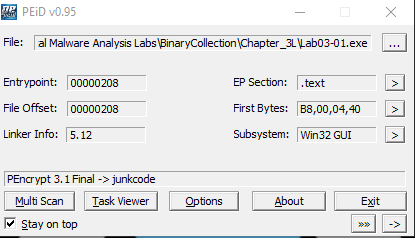
Packed
After using PeID it showed us that it is packed using PEncrypt 3.1 Final -> junkcode
I think thats enough for Basic Static Analysis. Let’s start Basic Dynamic Analysis.
Basic Dynamic Analysis
Note :-
I had an error while running the program in windows 10 so I used windows xp as most of the labs in the book are designed for Windows XP
So started InetSim in my Remnux Machine and WireShark to intercept the traffic now we are ready lets run the Malware :-
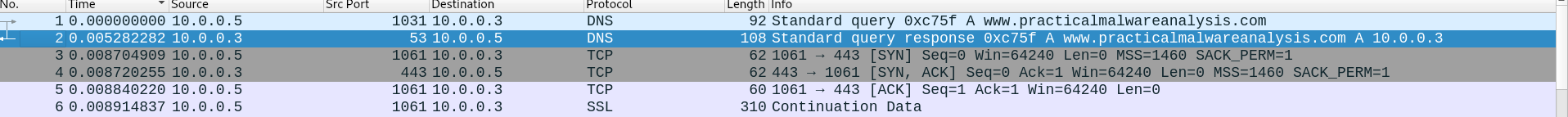
As we can see it is sending data over HTTPS (SSL) to www.practicalmalwareanalysis.com so lets see what it is sending by viewing the SSL protocol captured :-
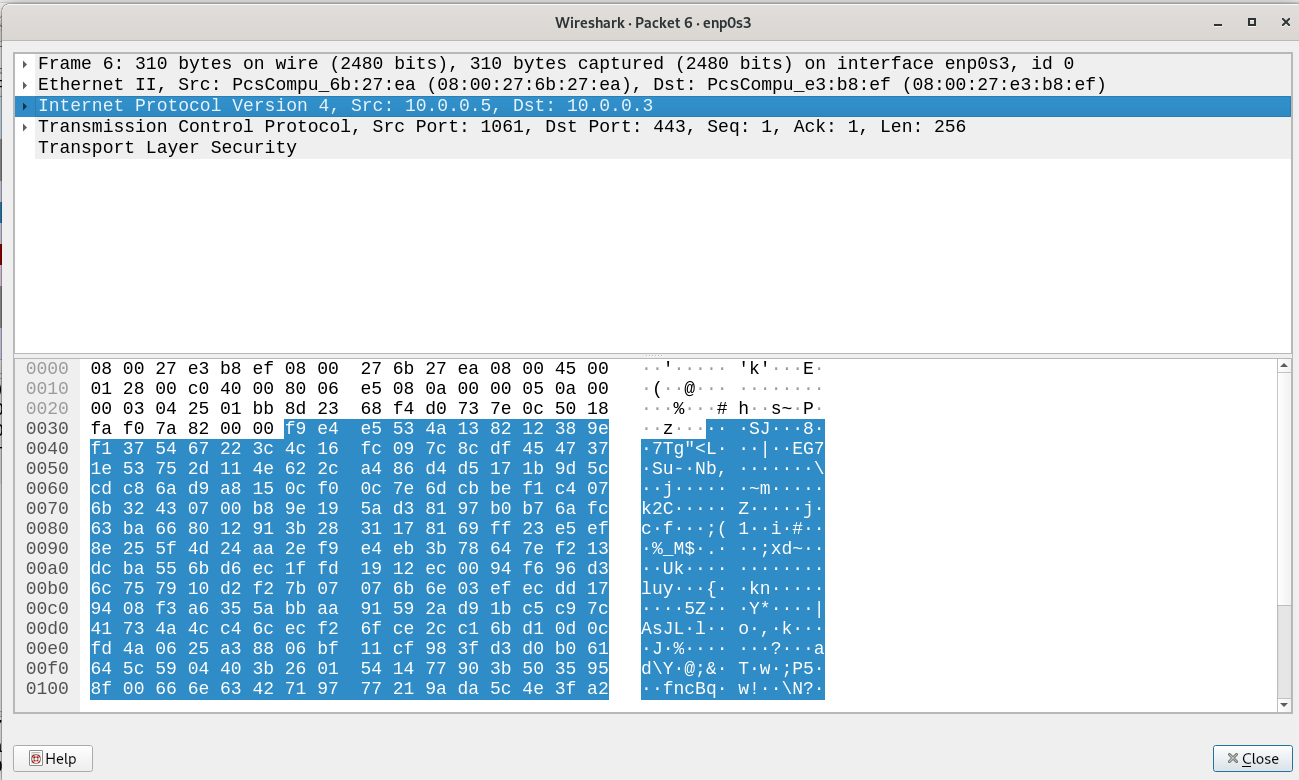
Looks like it sending random things or maybe using encryption to exfiltrate data and make it unreadable.Also looks like there is a loop for sending data as every few seconds it repeats the process.
lets use procmon to see if it created or add REG key I used WriteFile and RegSetValue as a filter :-
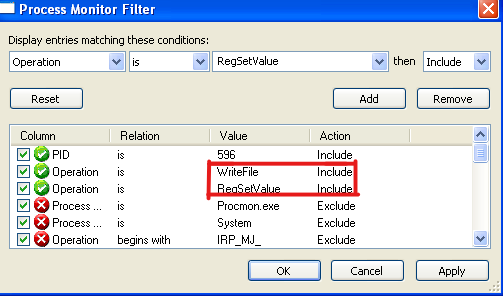
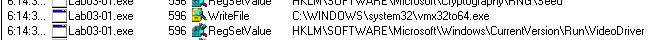
As we can see it created an EXE c:\windows\system32\vmx32to64.exe and add a REG Key SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoDriver which is used for persistance.
Note :-
Run VS RunOnce :-
- Run makes the program run every time the user logs on.
- RunOnce makes the program run one time, and then the key is deleted.
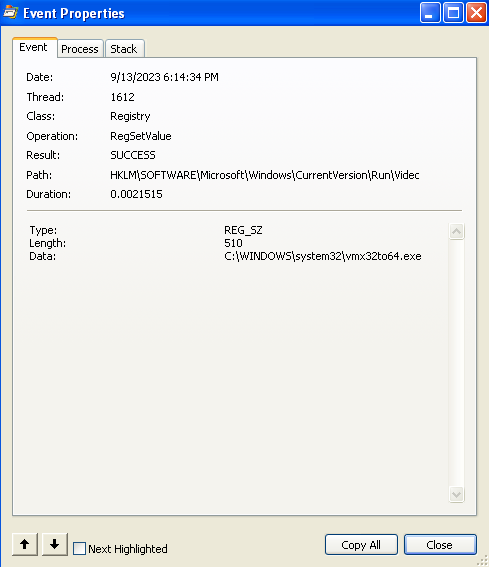
So it will run vmx32to64.exe every time the user logs on
But why dose the malware creates EXE (vmx32to64.exe) and whats it’s SHA256?!
SHA256 Hash
vmx32to64.exe -> EB84360CA4E33B8BB60DF47AB5CE962501EF3420BC7AAB90655FD507D2FFCEDD
Lab03-01.exe -> EB84360CA4E33B8BB60DF47AB5CE962501EF3420BC7AAB90655FD507D2FFCEDD
It created this EXE to copies itself to vmx32to64.exe to use the new EXE for the persistance as shown above
I used ProcExp and found that it created a mutex WinVMX32
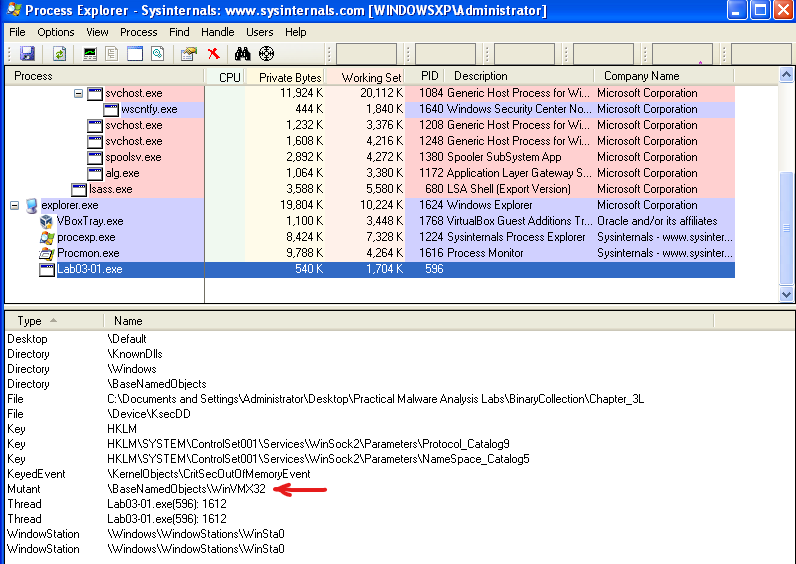
I think thats enough for basic static and dynamic analysis.
Questions
- What are this malware’s imports and strings?
- we have only one import form kernel32.dll which is ExitProcess
- strings as shown above
- What are the malware’s host-based indicators?
- creating EXE -> vmx32to64.exe
- Mutex -> WinVMX32
- REG kry -> SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoDriver
- Are there any useful network-based signatures for this malware? If so, what are they?
- www.practicalmalwareanalysis.com
Lab 2
SHA256 File Hash
Lab03-2.dll -> 5eced7367ed63354b4ed5c556e2363514293f614c2c2eb187273381b2ef5f0f9
ARCH -> 32 bit (DLL)
Basic Static Analysis
VirusTotal
Looks like it is Malicious as shown below :-
strings
GetModuleFileNameA
Sleep
TerminateThread
WaitForSingleObject
GetSystemTime
CreateThread
GetProcAddress
LoadLibraryA
GetLongPathNameA
GetTempPathA
ReadFile
CloseHandle
CreateProcessA
GetStartupInfoA
CreatePipe
GetCurrentDirectoryA
GetLastError
lstrlenA
SetLastError
OutputDebugStringA
KERNEL32.dll
RegisterServiceCtrlHandlerA
RegSetValueExA
RegCreateKeyA
CloseServiceHandle
CreateServiceA
OpenSCManagerA
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
DeleteService
OpenServiceA
SetServiceStatus
ADVAPI32.dll
WSASocketA
WS2_32.dll
InternetReadFile
HttpQueryInfoA
HttpSendRequestA
HttpOpenRequestA
InternetConnectA
InternetOpenA
InternetCloseHandle
WININET.dll
Lab03-02.dll
Install
ServiceMain
UninstallService
installA
uninstallA
Y29ubmVjdA==
practicalmalwareanalysis.com
serve.html
Windows XP 6.11
CreateProcessA
kernel32.dll
.exe
GET
HTTP/1.1
%s %s
1234567890123456
quit
exit
getfile
cmd.exe /c
There are lots of interesting imports and strings looks like it is going communicate with practicalmalwareanalysis.com over HTTP and it will create RegKeys.Until now it just some guess from the strings and imports.What is the name of the service that is going to be created and what is its job ?!
We will discover all of this in Dynamic Analysis
There is one important thing we need to analysis for DLLs which is the Exports Function
Install
ServiceMain
UninstallService
installA
uninstallA
So looks like that install/installA is what we are looking for looks like thats the function install/installA that is going to create the service we will try this in dynamic analysis.
Packed or Not
I don’t think it is packed but lets check PeID,EXE Info and DIE :-
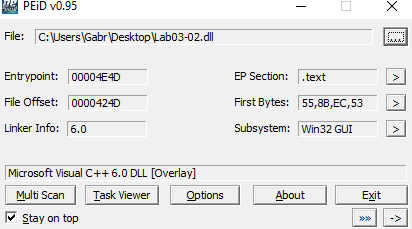
PeID and other tools didn’t detect that it is packed.
Thats enough for Basic Static Analysis.
Basic Dynamic Analysis
My Remnux machine is ready and I’ve opened InetSim and WireShark we are ready to run the mal… BUT WAIT IT IS DLL HOW TO RUN DLL ?!!!

We are going to use rundll32.exe. How to use it ?!
rundll32.exe DLLname, Export arguments
Thats why the most important in dll is to analyze the Export functions
so lets try to run the exported function installA or Install in Lab03-2.dll without any arguments . Lets see what is going to happen but before running lets take snapshot of the registry by RegShot or you can just trace the process by procmon :-
Install didn’t work so lets try installA
rundll32.exe Lab03-2.dll, installA
Actually it created a new service IPRIP.RegShot output:-
----------------------------------
Keys added: 6
----------------------------------
HKLM\SYSTEM\ControlSet001\Services\IPRIP
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Parameters
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Security
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Parameters
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Security
----------------------------------
Values added: 20
----------------------------------
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Type: 0x00000020
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Start: 0x00000002
HKLM\SYSTEM\ControlSet001\Services\IPRIP\ErrorControl: 0x00000001
HKLM\SYSTEM\ControlSet001\Services\IPRIP\ImagePath: "%SystemRoot%\System32\svchost.exe -k netsvcs"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\DisplayName: "Intranet Network Awareness (INA+)"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\ObjectName: "LocalSystem"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Description: "Depends INA+, Collects and stores network configuration and location information, and notifies applications when this information changes."
HKLM\SYSTEM\ControlSet001\Services\IPRIP\DependOnService: 52 70 63 53 73 00 00
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Parameters\ServiceDll: "C:\Documents and Settings\Administrator\Desktop\Lab03-02.dll"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Security\Security: 01 00 14 80 90 00 00 00 9C 00 00 00 14 00 00 00 30 00 00 00 02 00 1C 00 01 00 00 00 02 80 14 00 FF 01 0F 00 01 01 00 00 00 00 00 01 00 00 00 00 02 00 60 00 04 00 00 00 00 00 14 00 FD 01 02 00 01 01 00 00 00 00 00 05 12 00 00 00 00 00 18 00 FF 01 0F 00 01 02 00 00 00 00 00 05 20 00 00 00 20 02 00 00 00 00 14 00 8D 01 02 00 01 01 00 00 00 00 00 05 0B 00 00 00 00 00 18 00 FD 01 02 00 01 02 00 00 00 00 00 05 20 00 00 00 23 02 00 00 01 01 00 00 00 00 00 05 12 00 00 00 01 01 00 00 00 00 00 05 12 00 00 00
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Type: 0x00000020
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Start: 0x00000002
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\ErrorControl: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\ImagePath: "%SystemRoot%\System32\svchost.exe -k netsvcs"
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\DisplayName: "Intranet Network Awareness (INA+)"
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\ObjectName: "LocalSystem"
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Description: "Depends INA+, Collects and stores network configuration and location information, and notifies applications when this information changes."
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\DependOnService: 52 70 63 53 73 00 00
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Parameters\ServiceDll: "C:\Documents and Settings\Administrator\Desktop\Lab03-02.dll"
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Security\Security: 01 00 14 80 90 00 00 00 9C 00 00 00 14 00 00 00 30 00 00 00 02 00 1C 00 01 00 00 00 02 80 14 00 FF 01 0F 00 01 01 00 00 00 00 00 01 00 00 00 00 02 00 60 00 04 00 00 00 00 00 14 00 FD 01 02 00 01 01 00 00 00 00 00 05 12 00 00 00 00 00 18 00 FF 01 0F 00 01 02 00 00 00 00 00 05 20 00 00 00 20 02 00 00 00 00 14 00 8D 01 02 00 01 01 00 00 00 00 00 05 0B 00 00 00 00 00 18 00 FD 01 02 00 01 02 00 00 00 00 00 05 20 00 00 00 23 02 00 00 01 01 00 00 00 00 00 05 12 00 00 00 01 01 00 00 00 00 00 05 12 00 00 00
Also by using procmon after using RegSetValue as a filter we can see that it created IPRIP service :-
Note :-
you can use RegCreateKey and you will see that it created the **IPRIP** service
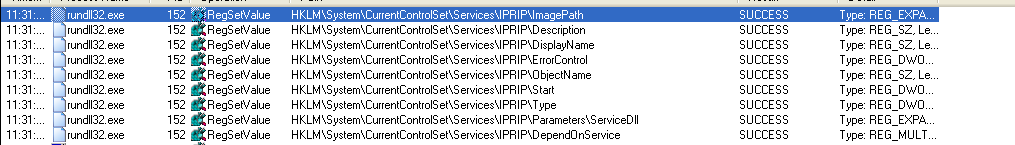
Lets try to start the service and see what is going to happen using :-
net start IPRIP
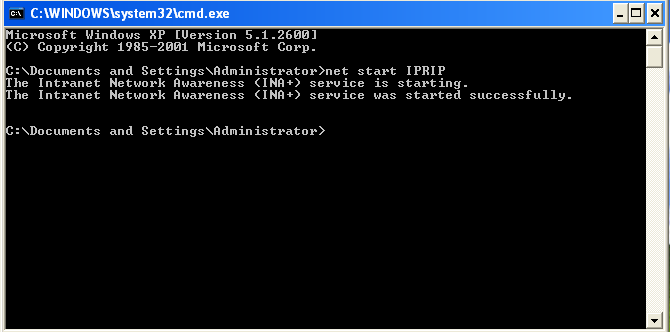
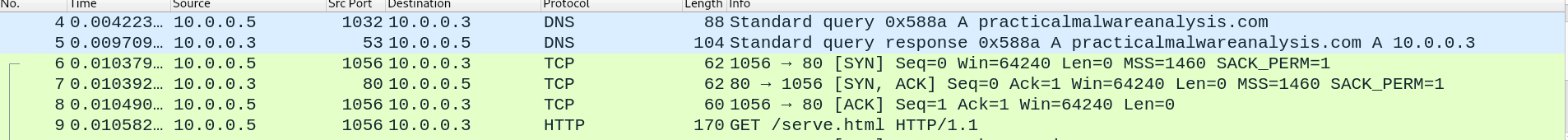
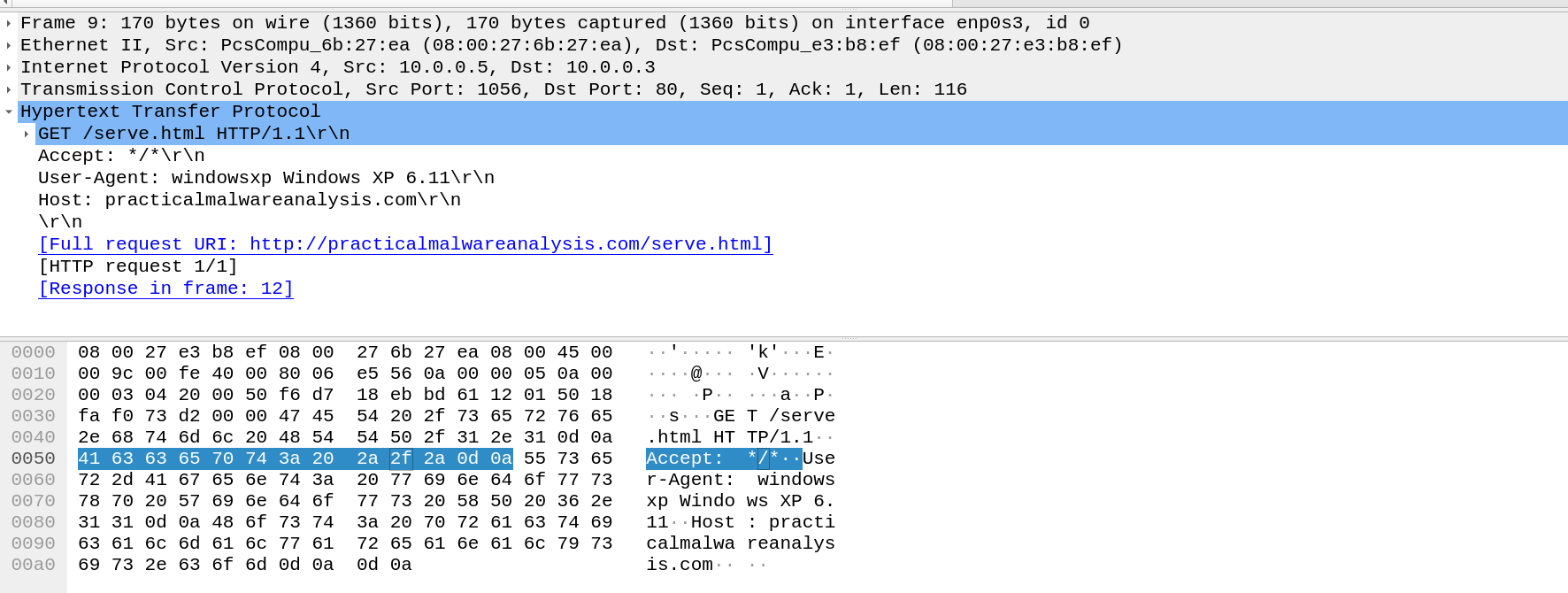
After few seconds we saw HTTP request to http://practicalmalwareanalysis.com/serve.html
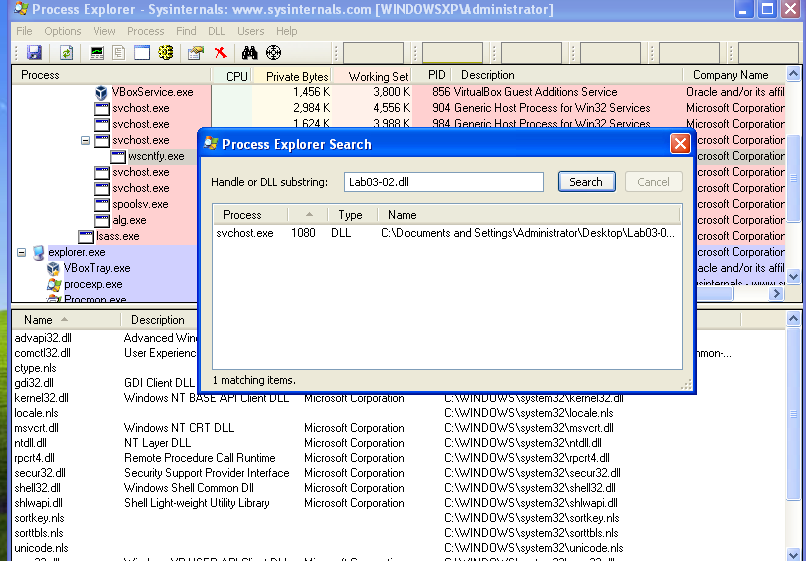
The question I asked my self How can I get the service ID that I’ve just started?!
So I used ProcExp then clicked Find and searched by the name of the DLL Lab03-2.dll :-
Questions
- How can you get this malware to install itself?
- After analyzing the Exports of the DLL we can find a function called installA which seems to install something later we found that it creates service :-
- rundll32.exe Lab03-2.dll, installA
- After analyzing the Exports of the DLL we can find a function called installA which seems to install something later we found that it creates service :-
- How would you get this malware to run after installation?
- We started the service by :-
- net start IPRIP
- We started the service by :-
- How can you find the process under which this malware is running?
- I used ProcExp then clicked Find and searched by the name of the DLL Lab03-2.dll
- Which filters could you set in order to use procmon to clean information?
- RegSetValue you can use also RegCreateKey
- What are the malware’s host-based indicators?
- it creates a service named IPRIP
- Are there any useful network-based signatures for this malware?
- http://practicalmalwareanalysis.com/serve.html
Lab 3
SHA256 Hash
Lab03-03.exe -> ae8a1c7eb64c42ea2a04f97523ebf0844c27029eb040d910048b680f884b9dce
Architecture -> 32 bit
Basic Static Analysis
VirusTotal
Looks like it is Malicious as shown below :-
Strings
...
GetLastActivePopup
GetActiveWindow
MessageBoxA
user32.dll
=9@
A9@
CloseHandle
VirtualFree
ReadFile
VirtualAlloc
GetFileSize
CreateFileA
ResumeThread
SetThreadContext
WriteProcessMemory
VirtualAllocEx
GetProcAddress
GetModuleHandleA
ReadProcessMemory
GetThreadContext
CreateProcessA
FreeResource
SizeofResource
LockResource
LoadResource
FindResourceA
GetSystemDirectoryA
Sleep
KERNEL32.dll
GetCommandLineA
GetVersion
ExitProcess
TerminateProcess
GetCurrentProcess
UnhandledExceptionFilter
GetModuleFileNameA
FreeEnvironmentStringsA
FreeEnvironmentStringsW
WideCharToMultiByte
GetEnvironmentStrings
GetEnvironmentStringsW
SetHandleCount
GetStdHandle
GetFileType
GetStartupInfoA
HeapDestroy
HeapCreate
HeapFree
RtlUnwind
WriteFile
HeapAlloc
GetCPInfo
GetACP
GetOEMCP
HeapReAlloc
LoadLibraryA
MultiByteToWideChar
LCMapStringA
LCMapStringW
GetStringTypeA
GetStringTypeW
h-@
\svchost.exe
NtUnmapViewOfSection
ntdll.dll
UNICODE
LOCALIZATION
...
From the the imports and strings VirtualFree, VirtualAlloc, ResumeThread, SetThreadContext, WriteProcessMemory, VirtualAllocEx, GetProcAddress, ReadProcessMemory, GetThreadContext, CreateProcessA we can guess that this is a shellcode injection. And this shellcode is found in .rsrc. FreeResource, SizeofResource, LockResource, LoadResource, FindResourceA. Also I think that the shellcode is going to be injected in svchost.exe All of this are just some guess from imports and strings.
So lets check Resource Hacker make sure that our guess about a shellcode found in .rsrc is right :-
Packed or Not
I don’t think it is packed but lets check PeID,EXE Info and DIE :-
PeID and other tools didn’t detect that it is packed.
Thats enough for Basic Static Analysis.
Basic Static Analysis
I opened ProcMon and ProcExp so lets run the EXE and see what happens :-
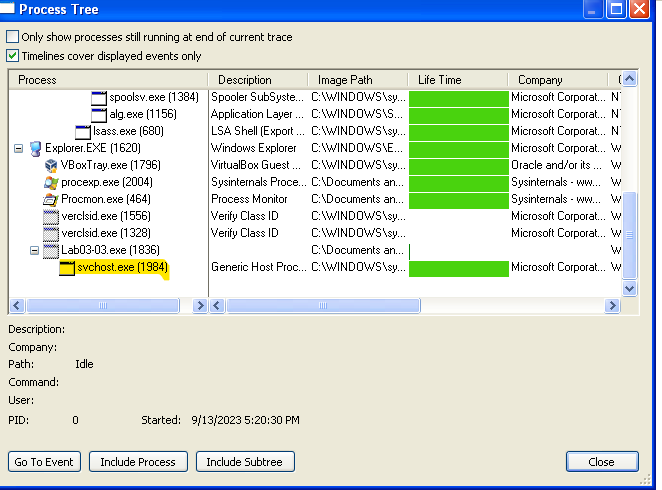
As you can see Lab3-03.exe created a child process which is svchost.exe then exits. For the first glance i thought it was a shellcode injection until I compared the image string with memory string and realized that they are completely different and this is a process replacement
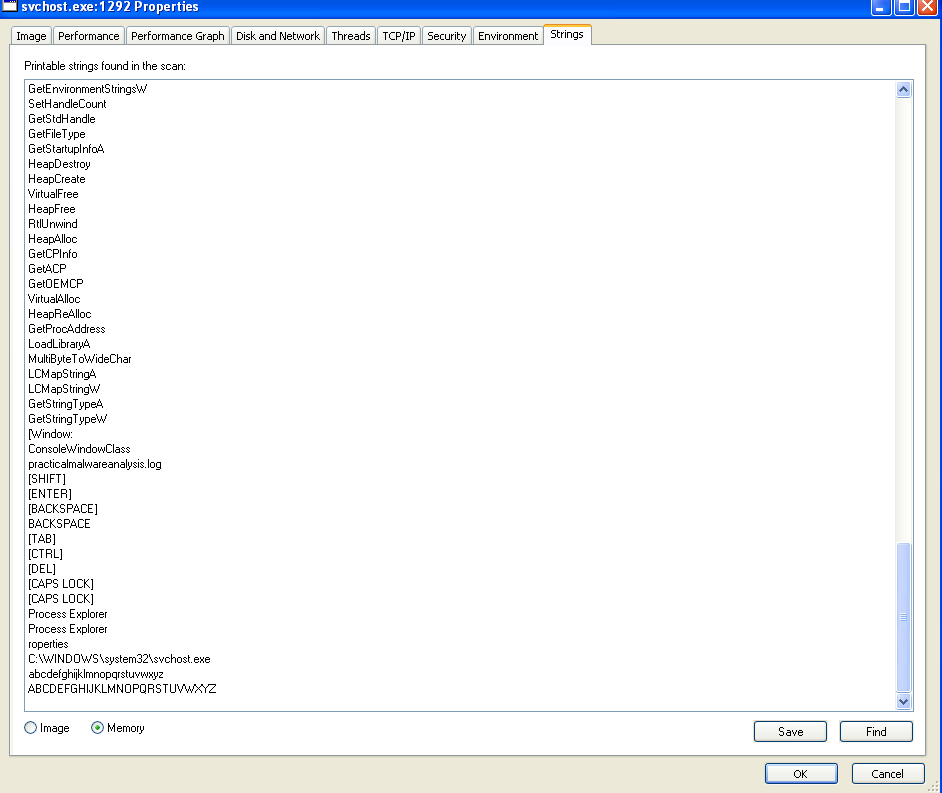
Also the strings found are used in keyloggers mainly and the data are saved in the log file “[SHIFT] , [ENTER] ,[BACKSPACE] ,BACKSPACE , [TAB] , practicalmalwareanalysis.log ….”
So lets get back to ProcMon and see what are the created files :-
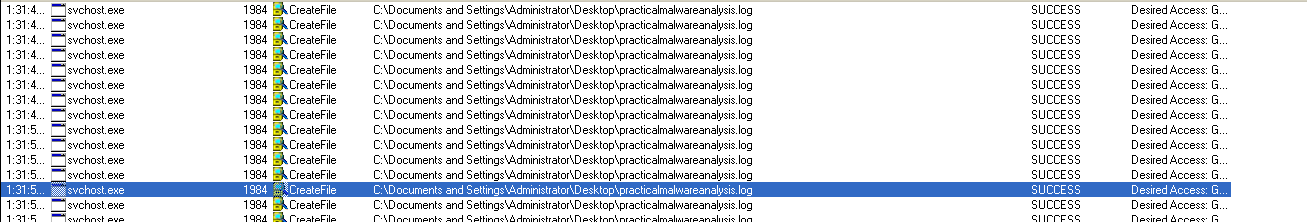
as we can see practicalmalwareanalysis.log is created at the desktop and when we opened the log file it contains every thing I typed by the keyboard :-
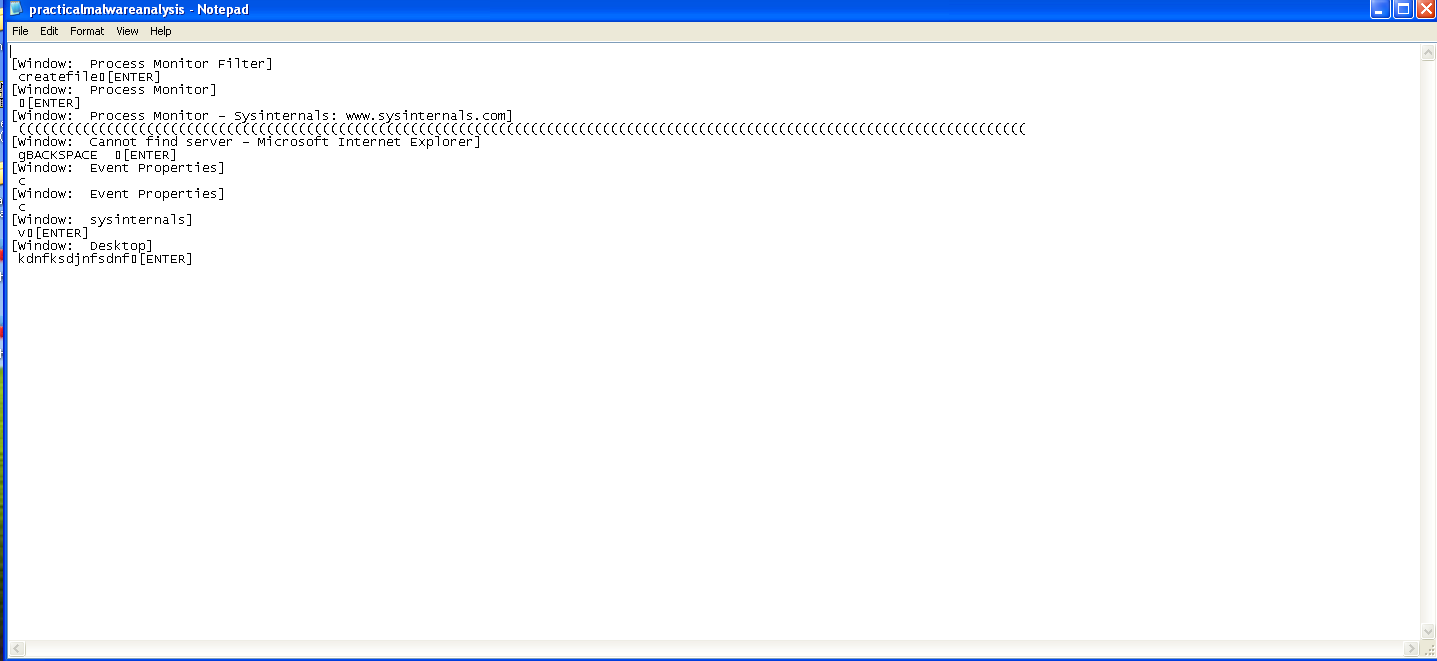
Now we know what our malware dose it is keylogger but it is not exfiltrating the log file. Lets answer the questions
Questions
- What do you notice when monitoring this malware with Process Explorer?
- Lab3-03.exe created a child process svchost.exe then exits leaving svchost.exe as an orphan process
- Can you identify any live memory modifications?
- from static analysis i thought it was a shellcode injection but when analyzing and comparing svchost.exe image string with memory string actually this is a process replacement
- What are the malware’s host-based indicators?
- Running svchost.exe as a non-service
- practicalmalwareanalysis.log
- What is the purpose of this program?
- it uses process replacement for privilege escalation to launch a keylogger
Lab 4
SHA256 Hash
Lab03-03.exe -> 6ac06dfa543dca43327d55a61d0aaed25f3c90cce791e0555e3e306d47107859
Architecture -> 32 bit
Basic Static Analysis
VirusTotal
Looks like it is Malicious as shown below :-
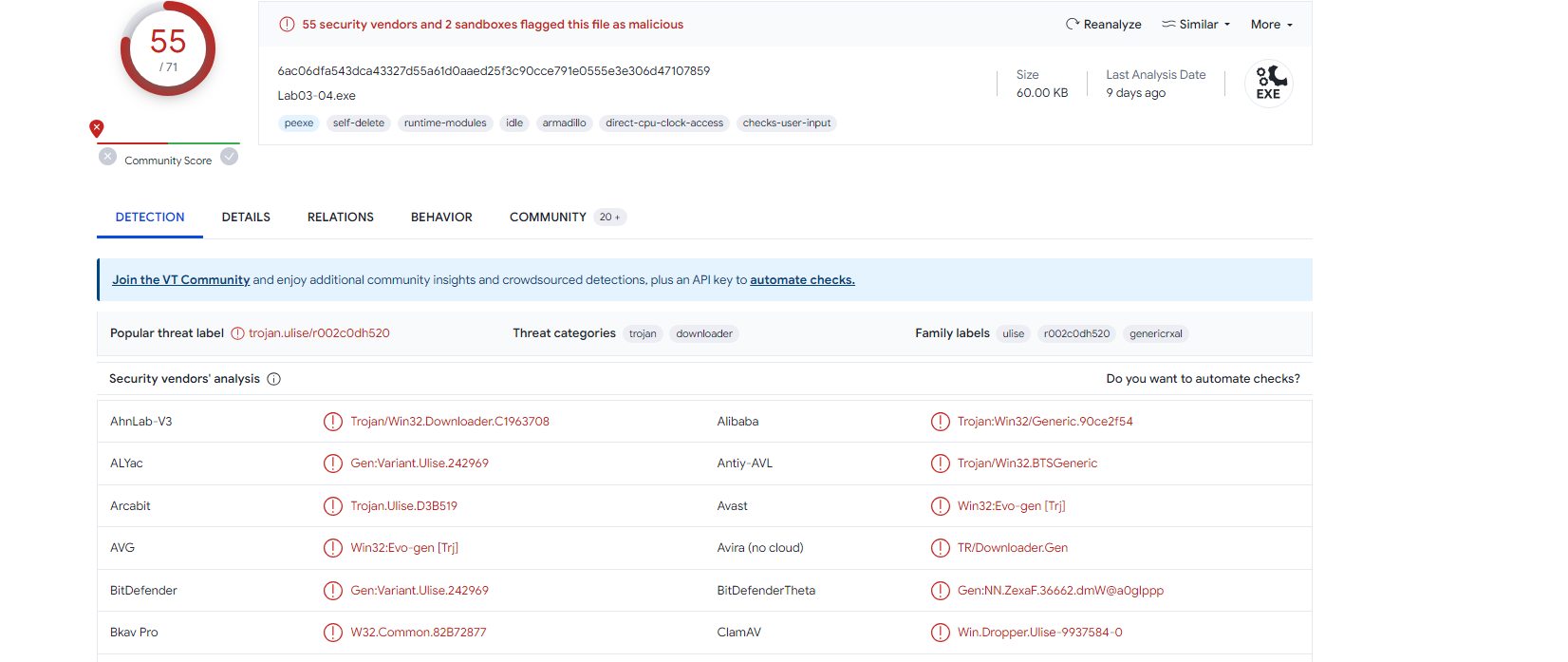
Strings
.com
.bat
.cmd
GetLastActivePopup
GetActiveWindow
MessageBoxA
user32.dll
PATH
CloseHandle
SetFileTime
GetFileTime
CreateFileA
GetSystemDirectoryA
GetLastError
ReadFile
WriteFile
Sleep
GetShortPathNameA
GetModuleFileNameA
CopyFileA
ExpandEnvironmentStringsA
DeleteFileA
KERNEL32.dll
RegQueryValueExA
RegOpenKeyExA
RegSetValueExA
RegCreateKeyExA
RegDeleteValueA
CreateServiceA
CloseServiceHandle
ChangeServiceConfigA
OpenServiceA
OpenSCManagerA
DeleteService
ADVAPI32.dll
ShellExecuteA
SHELL32.dll
WS2_32.dll
ExitProcess
TerminateProcess
GetCurrentProcess
GetTimeZoneInformation
GetSystemTime
GetLocalTime
DuplicateHandle
GetCommandLineA
GetVersion
SetStdHandle
GetFileType
SetHandleCount
GetStdHandle
GetStartupInfoA
CreatePipe
GetExitCodeProcess
WaitForSingleObject
HeapReAlloc
HeapAlloc
GetCPInfo
GetACP
GetOEMCP
UnhandledExceptionFilter
FreeEnvironmentStringsA
FreeEnvironmentStringsW
WideCharToMultiByte
GetEnvironmentStrings
GetEnvironmentStringsW
GetModuleHandleA
GetEnvironmentVariableA
GetVersionExA
HeapDestroy
HeapCreate
VirtualFree
HeapFree
RtlUnwind
MultiByteToWideChar
GetStringTypeA
GetStringTypeW
SetFilePointer
VirtualAlloc
LCMapStringA
LCMapStringW
GetProcAddress
LoadLibraryA
FlushFileBuffers
GetFileAttributesA
CreateProcessA
CompareStringA
CompareStringW
SetEnvironmentVariableA
lZ@
Configuration
SOFTWARE\Microsoft \XPS
\kernel32.dll
HTTP/1.0
GET
'`'`'
`'`'`
NOTHING
CMD
DOWNLOAD
UPLOAD
SLEEP
cmd.exe
>> NUL
/c del
ups
http://www.practicalmalwareanalysis.com
Manager Service
.exe
%SYSTEMROOT%\system32\
k:%s h:%s p:%s per:%s
-cc
-re
-in
From string we can see that the malware can read, write, create and copy files also it looks like it going to add a REG key and will add a service it can also delete a service and it will execute cmd.exe and maybe it is going to create a child process .The most important thing looks like it is going to download and upload to http://www.practicalmalwareanalysis.com using -in, -re, -cc commands.That is a behavior of a HTTP backdoor malware.
Packed or Not
I am sure that it is not packed but lets check :
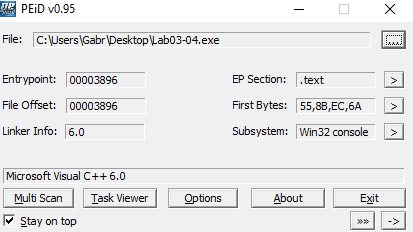
Thats enough for the Basic Static Analysis.
Basic Static Analysis
So lets get InetSim and WireShark ready at Remnux and ProcMon and ProcExp at our Windows XP. So lets run the malware and see what happens:-
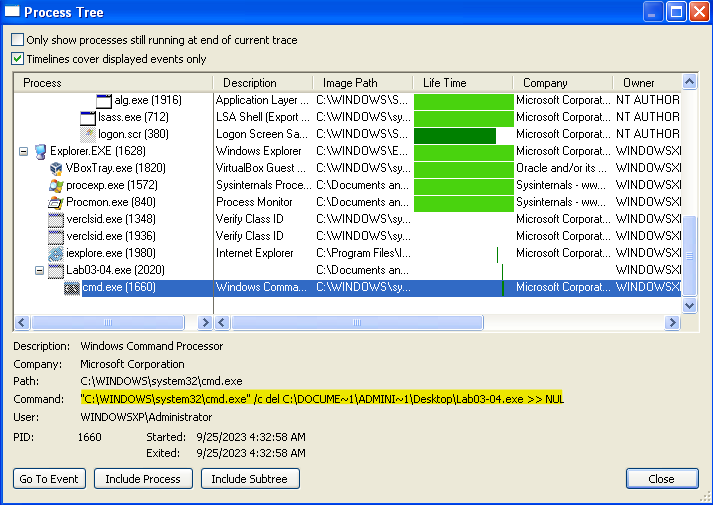
As we can see that Lab3-04.exe created a cmd.exe child process with the following arguments /c del C:\DOCUME~1\ADMINI~1\Desktop\Lab03-04.exe » NUL which means it is going to delete Lab3-04.exe.
Still don’t know why Lab3-03.exe did it detect that it is being monitored. I filletered ProcMon with CreateFile, RegSetValue but didn’t find any thing interesting. The most important thing that it didn’t create any network activity that means it detected it is being monitored and deleted it self. Lets find how it did so and how to run it :-
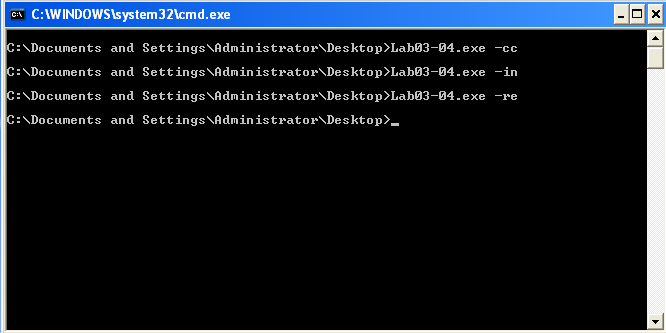
I tried to run it with every possible argument that I found in strings but still deletes itself so after reading the writeup in the book it says we will analyze this sample in chapter 9
Questions
- What happens when you run this file?
- It creates a cmd.exe child process which will delete the file (Lab3-4.exe)
- What is causing the roadblock in dynamic analysis?
- still can’t answer this question but I think there is a detection mechanism or maybe an argument is used to run it need advanced analysis
- Are there other ways to run this program?
- We need to do Advanced Analysis to know how to run the program
