Chapter 1 : Basic Static Analysis
Chapter 1 : Basic Static Analysis
1- Lab 1-1
SHA256 Hash :-
Lab01-1.exe -> 58898bd42c5bd3bf9b1389f0eee5b39cd59180e8370eb9ea838a0b327bd6fe47
Lab01-1.dll -> f50e42c8dfaab649bde0398867e930b86c2a599e8db83b8260393082268f2dba
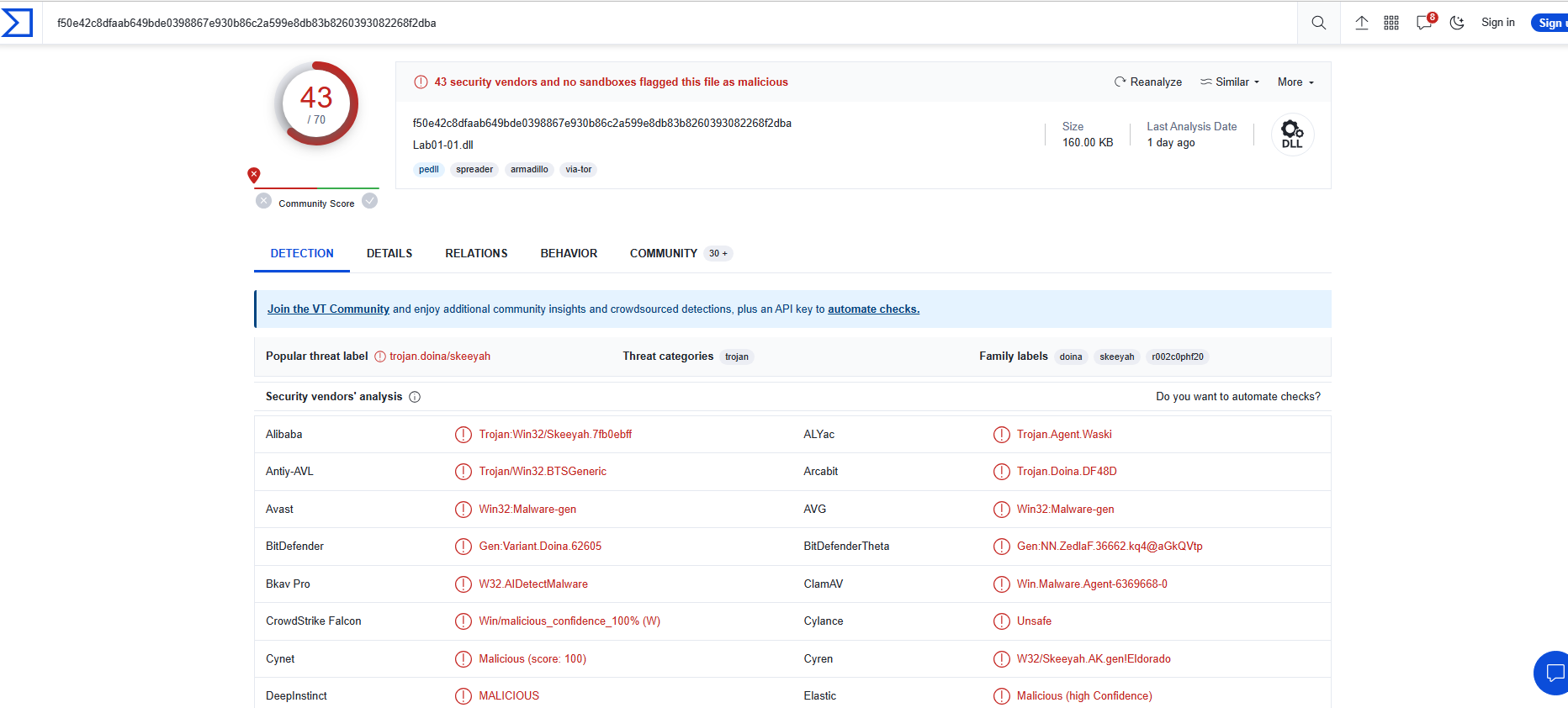
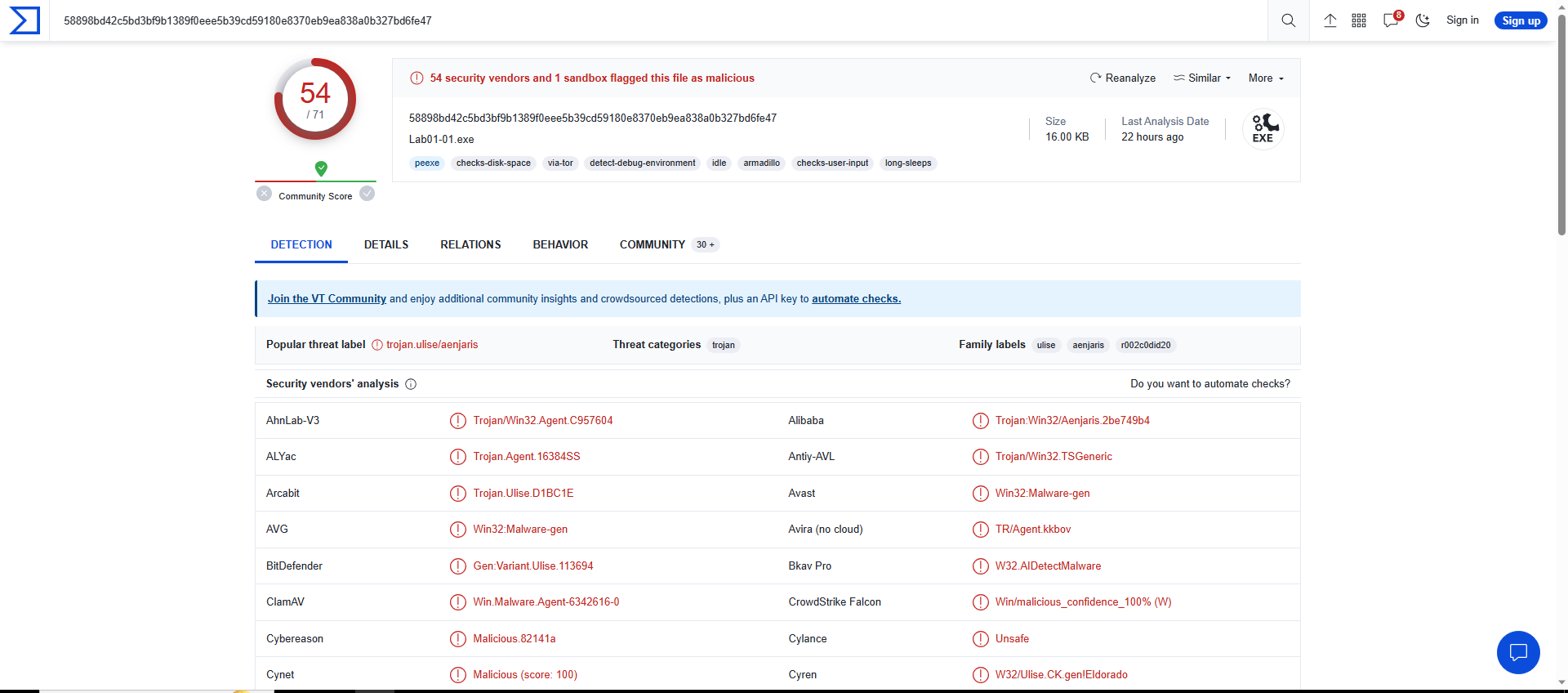
So first of all lets check both file in VirusTotal for Lab01-1.exe :-
Lab01-1.dll
As we can see both of them are malicious files. Lets see the strings of Lab01-01.exe :-
CloseHandle
UnmapViewOfFile
IsBadReadPtr
MapViewOfFile
CreateFileMappingA
CreateFileA
FindClose
FindNextFileA
FindFirstFileA
CopyFileA
KERNEL32.dll
malloc
exit
MSVCRT.dll
kerne132.dll
kernel32.dll
.exe
C:\*
C:\windows\system32\kerne132.dll
Kernel32.
Lab01-01.dll
C:\Windows\System32\Kernel32.dll
- The strings aren’t much but is enough for exe to work
- From the imports of KERNEL32.dll (CreateFileA, FindClose, FindNextFileA, FindFirstFileA, CopyFileA) looks like it is copies files and searching for files
strings of Lab01-1.dll :-
CloseHandle
Sleep
CreateProcessA
CreateMutexA
OpenMutexA
KERNEL32.dll
WS2_32.dll
strncmp
MSVCRT.dll
exec
sleep
hello
127.26.152.13
- From the imports of KERNEL32.dll (Sleep, CreateProcessA) :-
- looks like it creates a process
- sleep at specific point
- From WS2_32.dll (Socket, WSAStartup, inet_addr, connect, send, shutdown, recv, closesocket, WSACleanup, htons)
- Looks it is creating a socket connection and data is send and received
Host-based indicators
We can see in Lab01-1.exe C:\windows\system32\kerne132.dll the malware trying to trick us by changing “L” in kernel to “1”
Network indicators
We can see in Lab01-1.dll 127.26.152.13 looks like it is going to create socket connection to this IP addr
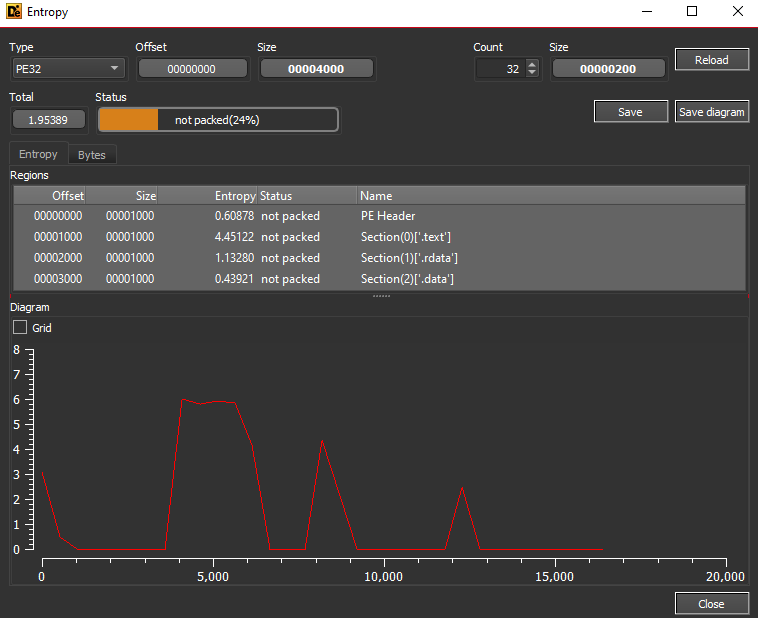
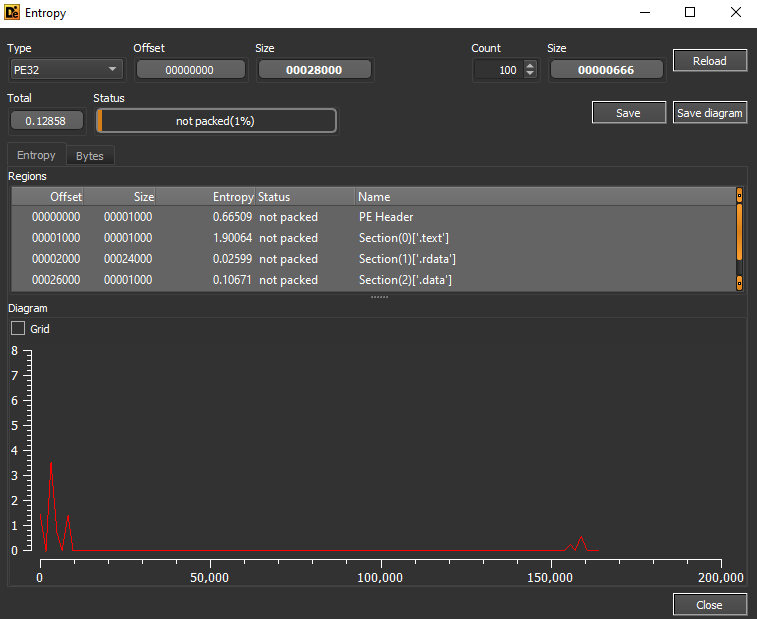
Packed or Not?!
By using DIE :-
- Lab01-1.exe
- Lab01-1.dll
- So it is Not Packed
Questions
-
Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
- Both of them are Malicious as we saw above in the analysis
-
When were these files compiled?
- By using PE-Studio
- Lab01-1.exe -> compiler-stamp,Sun Dec 19 16:16:19 2010
- Lab01-1.exe -> compiler-stamp,Sun Dec 19 16:16:38 2010
- Less than 1 min difference which indicates it is made by the same author
- By using PE-Studio
-
Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
- The strings found aren’t much but it enough and they are not obfuscated as seen above
- Also as seen Above using DIE also you can use PeId
-
Do any imports hint at what this malware does? If so, which imports are they?
- Lab01-1.exe
- From the imports of KERNEL32.dll (CreateFileA, FindClose, FindNextFileA, FindFirstFileA, CopyFileA) looks like it is copies files and searching for files
- Lab01-1.dll
- From the imports of KERNEL32.dll (Sleep, CreateProcessA) :-
- looks like it creates a process
- sleep at specific point
- From WS2_32.dll (Socket, WSAStartup, inet_addr, connect, send, shutdown, recv, closesocket, WSACleanup, htons)
- Looks it is creating a socket connection and data is send and received
- From the imports of KERNEL32.dll (Sleep, CreateProcessA) :-
- Lab01-1.exe
-
Are there any other files or host-based indicators that you could look for on infected systems?
- C:\windows\system32\kerne132.dll
-
What network-based indicators could be used to find this malware on infected machines?
- 127.26.152.13
-
What would you guess is the purpose of these files?
- The .exe is used for searching and coping files also I think it will execute the .dll which is a backdoor as the combination of socket connection with Sleep, CreateProcessA are used at backdoor.
2- Lab 1-2
SHA256 Hash
Lab01-02.exe -> c876a332d7dd8da331cb8eee7ab7bf32752834d4b2b54eaa362674a2a48f64a6
VirusTotal
Lets upload the given exe to VirusTotal :-
-
-
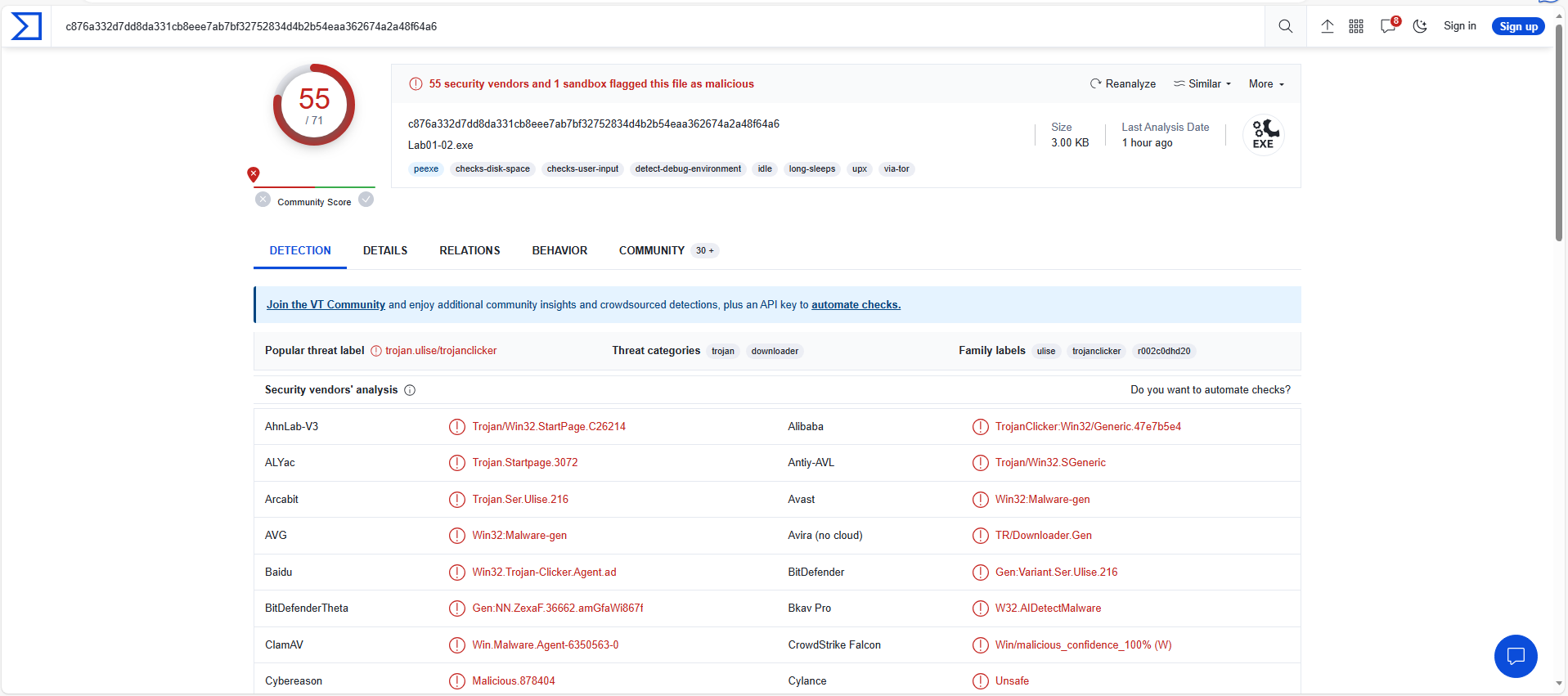
As we can see it is detected as Malicious exe trojan
Strings
UPX0
UPX1
UPX2
3.04
UPX!
MalService
sHGL345
http://w
warean
ysisbook.co
om#Int6net Explo!r 8FEI
*Waitab'r
Process
OpenMu$x
XPTPSW
KERNEL32.DLL
ADVAPI32.dll
MSVCRT.dll
WININET.dll
LoadLibraryA
GetProcAddress
VirtualProtect
VirtualAlloc
VirtualFree
ExitProcess
CreateServiceA
exit
InternetOpenA
- As we can see the no much strings which looks like it is packed
- Also at the beginning we we can see UPX that tells us it is packed by upx
- UPX is easy to unpack :-
upx -d Lab01-02.exe
Strings after unpacking :-
KERNEL32.DLL
ADVAPI32.dll
MSVCRT.dll
WININET.dll
SystemTimeToFileTime
GetModuleFileNameA
CreateWaitableTimerA
ExitProcess
OpenMutexA
SetWaitableTimer
WaitForSingleObject
CreateMutexA
CreateThread
CreateServiceA
StartServiceCtrlDispatcherA
OpenSCManagerA
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
InternetOpenUrlA
InternetOpenA
MalService
Malservice
HGL345
http://www.malwareanalysisbook.com
Internet Explorer 8.0
- (CreateServiceA, StartServiceCtrlDispatcherA, OpenSCManagerA) Looks like the malware is going to create and start a service with the name of MalService
Host-Based Indicators
If MalService found then the device is compromised
Network-Based Indicators
looks like it is going to open this URL with http://www.malwareanalysisbook.com or maybe the MalService will do so
Questions
- Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
- Yes , it does. It is malicious trojan as shown above
- Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
- Yes it is Packed, If we used strings we can see UPX which tells its is packed
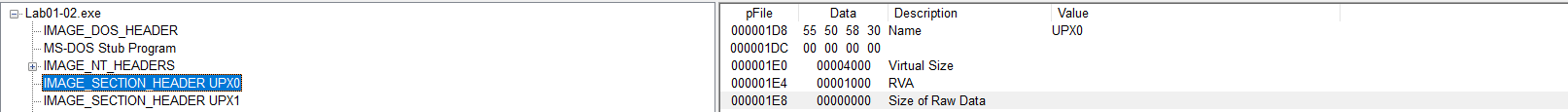
- Using PeView we can see UPX0 section the size of raw data i zero and virtual size is 4000
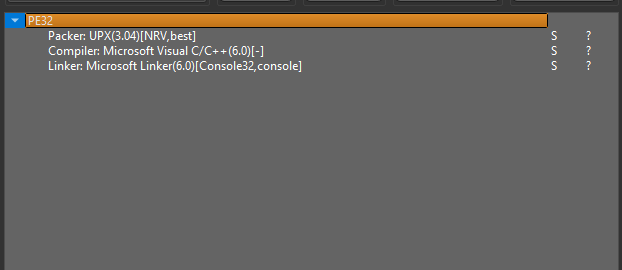
- Also by using DIE or PeID/EXE info PE
-
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
- (CreateServiceA, StartServiceCtrlDispatcherA, OpenSCManagerA) Looks like the malware is going to create and start a service with the name of MalService
-
What host- or network-based indicators could be used to identify this malware on infected machines?
- Host-Based Indicators :-
- MalService
- Network-Based Indicators :-
- http://www.malwareanalysisbook.com
- Host-Based Indicators :-
3- Lab01-03
SHA256 Hash
Lab01-03.exe -> 7983a582939924c70e3da2da80fd3352ebc90de7b8c4c427d484ff4f050f0aec
VirusTotal
Lets upload the exe to VirusTotal :-
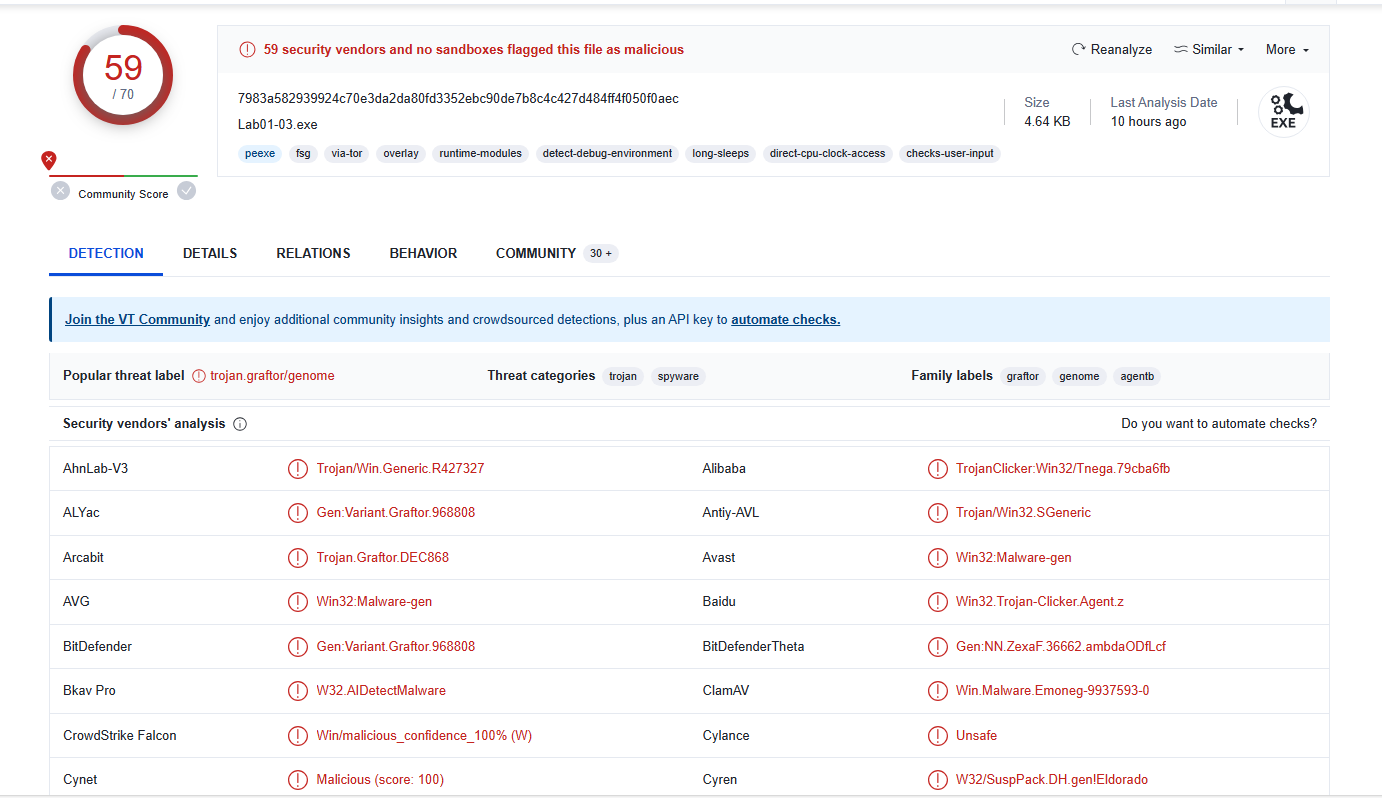
- As we can see it is malicious exe
Strings
...
KERNEL32.dll
LoadLibraryA
GetProcAddress
...
- Can’t find useful strings which for sure indicates that it is packed as LoadLibraryA, GetProcAddress usually used in packing
Packed or Not
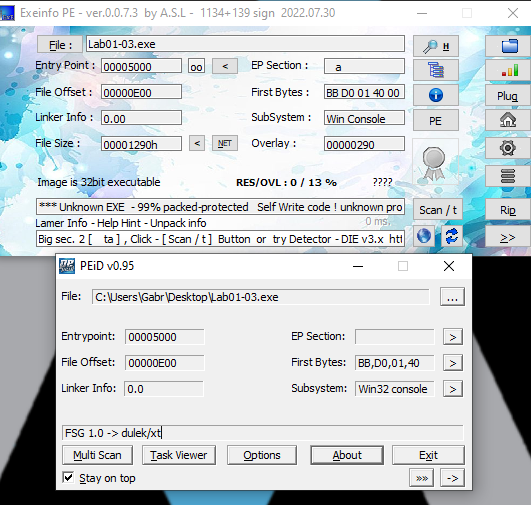
As we have seen above there no thing useful in strings lets use PeView or PeStudio (I used PeStudio) to find if it is packed or not :-
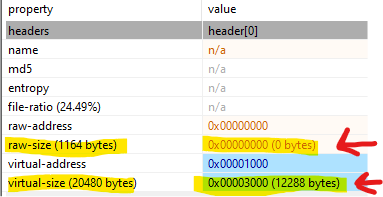
- We can see that header[0] section is responsible fro the packing
- EXE Info PE didn’t detect the packer type but PeID did:-
Questions
- Upload the Lab01-03.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
- As seen above it is a malicious exe
- Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
- Yes, first of all there is no useful strings except LoadLibraryA, GetProcAddress which usually used in packing
- Also by using PeId as seen Above
- Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
- LoadLibraryA, GetProcAddress which usually used in packing but it is hard to tell what is the functionality of the program
- What host- or network-based indicators could be used to identify this malware on infected machines?
- Can’t get any information because the malware is packed
4- Lab01-04
SHA256 Hash
Lab01-04.exe -> 0fa1498340fca6c562cfa389ad3e93395f44c72fd128d7ba08579a69aaf3b126
VirusTotal
Lets upload the exe to VirusTotal :-
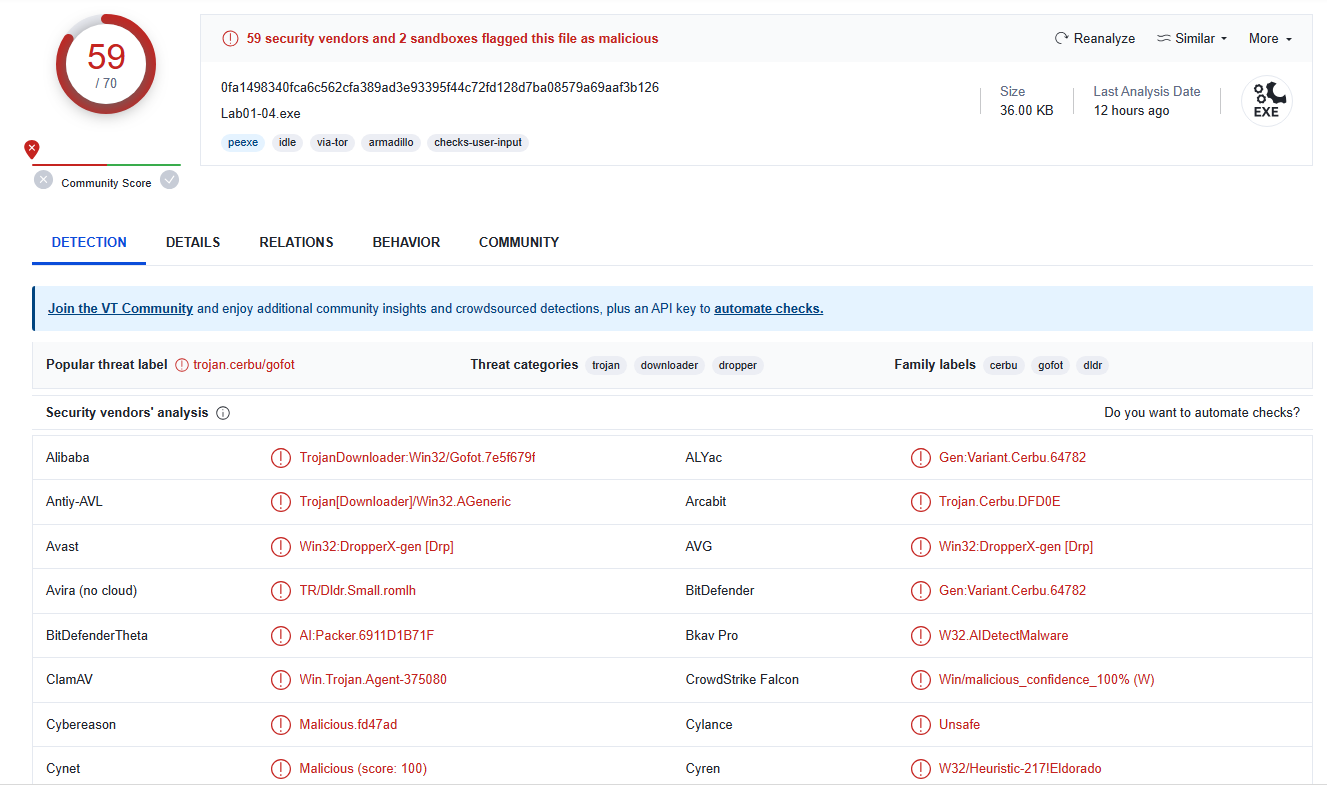
- As we can see it is malicious exe
Strings
!This program cannot be run in DOS mode.
Rich
.text
`.rdata
@.data
.rsrc
CloseHandle
OpenProcess
GetCurrentProcess
CreateRemoteThread
GetProcAddress
LoadLibraryA
WinExec
WriteFile
CreateFileA
SizeofResource
LoadResource
FindResourceA
GetModuleHandleA
GetWindowsDirectoryA
MoveFileA
GetTempPathA
KERNEL32.dll
AdjustTokenPrivileges
LookupPrivilegeValueA
OpenProcessToken
ADVAPI32.dll
_snprintf
MSVCRT.dll
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
_stricmp
winlogon.exe
<not real>
SeDebugPrivilege
sfc_os.dll
\system32\wupdmgr.exe
%s%s
BIN
#101
EnumProcessModules
psapi.dll
GetModuleBaseNameA
psapi.dll
EnumProcesses
psapi.dll
\system32\wupdmgr.exe
%s%s
\winup.exe
%s%s
BIN
!This program cannot be run in DOS mode.
Rich
.text
`.rdata
@.data
GetWindowsDirectoryA
WinExec
GetTempPathA
KERNEL32.dll
URLDownloadToFileA
urlmon.dll
_snprintf
MSVCRT.dll
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
\winup.exe
%s%s
\system32\wupdmgrd.exe
%s%s
http://www.practicalmalwareanalysis.com/updater.exe
- WAIT WHAT !!! Looks like this exe has another exe embedded inside it looks like it is a Loader Malware lets try to understand what is happening here (We can use resource hacker to dump the exe):-
- AdjustTokenPrivilegesو LookupPrivilegeValueAو OpenProcessToken, SeDebugPrivilege Looks like it is going evolve the privilege to SeDebugPrivilege
- SeDebugPrivilege particularly important for debugging and system analysis tools. Processes with this privilege can do the following:
- Debug other processes
- Access system information
- Bypass security restrictions:
- Looks like it is going to dump the embedded exe and then execute it by the help of WinExec, WriteFile, CreateFileA
- Also looks like it is going to download update.exe from http://www.practicalmalwareanalysis.com/updater.exe by the help of the URLDownloadToFileA
- SizeofResource, LoadResource, FindResourceA indicates that data is being loaded form resource section
Packed or Not
Form the first glance it is nether packed nor obfuscated you can use EXE info Pe or PeID to make sure
Host-Based indicators
\winup.exe
\system32\wupdmgrd.exe
\system32\wupdmgr.exe
- Maybe it is going to do something to both EXE
Network-Based indicators
http://www.practicalmalwareanalysis.com/updater.exe
Questions
- Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
- Yes, it is detected as a malicious EXE
- Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
- No it is not packed the strings gives lots of information about the EXE
- When was this program compiled?
- Fri Aug 30 22:26:59 2019
- Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
- Looks like it is going to dump the embedded exe and then execute it by the help of WinExec, WriteFile, CreateFileA
- AdjustTokenPrivilegesو LookupPrivilegeValueAو OpenProcessToken, SeDebugPrivilege Looks like it is going evolve the privilege to SeDebugPrivilege
- Also looks like it is going to download update.exe from http://www.practicalmalwareanalysis.com/updater.exe by the help of the URLDownloadToFileA
-
SizeofResource, LoadResource, FindResourceA indicates that data is being loaded form resource section
- What host- or network-based indicators could be used to identify this malware on infected machines?
- Host-Based indicators
- \system32\wupdmgrd.exe
- winup.exe
- \system32\wupdmgr.exe
- Netowk-Based indicator
- http://www.practicalmalwareanalysis.com/updater.exe
- Host-Based indicators
- This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource
- after dumping the embedded EXE it s downloader that looks like it is going to download 2nd stage Malware